CMD Watcher and Maldocs
Having spent a good amount of time analyzing a variety of maldocs, I realized that they had one thing in common. Have a look at this chart below and you might have the same "a-ha" moment I had.

I realized that many of these maldocs use CMD to launch the next stage. Of course, not all maldocs follow this chart. There are some maldocs that make a request to pull down malware directly from VBA (or variants of that) and CMD is not used at all.
So I thought what if I watch for the CMD process and extract the data from the command line. Then I could get the deobfuscated output from the VBA macro without having to trace through the code and dump the content out manually.
Then I thought...what if I watch for the CMD process, suspend it, extract the command line data, then kill it. Not only would I be able to get the VBA macro output quickly and easily, I would also avoid getting my machine compromised. That's how CMD Watcher was born.
I went to the Malware Traffic Analysis site and grabbed several maldocs, fired up CMD Watcher, and started to open up each document while allowing macros to run.
Looks like it's working...

Here's Emotet's maldoc.

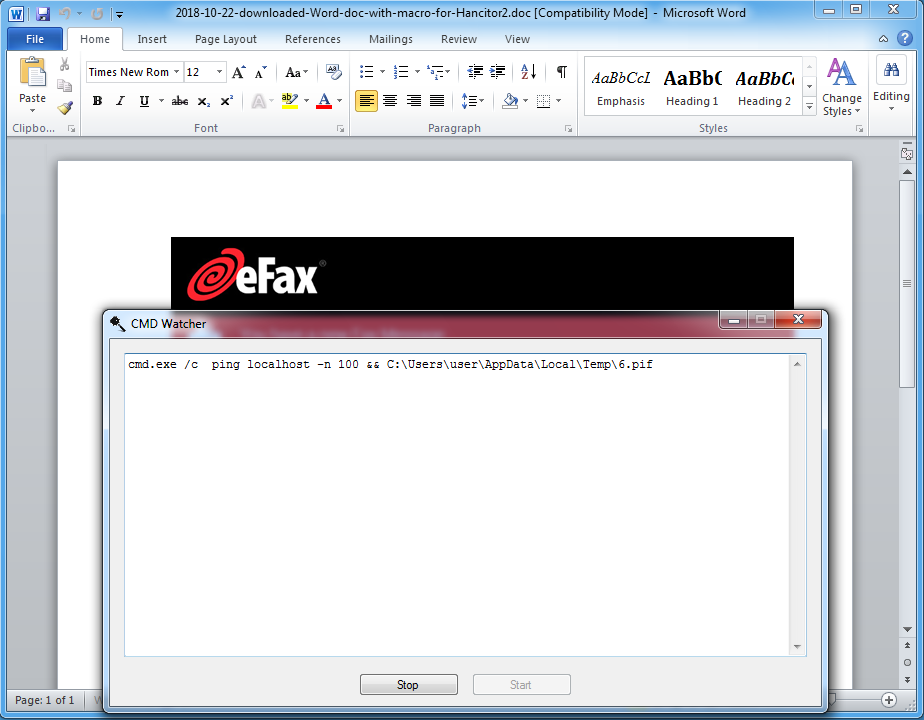
This one is Hancitor.
And here's Trickbot.

I'm now able to collect the second stage scripts with very little effort. Taking a quick look at the scripts I notice that they all use DOSfuscation. I'll write a follow-up post on how to deobfuscate DOSfuscated scripts.
If you're interested in playing with CMD Watcher, you can download it from the Tools page.

