Exploit Packs and the Secret Decoder Ring
If you've ever analyzed an exploit pack, you will often see a string of strange characters as parameters to a Java applet. You might have even noticed a certain pattern suggesting that this isn't random characters. Here's what I'm talking about; have a look at the parameter values for Black Hole:
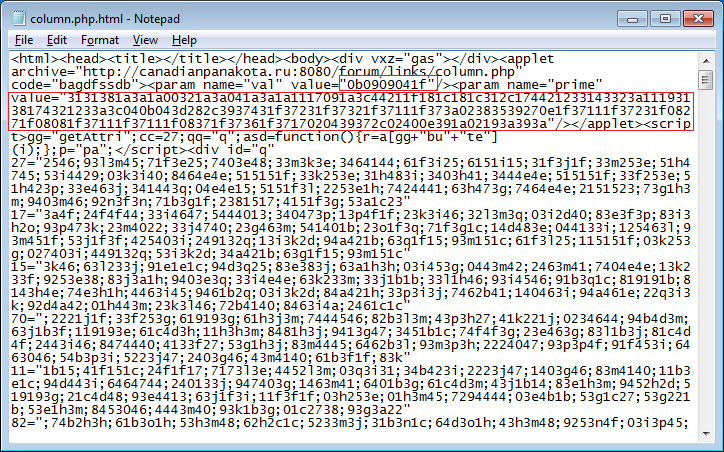
In a version of Black Hole early in the month, you could find this in the HTTP request generated by the Java applet itself:
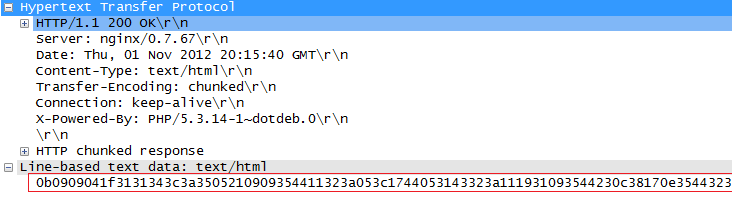
These strings are the URLs of the payload obscured using a secret decoder so to speak. Every two characters is a byte that represents a position in a key. If you extract the results from the key and concatenate them, you'll have the URL.
What's the key? Each author or exploit pack version could have its own unique key but we can try to figure out what the key is; we just have to work in reverse. I wrote a program that might be of some help so let's try this out on Black Hole version 2.
First we have to obtain this string of encoded characters and the URL of the payload. I've done a little Wiresharking that yielded the following:

I've pasted the values in the program and set it to "Position Lookup", two-character formatting with a hex type:
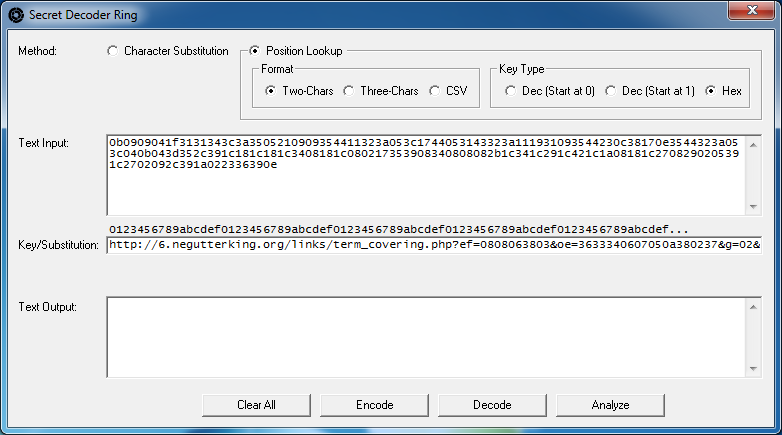
If you press the "Analyze" button right now, it will tell you that the output field is empty (it needs to have a starting string to build off of) so the program will then insert a string of ` characters for you like so:
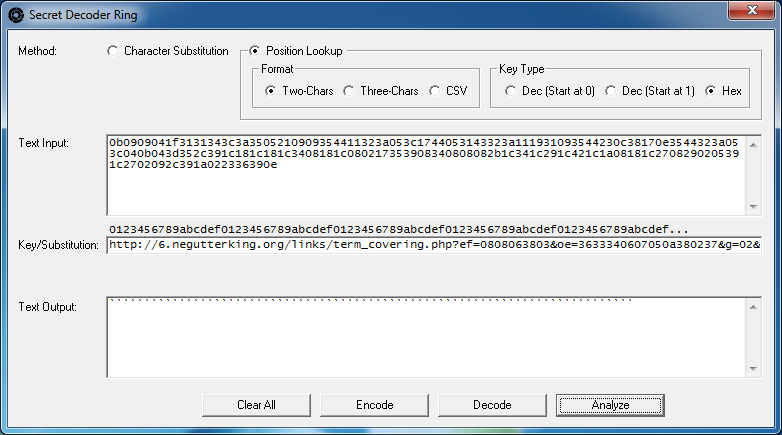
Now press the "Analyze" button once again. It will fill in the positions of the key based on what is known -- the encoded values and the URL.
