Deobfuscating the CK Exploit Kit
The CK Exploit Kit has been around since 2012 and has its roots in the NetBoom Exploiter kit according to security blog site CySecTa. You can read about its history and other information here.
Output from the NB Exploiter doesn't resemble the scripts found in today's CK Exploit Kit so we're probably talking about a completely new tool. However, when you take a closer look, you will find variable names like "nbcode", "nbChar", and "nbencode" so there may be some code reuse after all.

Finding a live instance of the CK Exploit Kit these days is a somewhat of a challenge. The drive-by download appears for less than a day then the files are removed from the server. This exploit kit tends to show up on Chinese and Korean sites.
The CK Exploit Kit is definitely out of date but since it's still being used today, I thought I would document it here for my reference. I won't spend too much time digging into the kit since there's already several good write-ups including this one from KISA - Korean Internet & Security Agency.
The landing page looks like this (you will notice the text "ck" referenced in variable names in several places). The "top.js" file is a plug-in detector and mainly checks for IE and Java versions.

The Javascript is compressed using a variant of Dean Edwards' packer. You can barely make out the variables p, a, c, k, e, d in between the comment tags:

The variable "p" holds the deobfuscated value so you just need to replace "return p" with "document.write('<textarea>'+p)":

Since this script checks your cookie to make sure you only run it once, you can remove that part or just clear your browser cookies if you need to visit the page a second time. You should see a textbox containing the uncompressed script.
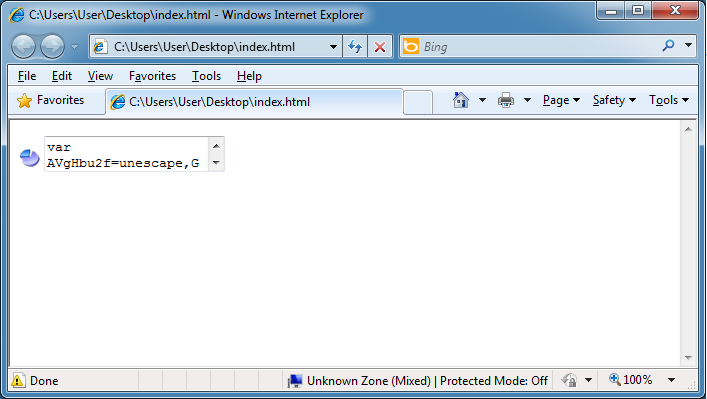
All I did here was add the "script" tags, copy the function "ckl" from the landing page back to this page, and then separated the blocks of script so I can make better sense of it. If you go through the script, you'll find that you can deobfuscate the script by modifying the function in the red block which is basically "window[document][write](t)".

Change the red block text to this: "window[X3cQCMIIF][ErTiUlaxlkP]('<textarea>'+t)" and execute the script. You will again see a small textbox with your deobfuscated script in it. Here's the final script with an interesting class name. Apparently someone didn't have a good day.

Inside one of those applets, the hilarity continues with another funny string:

Near the bottom of the landing page, the script will open one of two HTML files depending on the version of IE used to visit the page.
if(ck_wm.indexOf("msie 6")>-1){document.write("< iframe src=zip.html width=60 height=1>< /iframe>");}else if(ck_wm.indexOf("msie 7")>-1||ck_wm.indexOf("msie 8")>-1){document.write("< iframe src=win.html width=60 height=1>< /iframe>");}This zip.html page uses the same obfuscation method as the landing page:

When you deobfuscate the script, it should look something like this. This hosts the CVE-2012-1889 exploit.

The second page, win.html, calls up a Flash file which is protected with DoSWF.

By the way, it contains an interesting string "King Lich V" which may be related to PlugX based on this write-up from Jaime Blasco.

The script references an file "Moview1.html" which I wasn't able to pull down in time. Presumably this is exploiting CVE-2013-0634. The shellcode is XOR'd using the value 0xE2 which is the same as Jaime's sample from 2012.
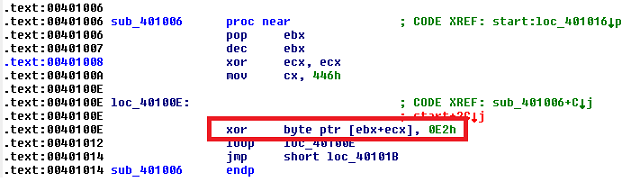
The payload file was downloaded from p.wangwangwangwangwang.com (174.139.88.102):

The payload was a Trojan that checked in at qwe.xzczxcasrafdsfzxcvzv.com:3306 (98.126.71.38).
File: logo.swf (dropper)MD5: ad760c37c4198449b81b4992a3f2d561VT: 6 / 45File: ckwm.jar (CVE-2011-3544)MD5: 4a562094a9d2771507e50faf08a6ca79VT: 8 / 46File: wmck.jar (CVE-2012-4681)MD5: 5b47778d02048bb081b122cb11367217VT: 22 / 45File: p.exeMD5: b8c0bec6b361c971a09d2b6a93692291VT: 25 / 46
