Neosploit is Back!
After a long hiatus, it appears that Neosploit may have come back to life! While the code has some slight changes, it functions similarly to previously known versions of Neosploit so it’s doesn’t look like a major upgrade. I just can’t tell how widespread this is but I think we can all agree that it did make a pretty big impact awhile ago before Black Hole became a dominant player in the attack toolkit space.
Here’s the website that is hosting the link to the exploit pack:
The website’s source code reveals the malicious redirect script.

When you clean up the code, it looks like this:

Interestingly, the redirect script above employs a similar obfuscation method used by Neosploit. Both scripts contain a common function that decrypts strings sent to it. If you can monitor that function, you can extract the resulting script after it gets decrypted.
The redirect script above calls upon an external script which triggers the infection process. Here are the URL formats:
website/ftfpckzxwj4sg7g3/website/468cc5ed9bfac20f8b2df382c08942f83869zxwwebsite/osnp91icm/?5website/osnp91icm/?256a9d86bde5afd64251505a0c5f0e030204035a0d06080d0650575600530f03website/osnp91icm/?2ace17a0a7c1b25c5800115e040c57050250565e0555510b0604025208005605website/osnp91icm/?0ff3a2f348f12d565a120b085409500600575308555056080403070458055106If you’ve been tracking Neosploit, you’ll notice that the URL formats look familar. Here’s another familiar item, the obfuscation method:
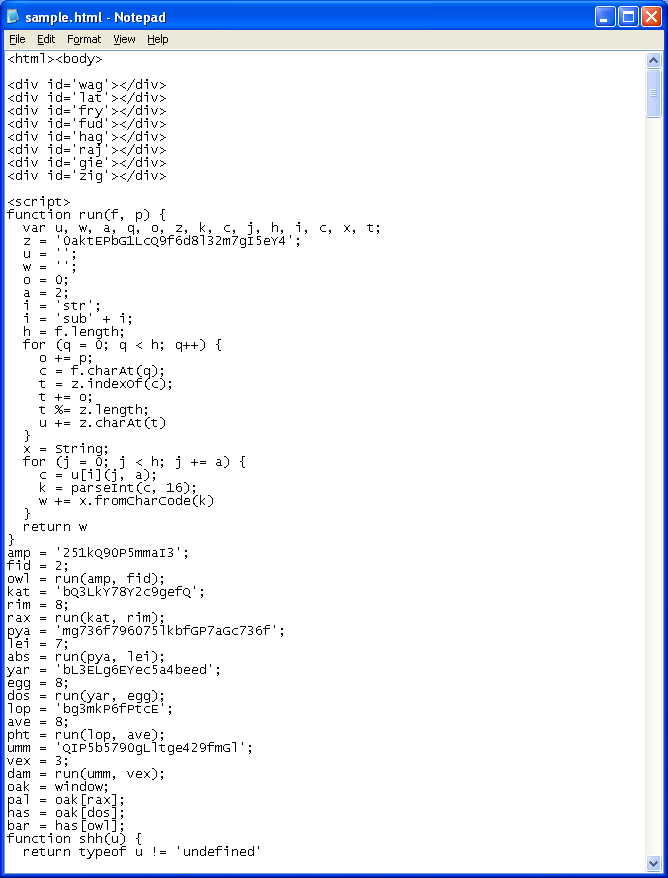
That “run” function you see is the main decryptor which is what previous versions of Neosploit was known to use. There’s slight changes here and there probably meant to get past IDS and AV. The exploits used are similar to previous versions with Java leading the way followed by Acrobat.