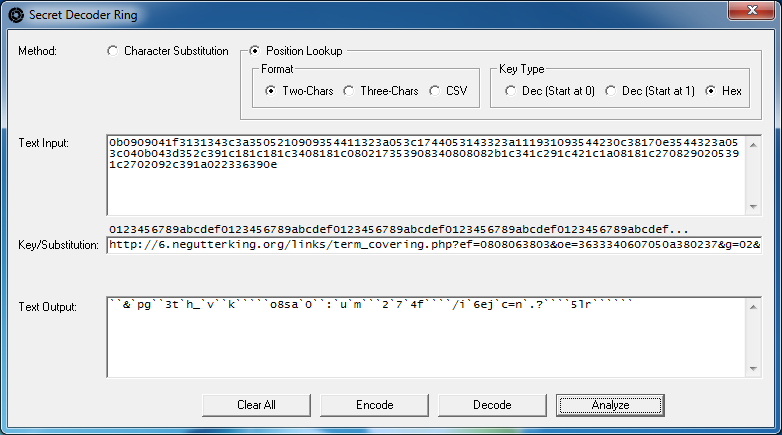
Let's get another set of strings from another instance of Black Hole and put that into the program but this time we leave the output value alone because we want to add to our existing (partial) key.
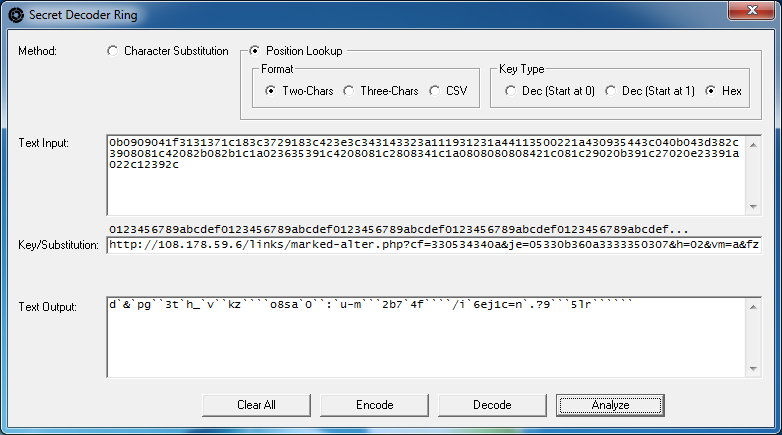
Keep going, trying to find a good mix of characters based off of the payload URL. After a few more, you'll probably end up with this:
dq&`pg``3twh_`v``kz````o8sa`0`y:`u-m```2b7`4f````/i`6ej1c=n`.?9`x`5lr``````The left over ` characters reveal missing values. By counting those up, we can guess that those are upper case characters and a couple more symbols. What we have are all the lower case characters, numbers, and significant symbols which may be enough. Now let's use the key, paste in just the encoded value, and this time click on the "Decode" button:
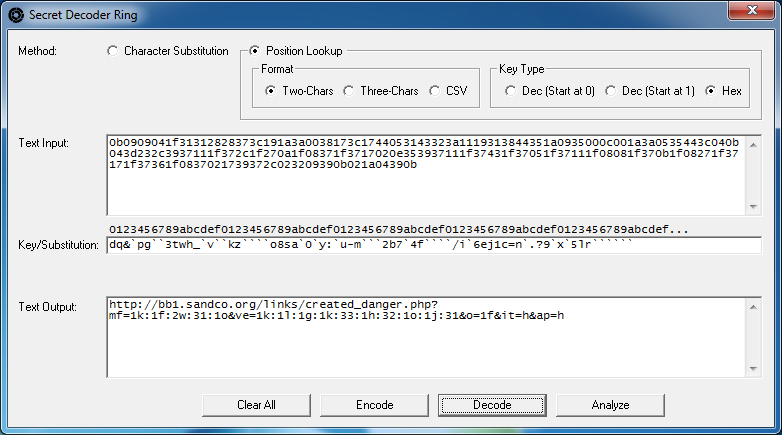
Cool! If you haven't figured out how this position lookup works, the above graphic should make it more clear. The first two bytes of the encoded value ("text input" field) are "0b". Just above the "Key/Substitution" field are a set of incrementing hex values. Go to position 0x0b and get the character directly underneath it, which is "h". That's the first character of the URL! The next two characters are "09" so go to the 0x09 position and get that character which is "t". Got it?
