Security Tools - New and Updated
Over the past several months, I've been busy with various projects and helping others with their analysis and in the process, whipped up a couple of new tools to share. I hope you find them to be useful. These have been tested on Windows XP and 7. When dealing with live malware, be sure you take the necessary precautions like using a virtualized environment. No warranties, use at your own risk.
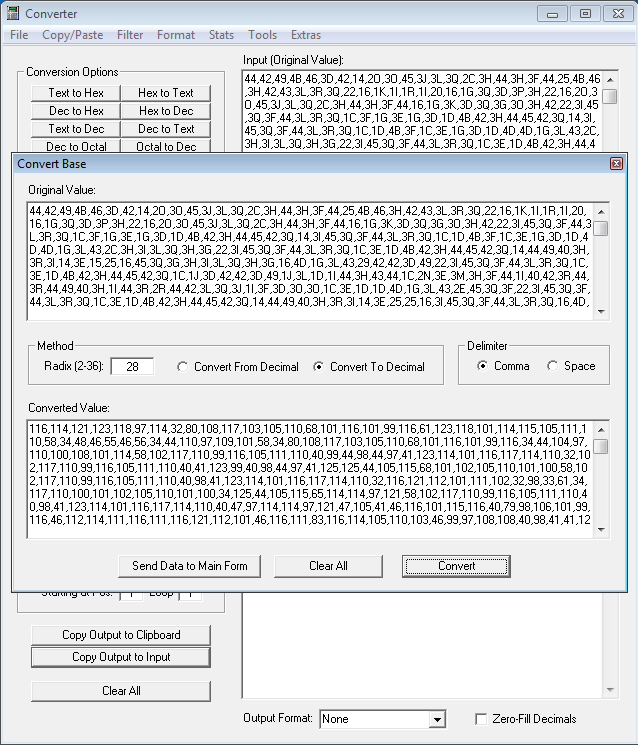
Converter v0.4
Some bug fixes and minor updates were made:
* "Convert Base" feature has been expanded to enable you to convert from/to decimal values separated by commas or spaces. Single-value conversions still work.* The "Convert Custom Base64" feature now lets you convert to hex as well as text.
* Replaced the "XOR Encrypt/Decrypt" feature with "Key Search/Convert" that allows you to do XOR, ROTate, or ShiFT searches and conversions from/to text, hex, or comma-separated decimal values (see Data Converter below).
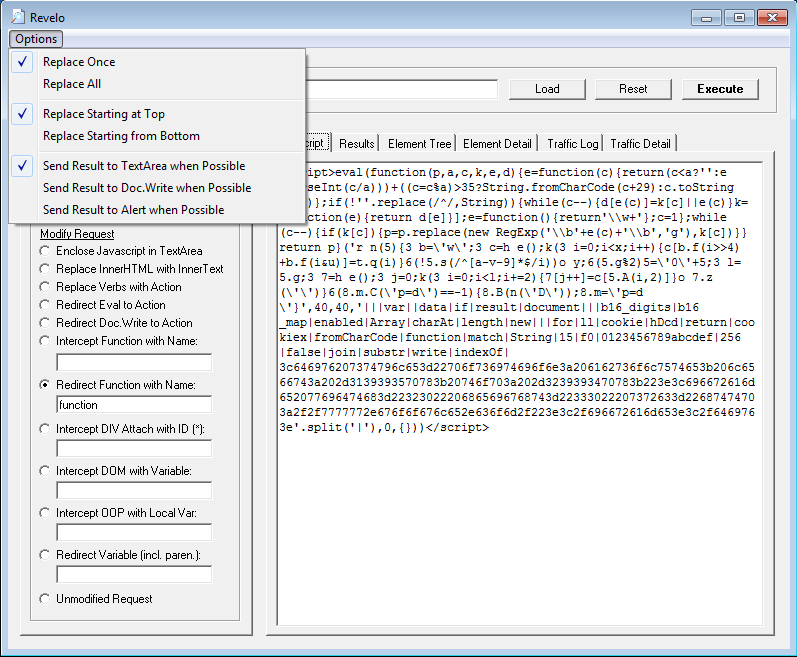
Revelo v0.5
I fixed some bugs and added a new method called "Redirect Function with Name". What this allows you to do is redirect a function to an outside script that displays the contents of the eval'd function. As an example, here we see a compressed script. We select the method, enter the word "function", and set the option to "Replace Starting at Top" to make sure we catch the first topmost instance then click on "Execute". The results appear on the Results tab.
What's going on behind-the-scenes is that Revelo modifies the script from this:
<script>eval(function(p,a,c,k,e,d)...To this:
<script>eval(zyxyz=function(p,a,c,k,e,d)...Then adds this to the end:
<script>alert(zyxyz);</script>I also added the ability to do these replacements just once instead of doing it for all matches.
PHP Converter
This tool really did not need to be made but I was asked by a friend to come up with an easy way to handle obfuscated PHP files found on compromised hosts for a non-PHP, security newbie. The best option is really to learn PHP and have Portable XAMPP (or similar) on-hand.
To "deobfuscate", choose the nested options from inside-out.
