Flash Used in Idol Malvertisement
As the American Idol finale approaches, millions of people are keeping an eye on the results. So what better time to launch a new malvertisement campaign! This one can be found on a popular idol fan page.
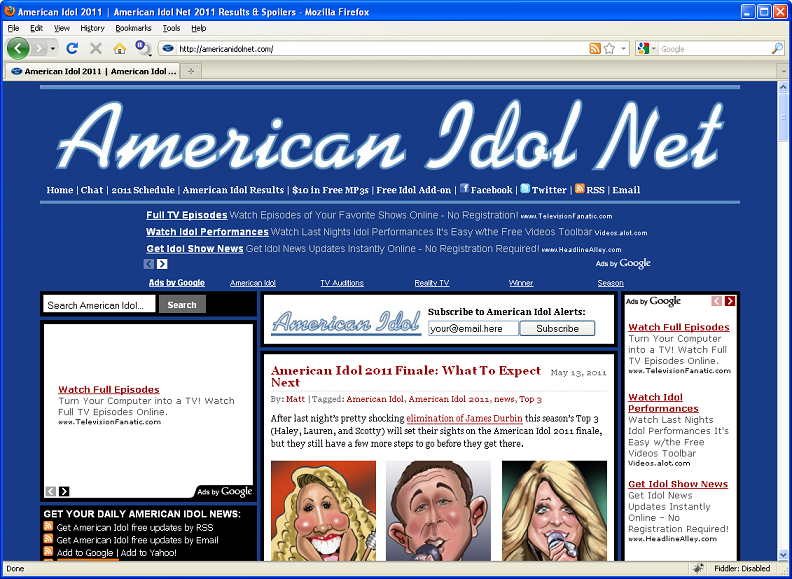
If you visit the site directly, everything acts normally. It’s when you arrive on the site via a search engine does it turn ugly on you.
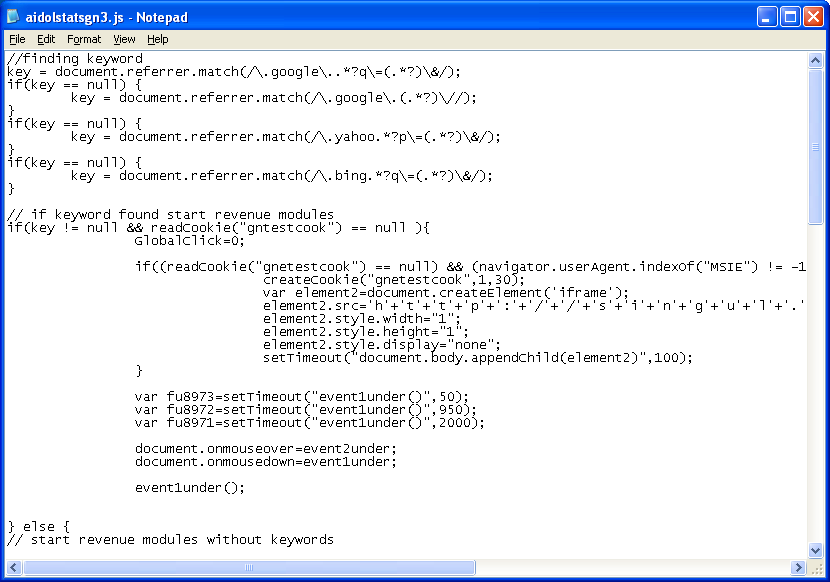
Here we see that one of the files checks where you came from. It also looks at your browser and cookies.