Now we can use this secret key to find out what the payload URLs are for this variant of Black Hole v2...until the key is changed.
Interestingly, I analyzed a new exploit pack that Kafeine found called Cool Exploit Pack and noticed the same-looking string of encoded characters. I put that into the program using the Black Hole key and guess what...it worked! What's the odds of two exploit pack authors using the same secret decoder?
The program also helps you tackle another type of "encoding method" called character substitution. The program acts a little differently for this method. You will need to enter a "plain text" value. I've already included a common set of URL-related characters but it probably won't work for all cases so you can adjust it as needed. In addition, the length of the "plain text" must match the length of the starting string (all those ` characters) since this is a subtitution cipher after all.
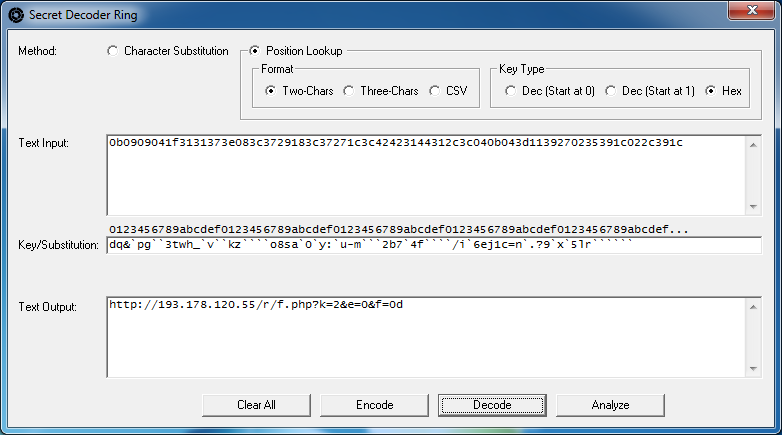
Here we have the payload URL for yet another new exploit pack called CritXPack. We plug this into the fields and click on the "Analyze" button. In this particular substitution cipher, the first character of the encoded string is "d" which corresponds to "h", "X" corresponds to "t", and so on.
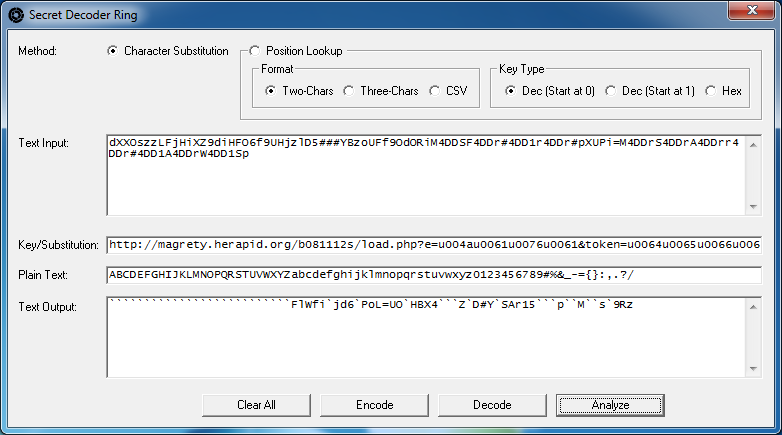
Again, you would find other instances of this exploit pack, collect enough encoded strings and URLs to build up the key until you have all of the useful characters. Then you can keep that key for decoding future CritXPack's payload URLs.
This program is now available on the Tools page.