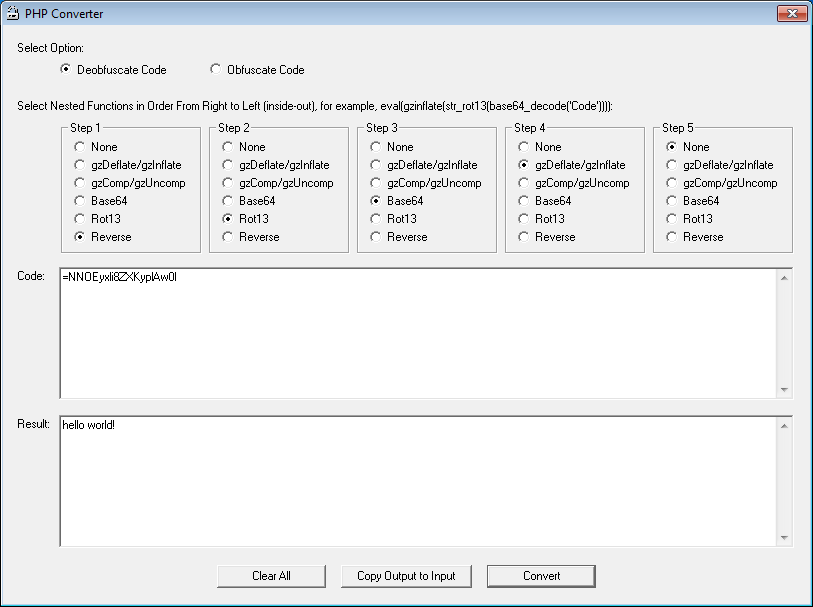
To "obfuscate" text, choose the nested options from outside-in. Credit to James Johnston of TechKnow Professional Services. This program also contains cryptography software by David Ireland of DI Management Services Pty Ltd
Data Converter
I've been coming across Java applets using XOR encryption for awhile now. Using a debugger like Eclipse is the way to go but sometimes I find that I just want to get an idea of what's going on so I whipped up this quick and dirty tool.
This program allows you to take in text, hexcode, or decimal values delimited using comma separation. The key and output format can be any of the three as well. You can choose the XOR, ROTate, or ShiFT method and the action can be single (same key for the entire run), sequential (converts the input using the first key, runs through it again using the second key, etc), and consecutive (loops through each of the keys for the length of the input).
Here's an example taken from a malicious Java applet:
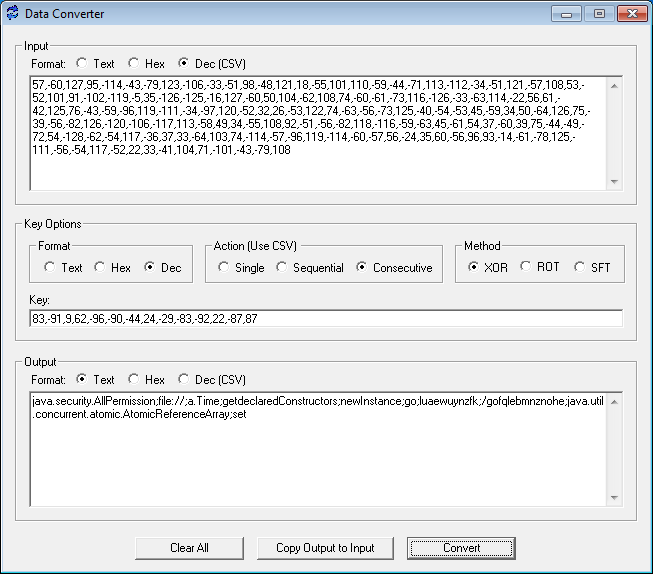
This program is now part of Converter but you can download this separately if you want.
Sandbox Tester
I needed to test an automated sandbox analysis tool. Without getting too fancy or sophisticated I came up with several methods to get my test malware through. I eventually came up with just over a dozen methods but this program incorporates only four of those methods. To prevent abuse, you can't select your own binary to drop. Sorry!
First choose your drop location, add a drop delay value in seconds (set it to 0 for no delay), and the name of the drop file.
The "Name Check" option checks to see if the name of the drop file has changed. If so, the dropper will quit without doing anything. The "Loc Check" checks to see if the location of the drop file is not "c:\documents and settings\" or "c:\users\". If yes, then the dropper will quit.
If you choose the "Mouse Aware" option then the dropper watches the mouse to see if it moves within the drop delay time. If not then the program quits. If you choose a short delay value then it may not give the dropper enough time to check for movement so bear that in mind.
The last option is "Active Window". If the dropper sees that the menubar or desktop is in the foreground (top-most window), the program quits. Again, you may need to up the delay value to give enough time to check for user activity.
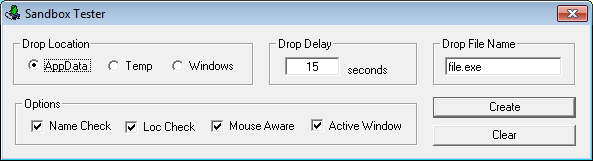
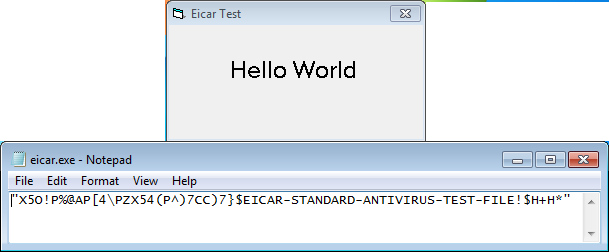
When you make your selections and click on "Create" then this program creates the dropper. This is what you upload to the sandbox. When the sandbox executes the dropper then an executable is dropped into the location you specified, waits a number of seconds (if applicable), then pops up a "Hello World" message and drops an .EXE file to the current path. That file is actually just a text file that contains the Eicar string.