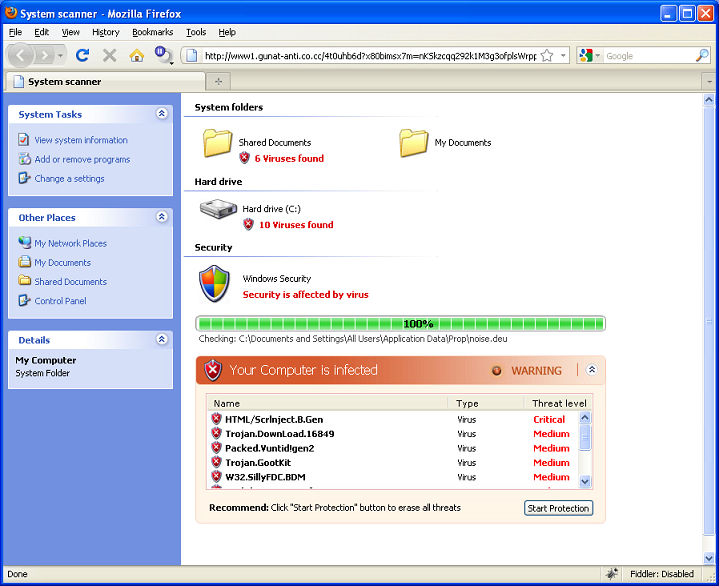
Trying to find the actual source of the rogueware link can be a bit of a challenge. I looked at every relevant file but couldn’t find it. Here’s the chain of events I had so far:
hxxp://americanidolnet[.]com/hxxp://partner[.]googleadservices[.]com/gampad/google_service.jshxxp://pubads[.]g[.]doubleclick[.]net/gampad/ads?correlator=1305321989351…*** missing link ***hxxp://adserver-cdn2[.]com/ts/go.php?sid=1006hxxp://adserver-cdn2[.]com/ts/geoipcity/cred_aidol.phphxxp://adserver-cdn2[.]com/aidolstatsgn3.jshxxp://singul[.]co[.]cc:81/bl1/hxxp://singul[.]co[.]cc:81/bl1/include/PluginDetect.jshxxp://singul[.]co[.]cc:81/bl1/add_visitor.php?referrer=http://americanidolnet.com/hxxp://www3[.]save-holderjmk[.]cx[.]cc/?edd5a62=m%2Bzgl2ullKmWU9jY0K…hxxp://www1[.]addprotectionte[.]vv[.]cc/28zguc6f?57opfyp…hxxp://www1[.]addprotectionte[.]vv[.]cc/24512f4.jsThe last thing to check was a Flash file at:
hxxp://adserver-cdn2[.]com/grepolis_aidol_160x600.swfI decompiled it and what do you know…
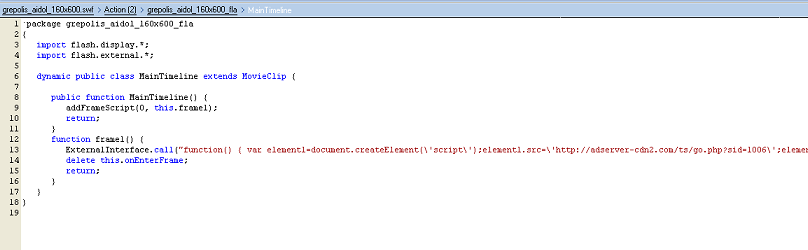
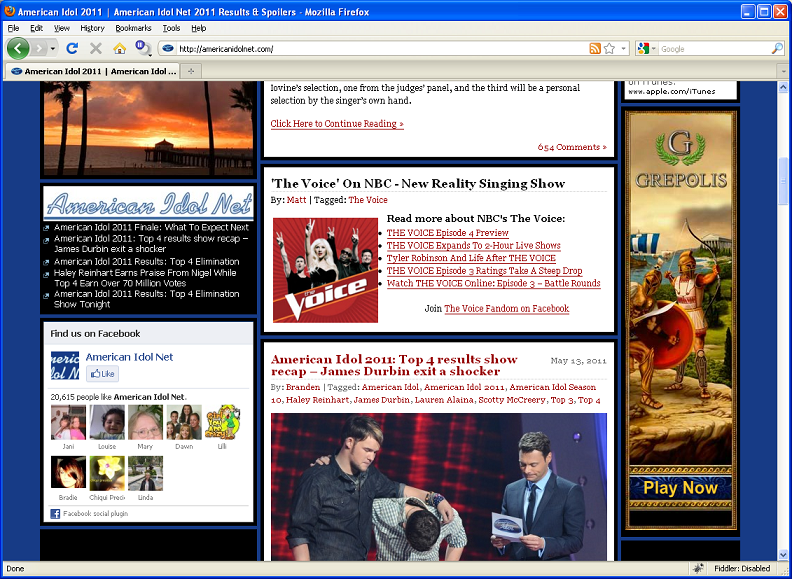
Looking back at the website about a fifth of the way down, the vertical Flash ad for “Grepolis” is the missing link.
One thing that caught my eye was the “bl” directory name on the co.cc server. Bleeding Life exploit kit? Sure looks like it…